CyberArk Related Exams
SECRET-SEN Exam







What is the most maintenance-free way to ensure a Conjur host’s access reflects any changes made to accounts in a safe in the CyberArk vault?
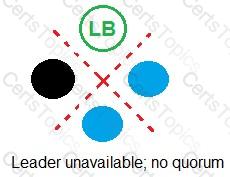
Refer to the exhibit.
In which example will auto-failover occur?

A)

B)
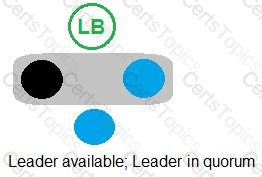
C)
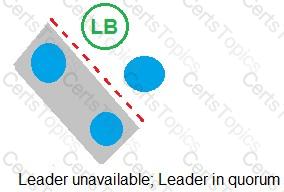
D)