Where can all the self-signed/imported certificates be found in Conjur?
When attempting to retrieve a credential managed by the Synchronizer, you receive this error:
What is the cause of the issue?
Followers are replications of the Leader configured for which purpose?
What is the most maintenance-free way to ensure a Conjur host’s access reflects any changes made to accounts in a safe in the CyberArk vault?
When installing the CCP and configuring it for use behind a load balancer, which authentication methods may be affected? (Choose two.)
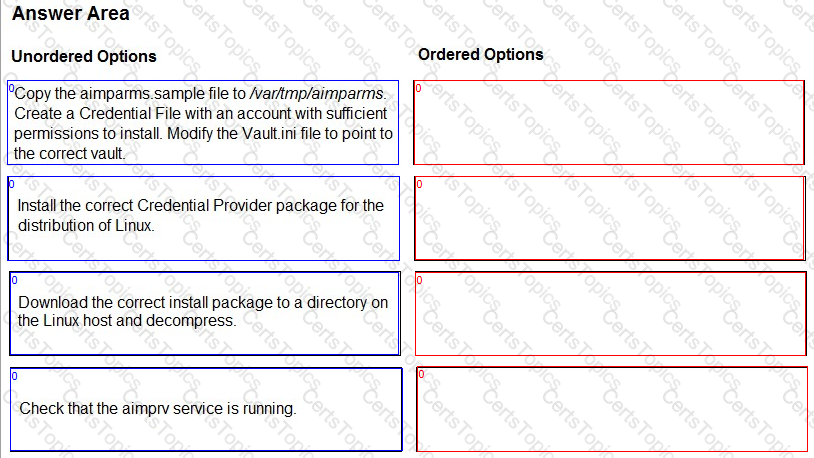
You are installing a Credential Provider on a Linux host. Arrange the installation steps in the correct sequence.
A customer wants to minimize the Kubernetes application code developers must change to adopt Conjur for secrets access.
Which solutions can meet this requirement? (Choose two.)
When working with Summon, what is the purpose of the secrets.yml file?
An application is having authentication issues when trying to securely retrieve credential’s from the Vault using the CCP webservices RESTAPI. CyberArk Support advised that further debugging should be enabled on the CCP server to output a trace file to review detailed logs to help isolate the problem.
What best describes how to enable debug for CCP?
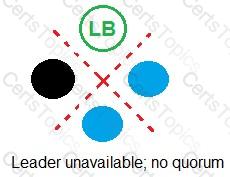
Refer to the exhibit.
In which example will auto-failover occur?

A)

B)
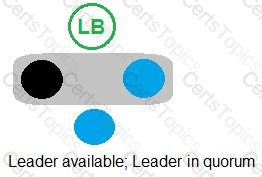
C)
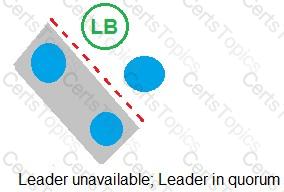
D)
If you rename an account or Safe, the Vault Conjur Synchronizer recreates these accounts and safes with their new name and deletes the old accounts or safes.
What does this mean?
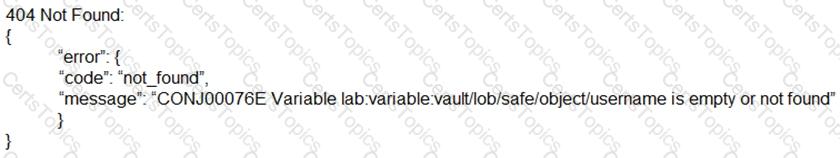
While troubleshooting an issue with accounts not syncing to Conjur, you see this in the log file:

What could be the issue?
How many Windows and Linux servers are required for a minimal Conjur deployment that integrates with an existing CyberArk PAM Vault environment, supports high availability, and is redundant across two geographically disparate regions?
You are enabling synchronous replication on Conjur cluster.
What should you do?
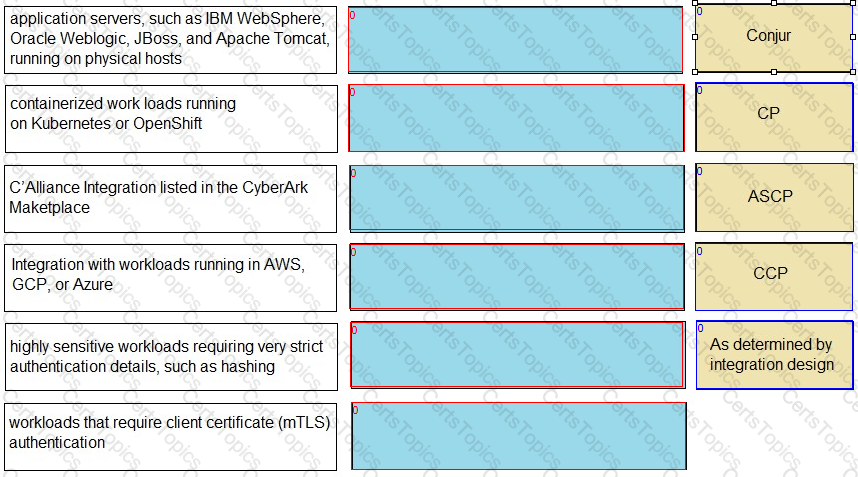
Match each use case to the appropriate Secrets Manager Solution.
Which statement is true for the Conjur Command Line Interface (CLI)?
A customer has 100 .NET applications and wants to use Summon to invoke the application and inject secrets at run time.
Which change to the NET application code might be necessary to enable this?