A penetration tester executes the following Nmap command and obtains the following output:
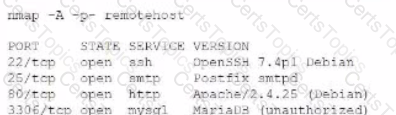
Which of the following commands would best help the penetration tester discover an exploitable service?
A)
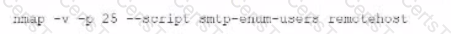
B)
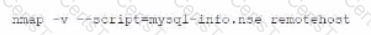
C)
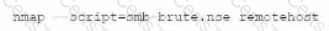
D)
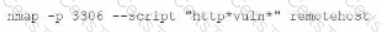
During a penetration test of a server application, a security consultant found that the application randomly crashed or remained stable after opening several simultaneous connections to the application and always submitting the same packets of data. Which of the following is the best sequence of steps the tester should use to understand and exploit the vulnerability?
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
Given the following Nmap scan command:
[root@kali ~]# nmap 192.168.0 .* -- exclude 192.168.0.101
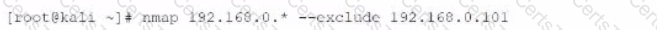
Which of the following is the total number of servers that Nmap will attempt to scan?