Global deployment of RFC 2827 would help mitigate what classification of attack?
In the context of Windows Security, what is a 'null' user?
Exhibit:
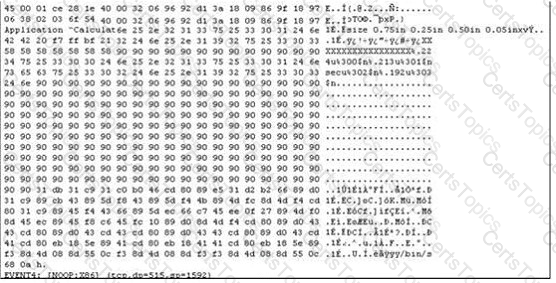
The following is an entry captured by a network IDS.You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP instruction for the Intel processor. You figure that the attacker is attempting a buffer overflow attack. You also notice "/bin/sh" in the ASCII part of the output. As an analyst what would you conclude about the attack?
Which tool would be used to collect wireless packet data?