Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three)
The follows is an email header. What address is that of the true originator of the message?
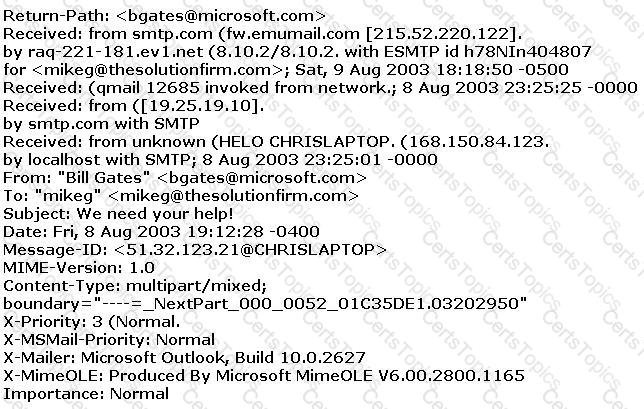
Assuring two systems that are using IPSec to protect traffic over the internet, what type of general attack could compromise the data?
Which of the following tools are used for enumeration? (Choose three.)