This TCP flag instructs the sending system to transmit all buffered data immediately.
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
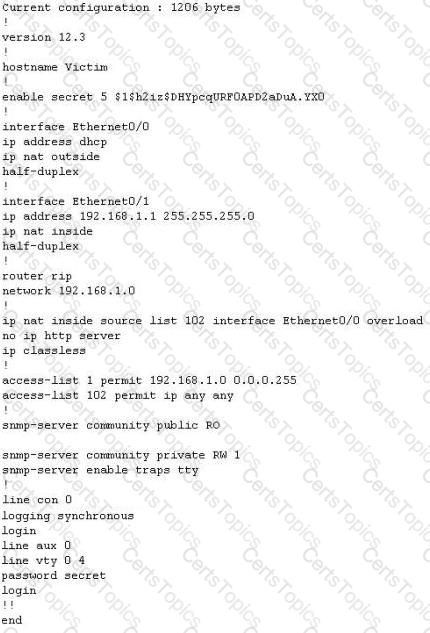
You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
Identify SQL injection attack from the HTTP requests shown below:
Which of the following encryption is NOT based on block cipher?