What are two examples of business goals to be considered when a network design is built? (Choose two.)
Which two advantages of using DWDM over traditional optical networks are true? (Choose two.)
A product manufacturing organization is integrating cloud services into their IT solution. The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service. What is one topic that should be considered in the Define Strategy step?
Company XYZ wants to use the FCAPS ISO standard for network management design, focusing on minimizing outages through detection, isolation, and corrective actions. Which layer accomplishes this design requirement?
Refer to the exhibit.

The enterprise customer wants to stream one-way video from their head office to eight branch offices using multicast. Their current service provider provides a Layer 3 VPN solution and manages the CE routers, but they do not currently support multicast. Which solution quickly allows this multicast traffic to go through while allowing for future scalability?
Customer XYZ network consists of an MPLS core, IS-IS running as IGP, a pair of BGP route reflectors for route propagation, and a few dozen MPLS-TE tunnels for specific tactical traffic engineering requirements. The customer's engineering department has some questions about the use of the Overload Bit in the IS-IS networks and how it could be used to improve their current network design. Which two concepts about the Overload Bit are true? (Choose two.)
Which two pain points are the most common for container technology adoption? (Choose two)
Refer to the table.
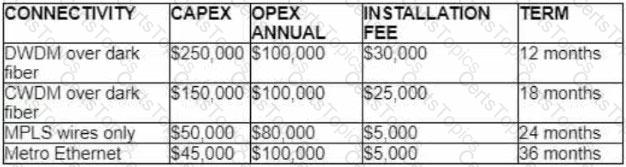
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
Which technology supports antispoofing and does not have any impact on encryption performance regardless of packet size?
Company XYZ runs OSPF in their network. A design engineer decides to implement hot-potato routing architecture. How can this implementation be achieved?
Company XYZ, a global content provider, owns data centers on different continents. Their data center design involves a standard three-layer design with a Layer 3-only core. HSRP is used as the FHRP. They require VLAN extension across access switches in all data centers, and they plan to purchase a Layer 2 interconnection between two of their data centers in Europe. In the absence of other business or technical constraints, which termination point is optimal for the Layer 2 interconnection?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
As part of a new network design documentation, you are required to explain the reason for choosing Cisco FabricPath for Layer 2 loop avoidance.
Which two elements help Cisco FabricPath mitigate Layer 2 loops if they happen in the Layer 2 MP network? (Choose two)
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
Refer to the diagram.
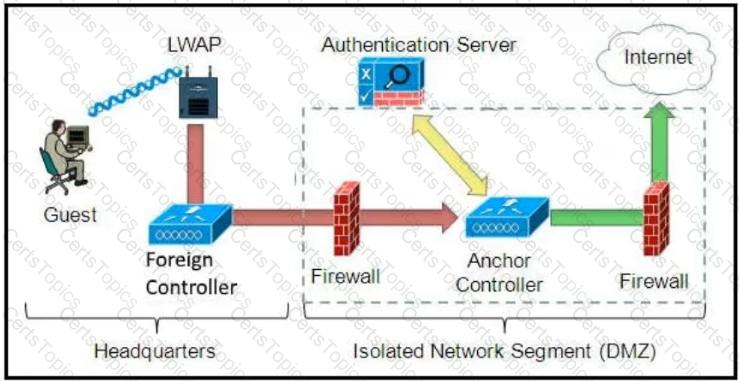
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
An external edge router provides connectivity from a service provider to an enterprise. Which two Internet edge best practices meet compliance regulations? (Choose two)
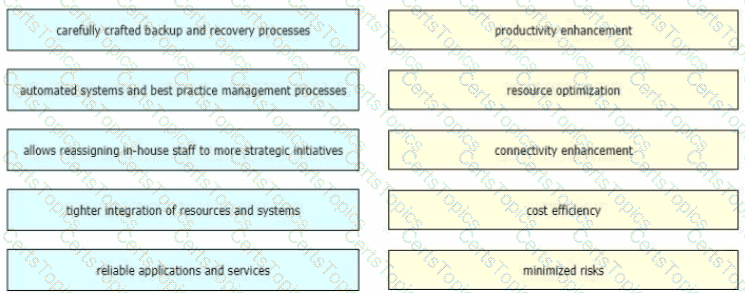
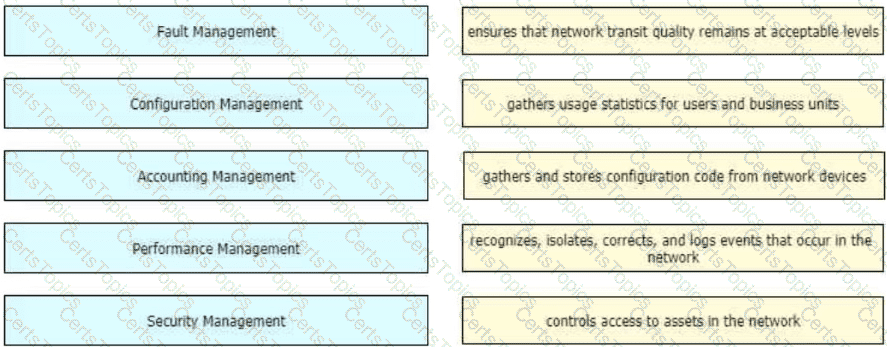
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
An enterprise requires MPLS-connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access is available only at dual regional hub sites that are connected to the MPLS network. Which connectivity method provides an optimum access method to the cloud-based services if one ISP suffers loss or latency?
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection. Which technology meets the updated requirements and can be incorporated into the design?
The major business applications of an enterprise are largely monolithic and hard-coded. As part of a major modernization and overhaul of the applications, the goal is to move to a modular and containerized application architecture model. At the same time, decoupling from the hardware is desired to move to an on-demand provisioning. However, the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
An enterprise network has two core routers that connect to 200 distribution routers and uses full-mesh IBGP peering between these routers as its routing method. The distribution routers are experiencing high CPU utilization due to the BGP process. Which design solution is the most cost effective?
While designing a switched topology, in which two options is UplinkFast recommended? (Choose two.)
Which main IoT migration aspect should be reviewed for a manufacturing plant?
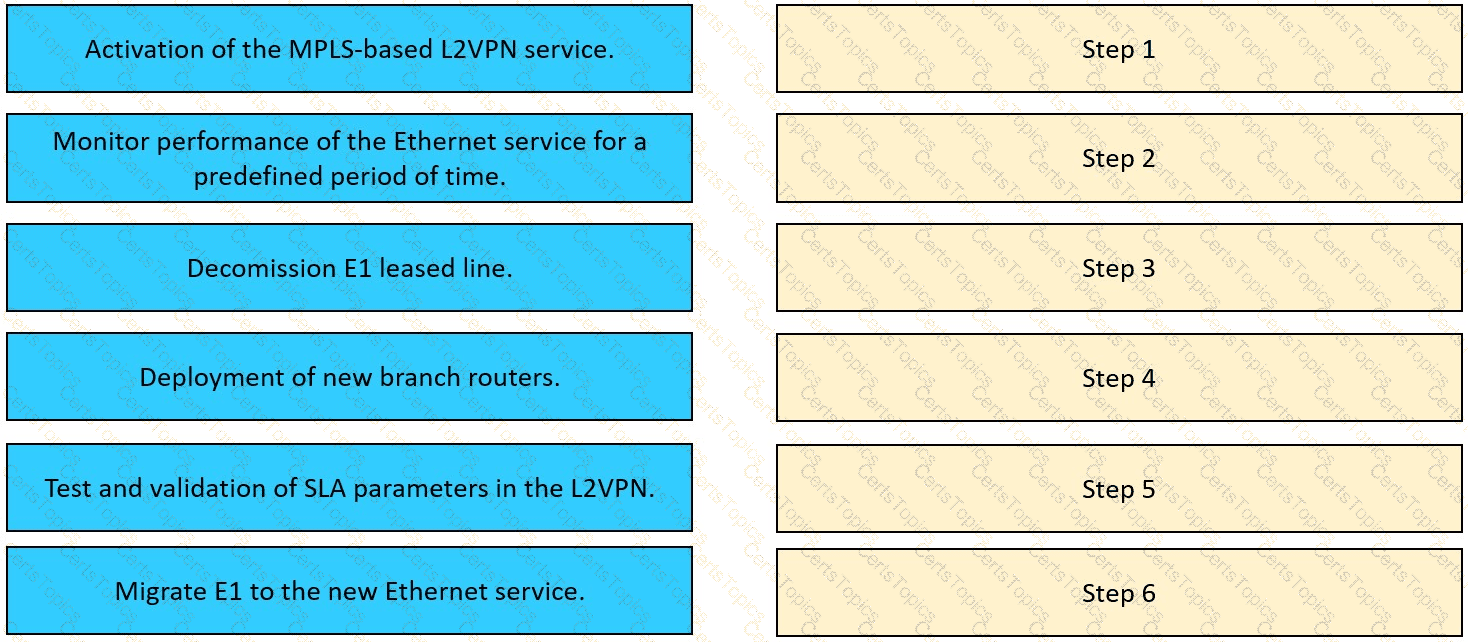
The network team in XYZ Corp wants to modernize their infrastructure and is evaluating an implementation and migration plan to allow integration MPLS-based, Layer 2 Ethernet services managed by a service provider to connect branches and remote offices. To decrease OpEx and improve
response times when network components fail, XYZ Corp decided to acquire and deploy new routers. The network currently is operated over E1 leased lines (2 Mbps) with a managed CE service provided by the telco.
Drag and drop the implementation steps from the left onto the corresponding targets on the right in the correct order.
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
Which management category is not part of FCAPS framework?
A service provider recently migrated to an SD-WAN solution for delivering WAN connections to its customers. One of the main challenges with the SD-WAN deployment is that branch site volume increases every year, which causes management complexity. Which action resolves the issue?
Retef to the exhibit.
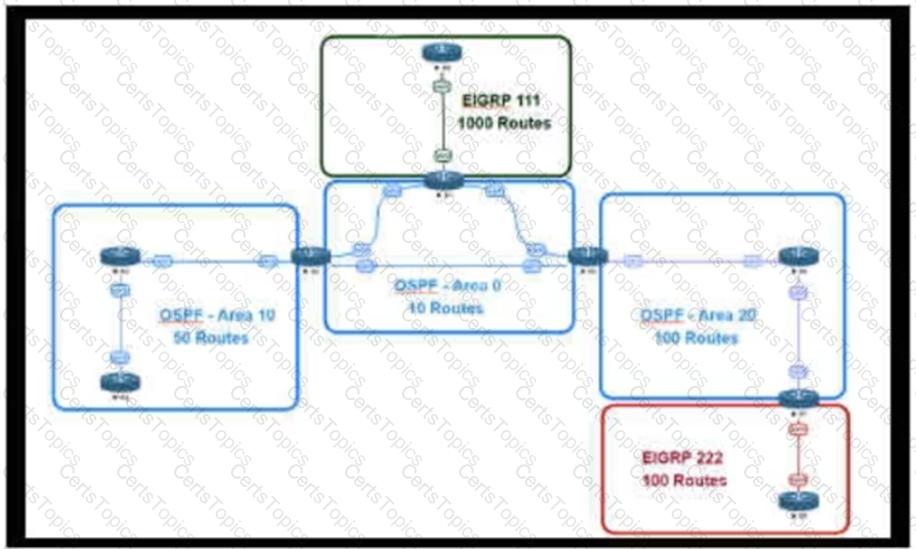
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain. EIGRP routes are getting redistributed into OSPF. OSPF area 20 has routers with limited memory and CPU resources. The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to flow in. Which OSPF area type fulfills this design requirement?
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two.)
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
As a network designer, you need to support an enterprise with hundreds of remote sites connected over a single WAN network that carries different types of traffic, including VoIP, video, and data applications. Which of the following design considerations will not impact design decision?
As network designer, which option is your main concern with regards to virtualizing multiple network zones into a single hardware device?
Company ABC uses IPv4-only. Recently they started deploying new endpoint devices. For operational reasons, IPv6 cannot be disabled on these new endpoint devices. Which security measure prevents the new endpoint from learning an IPv6 prefix from an attacker?
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
Which two points must network designers consider when designing a new network design or when evaluating an existing network design to help them understand the high-level design direction with regards to the security aspects? (Choose two)
Which component of the SDN architecture automatically ensures that application traffic is routed according to policies established by network administrators?
Hybrid cloud computing allows organizations to take advantage of public and private cloud models. Which best practice should organizations follow to ensure data security in the private cloud?
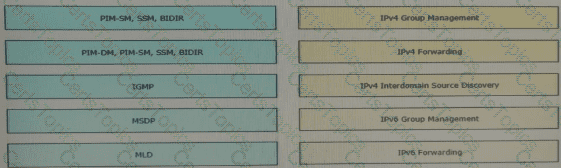
Drag and drop the multicast protocols from the left onto the current design situation on the right.
Refer to the exhibit.
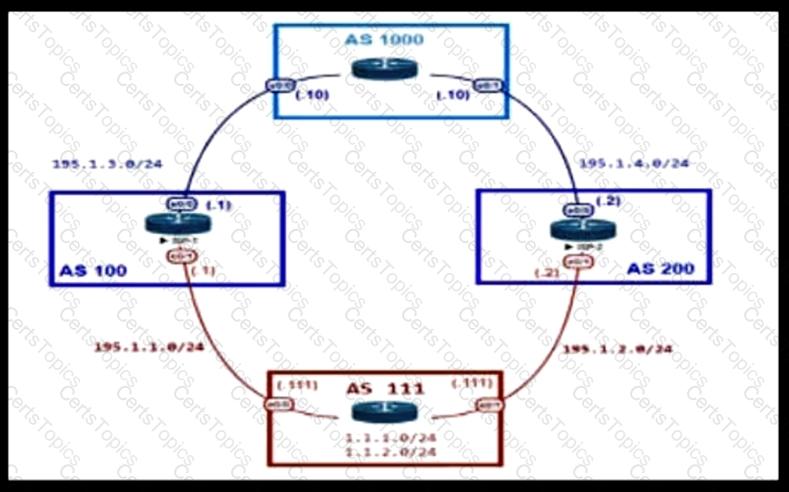
An engineer is designing the network for a multihomed customer running in AS 111. The AS does not have any other ASs connected to it. Which technology is more comprehensive to use in the design to make sure that the AS is not being used as a transit AS?
Over the years, many solutions have been developed to limit control plane state which reduces the scope or the speed of control plane information propagation. Which solution removes more specific information about a particular destination as topological distance is covered in the network?
Which feature is supported by NETCONF but is not supported by SNMP?
An enterprise plans to evolve from a traditional WAN network to a software-defined WAN network. The existing devices have limited capability when it comes to virtualization. As the migration is carried out, enterprise applications and services must not experience any traffic impact. Which implementation plan can be used to accommodate this during the migration phase?
You are designing an Out of Band Cisco Network Admission Control Layer 3 Real-IP Gateway deployment for a customer. Which VLAN must be trunked back to the Clean Access Server from the access switch?
What are two top cloud-native security challenges faced by today's cloud-oriented organizations? (Choose two.)
What are two descriptions of network optimization? (Choose two.)
Which function is performed at the access layer of the three-layer hierarchical network design model?
Your network operations team is deploying Access Control Lists (ACLs) across your Internet gateways. They wish to place an ACL inbound on the Internet gateway interface facing the core network (the "trusted" interface). Which IP address would the ACL need for traffic sourced from the inside interface, to match the source address of the traffic?
Company XYZ has 30 sites using MPLS L3 VPN and is concerned about data integrity. They want a centralized configuration model and minimal overhead. Which technology can be used?
What is the most important operational driver when building a resilient and secure modular network design?
An enterprise campus is adopting a network virtualization design solution with these requirements:
• It must include the ability to virtualize the data plane and control plane by using VLANs and VRFs
• It must maintain end-to-end logical path transport separation across the network
• Resources available grouped at the access edge
Which two primary models can this network virtualization design be categorized? (Choose two)
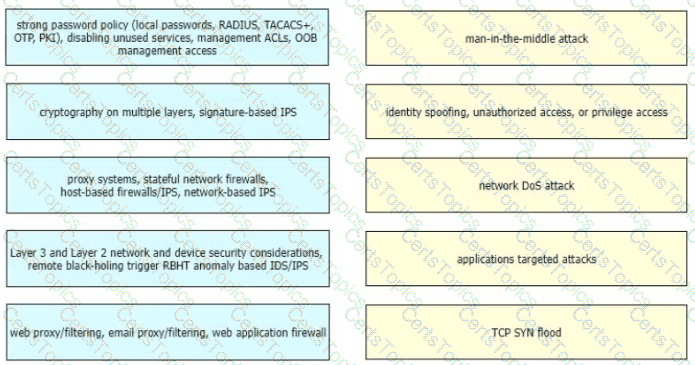
Drag and drop the correct mitigation methods from the left onto the corresponding types of attack on the right
Which mechanism provides Layer 2 fault isolation between data centers?
Company XYZ wants to prevent switch loops caused by unidirectional point-to-point link conditions on Rapid PVST+ and MST. Which technology can be used in the design to meet this requirement?
SD-WAN can be used to provide secure connectivity to remote offices, branch offices, campus networks, data centers, and the cloud over any type of IP-based underlay transport network. Which two statements describe SD-WAN solutions? (Choose two.)
Refer to the exhibit.
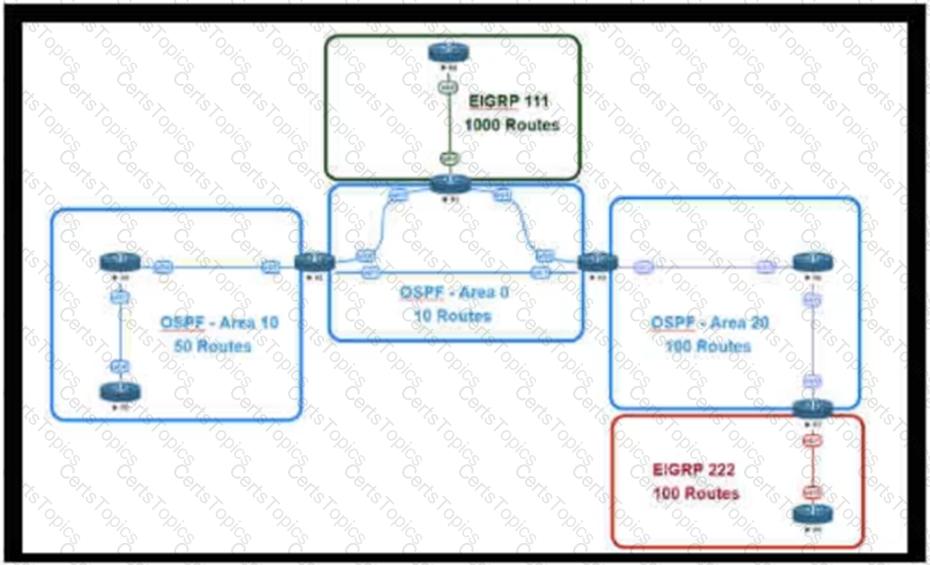
This network is running OSPF and EIGRP as the routing protocols. Mutual redistribution of the routing protocols has been configured on the appropriate ASBRs. The OSPF network must be designed so that flapping routes in EIGRP domains do not affect the SPF runs within OSPF. The design solution must not affect the way EIGRP routes are propagated into the EIGRP domains. Which technique accomplishes the requirement?
You are a network designer and you must ensure that the network you design is secure. How do you plan to prevent infected devices on your network from sourcing random DDoS attacks using forged source addresses?
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
An existing wireless network was designed to support data traffic only. You must now install context-aware services for location tracking. What changes must be applied to the existing wireless network to increase the location accuracy? (Choose two)
In search of a system capable of hosting, monitoring, compiling, and testing code in an automated way, what can be recommended to the organization?
What is the most important operational driver in building a resilient and secure modular network design?
Which two possible drawbacks should you consider when introducing Network Functions Virtualization in a network design? (Choose two.)
Which two descriptions of CWDM are true? (Choose two)
Backups and mirror copies of data are part of RPO (Recovery Point Objective) strategies. If a business wants to reduce their CAPEX for disaster recovery, which solution is most applicable?
What is a web-based model in which a third-party provider hosts applications that are available to customers over the Internet?
Which undesired effect of increasing the jitter compensation buffer is true?
A Tier-3 Service Provider is evolving into a Tier-2 Service Provider due to the amount of Enterprise business it is receiving. The network engineers are re-evaluating their IP/MPLS design considerations in order to support duplicate/overlapping IP addressing from their Enterprise customers within each Layer3 VPN. Which concept would need to be reviewed to ensure stability in their network?
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
Which methodology is the leading lifecycle approach to network design and implementation?
While reviewing an existing network design, you are discussing the characteristics of different STP versions. Which protocol minimizes unicast flooding during a Topology Change Notification in a Layer 2 switched network with many VLANs?
Software-defined networking architecture is used for cost-effective, adaptable, and easily manageable applications. In which two software-defined networks is SDN commonly used? (Choose two.)
During a pre-sales meeting with a potential customer, the customer CTO asks a question about advantages of controller-based networks versus a traditional network. What are two advantages to mention? (Choose two)
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Which two actions must merchants do to be compliant with the Payment Card Industry Data Security Standard (PCI DSS)? (Choose two.)
QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
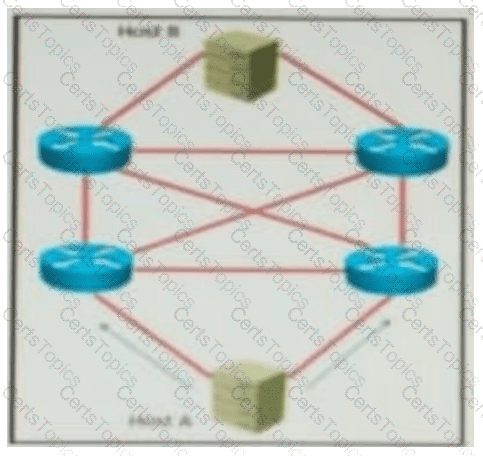
Refer to the exhibit. All links are P2P Layer 3. A high availability application is synchronizing data between Host A and Host B. To increase the chance of delivery, the same data is sent twice from Host A on two different NICs toward the two NICs on Host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on Host B?
Refer to the exhibit.
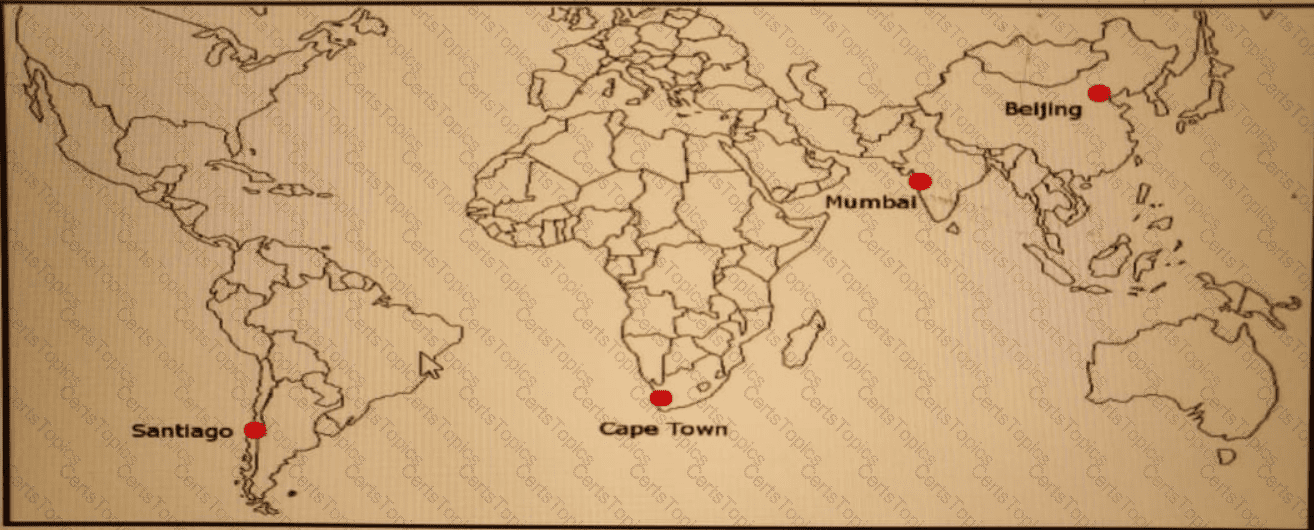
ACME Mining has four data centers in Santiago. Cape Town. Mumbai, and Beijing, full-mesh connected via a 400 Mb/s EVP-LAN They want to deploy a new mission-critical application with these
requirements:
clusterheartbeat2Mb/s continuous (250 KB/s)
cluster heartbeat one-way maximum latency 100 ms
These are the current ping tests results between the four data centers:
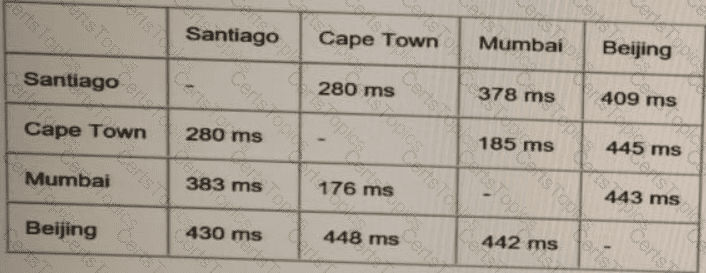
Which hosting data center pair can host the new application?
An engineer is designing the QoS strategy for Company XYZ. A lot of scavenger traffic is traversing the 20Mb Internet link. The new design must limit scavenger traffic to 2 Mbps to avoid oversubscription during congestion. Which QoS technique can be used?
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
Refer to the exhibit.
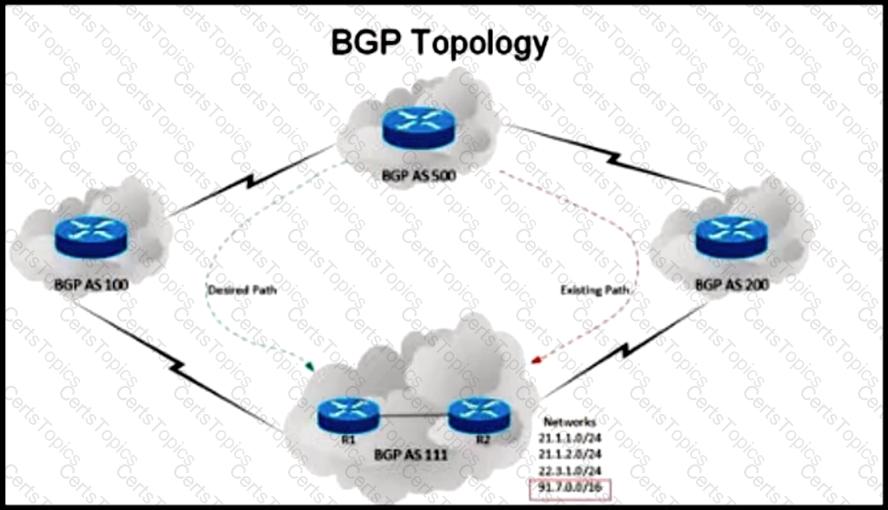
An engineer has been asked to redesign the traffic flow toward AS 111 coming from AS 500. Traffic destined to AS 111 network 91.7.0.0/16 should come in via AS 100, while traffic destined to all other networks in AS 111 should continue to use the existing path. Which BGP attributes are best suited to control this inbound traffic coming from BGP AS 500 into the 91.7.0.0/16 network?
Refer to the exhibit.
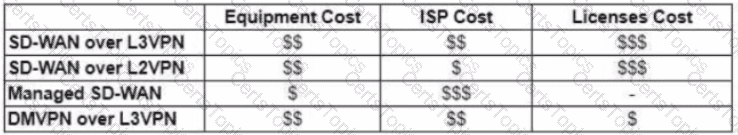
The WAN network of the General Bank of Greece has experienced several outages. It takes too long to activate a new branch site. The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible, manageable, and scalable in-house solution. The number of branches will increase exponentially in the next fiscal year. The CTO states that the bank’s main goal is OPEX reduction. The network engineering team prepares a table to evaluate the available options. Which WAN technology can be used for the solution?
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?
Which encoding format does Cisco IOS XE software support for NETCONF?
Refer to the exhibit.
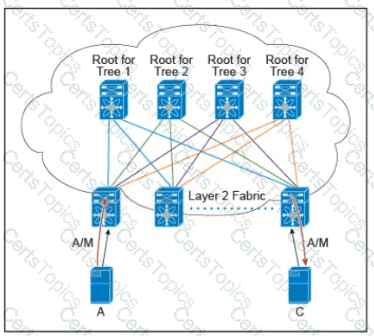
There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two.)
Drag and drop the end-to-end network virtualization elements from the left onto the correct network areas on the right.
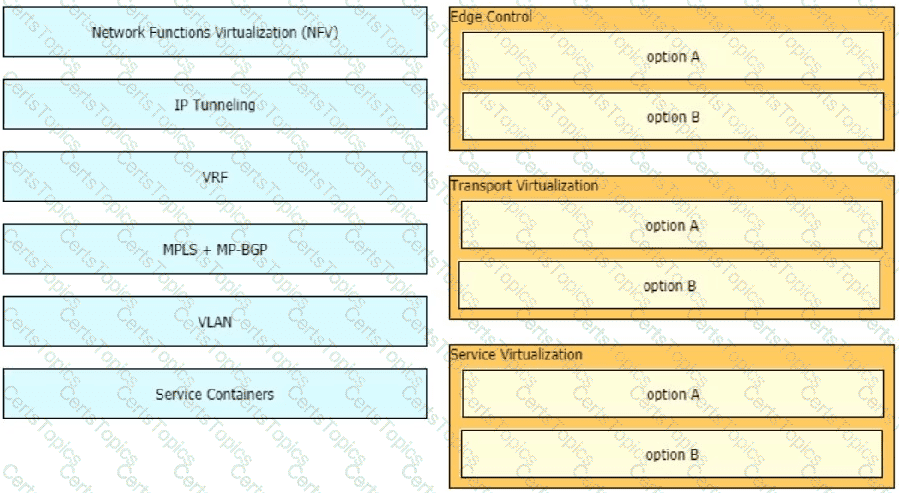
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
Refer to the exhibit.
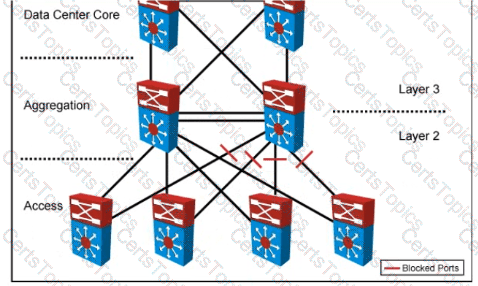
Your company designed a network to allow server VLANs to span all access switches in a data center. In the design, Layer 3 VLAN interfaces and HSRP are configured on the aggregation switches. Which two features improve STP stability within the network design? (Choose two.)
Which design benefit of PortFast is true?
What is a disadvantage of the traditional three-tier architecture model when east-west traffic between different pods must go through the distribution and core layers?
Which two conditions must be met for EIGRP to maintain an alternate loop-free path to a remote network? (Choose two.)
A consultant needs to evaluate project management methodologies for a new service deployment on the existing network of a customer. The customer wants to be involved in the end-to-end project progress and be provided with frequent updates. The customer also wants the ability to change the requirements if needed, as the project progresses. Which project management methodology should be used?
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
Refer to the exhibit.
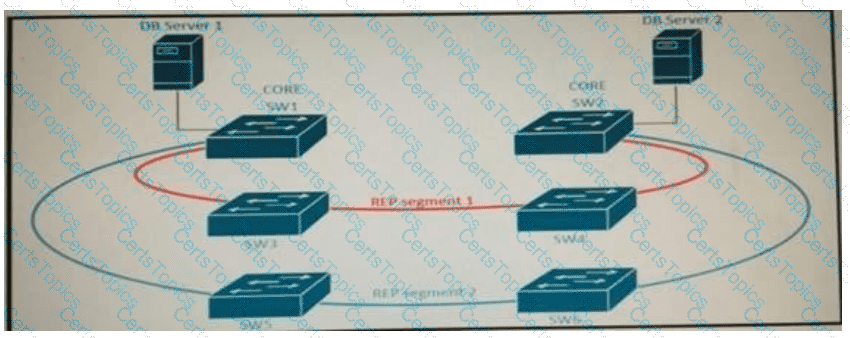
Refer to the exhibit. A new high availability DB server cluster is installed in the network. These two servers require high bandwidth and low latency Layer 2 connectivity for database replication.
Which solution supports these requirements?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
Which parameter is the most important factor to consider when deciding service placement in a cloud solution?
Which service abstracts away the management of the operating system, middleware, and runtime?
As technologies such as big data, cloud, and loT continue to grow, so will the demand for network bandwidth Business strategies must be flexible to accommodate these changes when it comes to priorities and direction and the network design strategy also must be agile and adaptable Drag and drop the benefits from the left onto the corresponding strategic approaches on the right as they relate to network design and management.