Refer to the scenario.
An organization wants the AOS-CX switch to trigger an alert if its RADIUS server (cp.acnsxtest.local) rejects an unusual number of client authentication requests per hour. After some discussions with other Aruba admins, you are still not sure how many rejections are usual or unusual. You expect that the value could be different on each switch.
You are helping the developer understand how to develop an NAE script for this use case.
You are helping a customer define an NAE script for AOS-CX switches. The script will monitor statistics from a RADIUS server defined on the switch. You want to future proof the script by enabling admins to select a different hostname or IP address for the monitored RADIUS server when they create an agent from the script.
What should you recommend?
A company has Aruba gateways and wants to start implementing gateway IDS/IPS. The customer has selected Block for the Fail Strategy.
What might you recommend to help minimize unexpected outages caused by using this particular fall strategy?
Refer to the scenario.
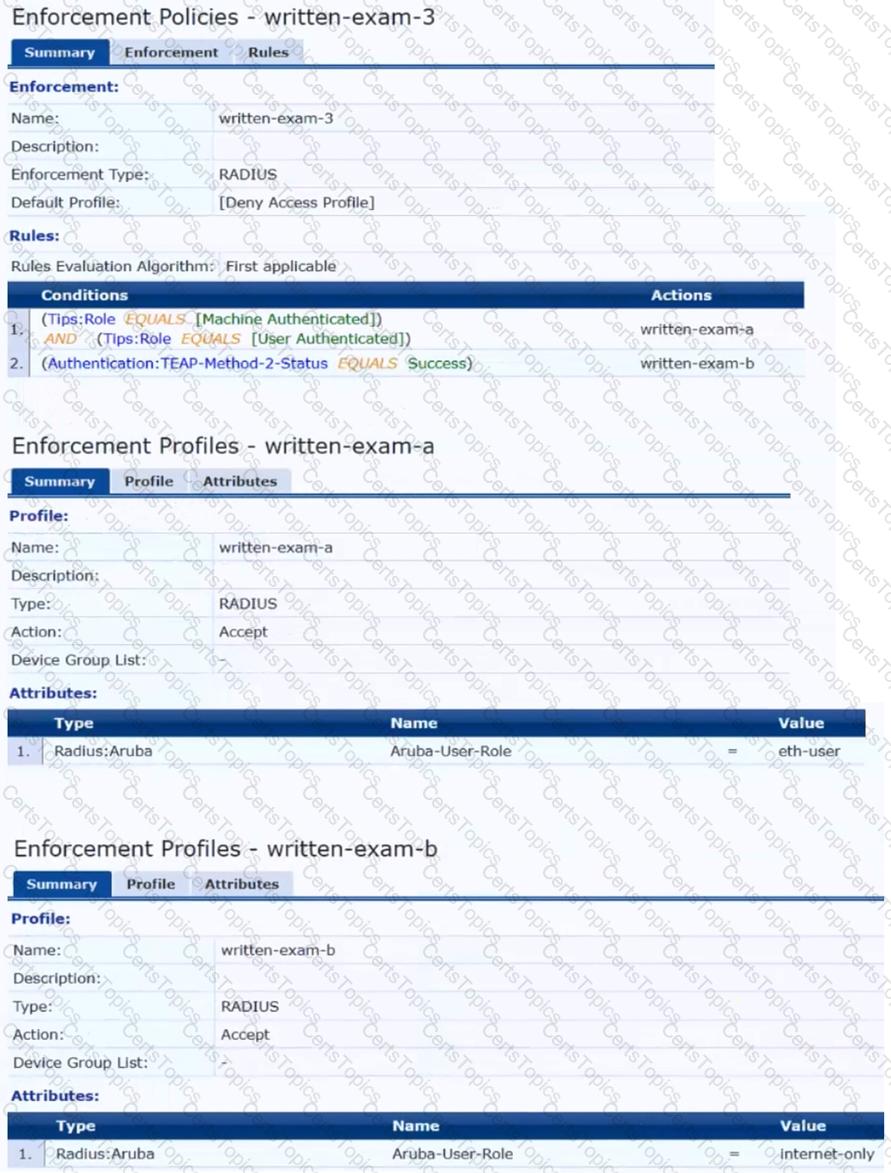
A customer has an Aruba ClearPass cluster. The customer has AOS-CX switches that implement 802.1X authentication to ClearPass Policy Manager (CPPM).
Switches are using local port-access policies.
The customer wants to start tunneling wired clients that pass user authentication only to an Aruba gateway cluster. The gateway cluster should assign these clients to the “eth-internet" role. The gateway should also handle assigning clients to their VLAN, which is VLAN 20.
The plan for the enforcement policy and profiles is shown below:
The gateway cluster has two gateways with these IP addresses:
• Gateway 1
o VLAN 4085 (system IP) = 10.20.4.21
o VLAN 20 (users) = 10.20.20.1
o VLAN 4094 (WAN) = 198.51.100.14
• Gateway 2
o VLAN 4085 (system IP) = 10.20.4.22
o VLAN 20 (users) = 10.20.20.2
o VLAN 4094 (WAN) = 198.51.100.12
• VRRP on VLAN 20 = 10.20.20.254
The customer requires high availability for the tunnels between the switches and the gateway cluster. If one gateway falls, the other gateway should take over its tunnels. Also, the switch should be able to discover the gateway cluster regardless of whether one of the gateways is in the cluster.
What is one change that you should make to the solution?
Refer to the scenario.
This customer is enforcing 802.1X on AOS-CX switches to Aruba ClearPass Policy Manager (CPPM). The customer wants switches to download role settings from CPPM. The “reception-domain” role must have these settings:
— Assigns clients to VLAN 14 on switch 1, VLAN 24 on switch 2, and so on.
— Filters client traffic as follows:
— Clients are permitted full access to 10.1.5.0/24 and the Internet
— Clients are denied access to 10.1.0.0/16
The switch topology is shown here:
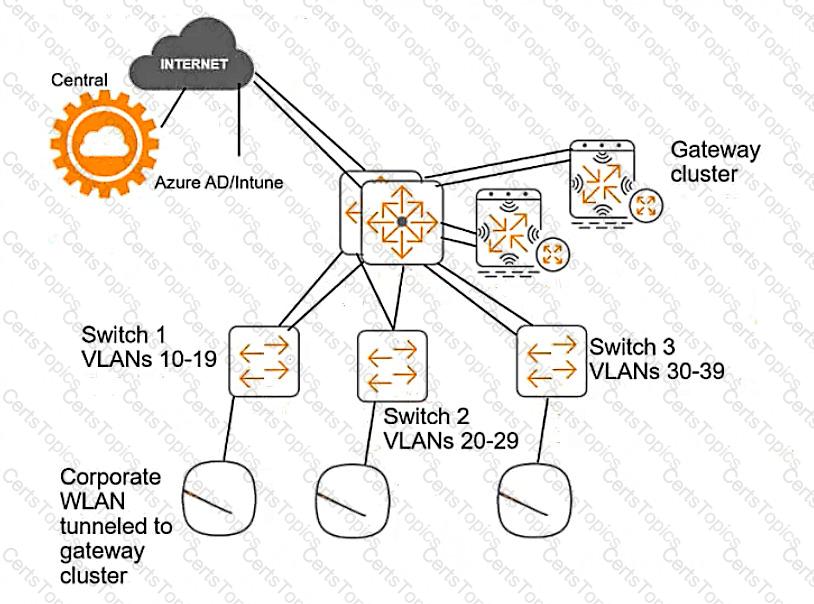
How should you configure the VLAN setting for the reception role?