You have hidden a Trojan file virus.exe inside another file readme.txt using NTFS streaming.
Which command would you execute to extract the Trojan to a standalone file?
Which of the following is the primary objective of a rootkit?
Study the snort rule given below:
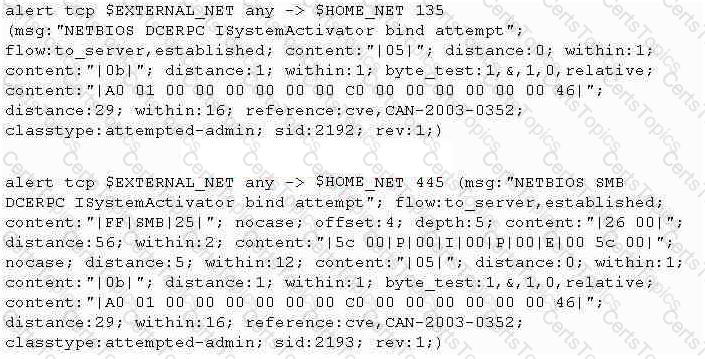
From the options below, choose the exploit against which this rule applies.
What is GINA?