Which of the following relationship is used to describe security use case scenario?
Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
Which of the following authentication mechanism does J2EE support?
James is a Java developer working INFR INC. He has written Java code to open a file, read it line by line and display its content in the text editor. He wants to ensure that any unhandled exception raised by the code should automatically close the opened file stream. Which of the following exception handling block should he use for the above purpose?
Identify the formula for calculating the risk during threat modeling.
Which of the following state management method works only for a sequence of dynamically generated forms?
Which of the following can be derived from abuse cases to elicit security requirements for software system?
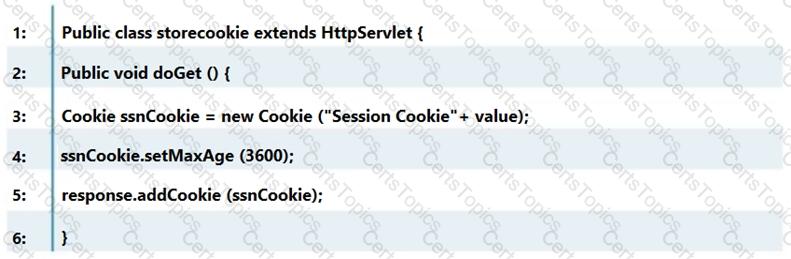
Which line of the following example of Java Code can make application vulnerable to a session attack?
In which phase of secure development lifecycle the threat modeling is performed?
Jacob, a Security Engineer of the testing team, was inspecting the source code to find security vulnerabilities.
Which type of security assessment activity Jacob is currently performing?
Which of the threat classification model is used to classify threats during threat modeling process?
To enable the struts validator on an application, which configuration setting should be applied in the struts validator configuration file?
The software developer has implemented encryption in the code as shown in the following screenshot.
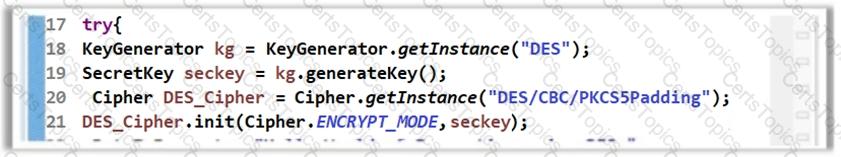
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?