ECCouncil Related Exams
EC0-350 Exam







This type of Port Scanning technique splits TCP header into several packets so that the packet filters are not able to detect what the packets intends to do.
Bob is doing a password assessment for one of his clients. Bob suspects that security policies are not in place. He also suspects that weak passwords are probably the norm throughout the company he is evaluating. Bob is familiar with password weaknesses and key loggers.
Which of the following options best represents the means that Bob can adopt to retrieve passwords from his clients hosts and servers?
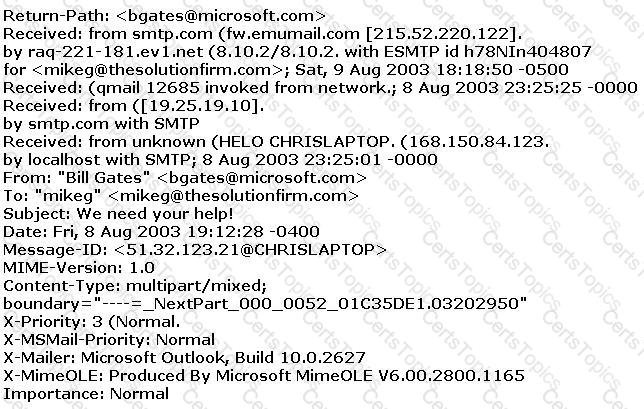
The follows is an email header. What address is that of the true originator of the message?