


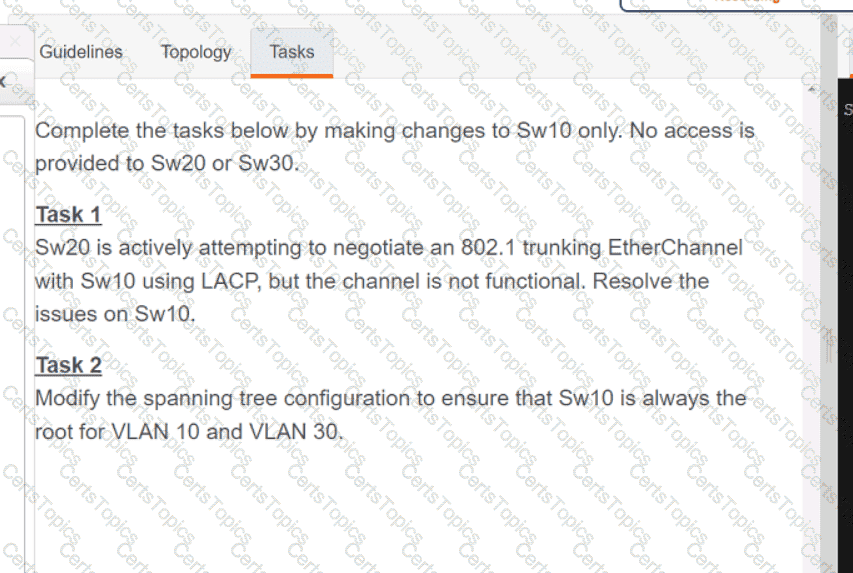

OR

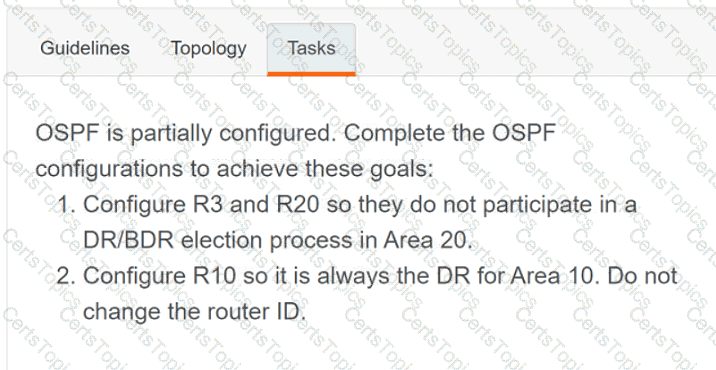
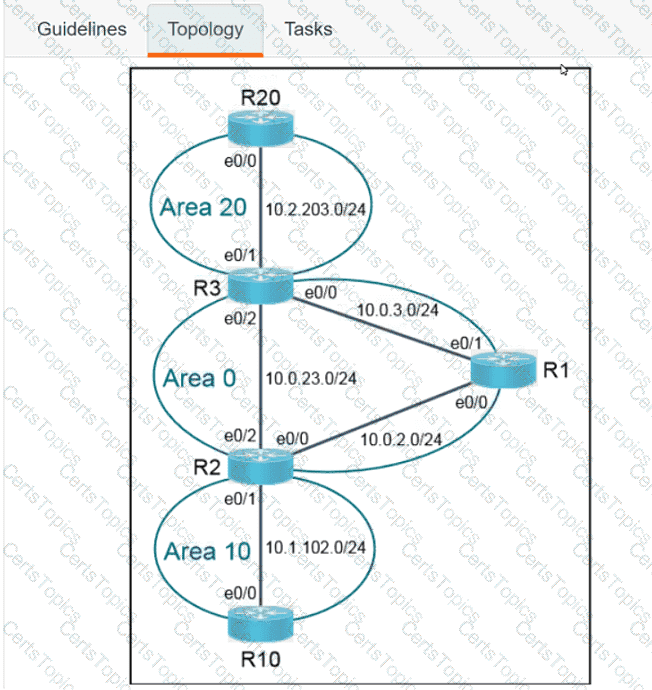
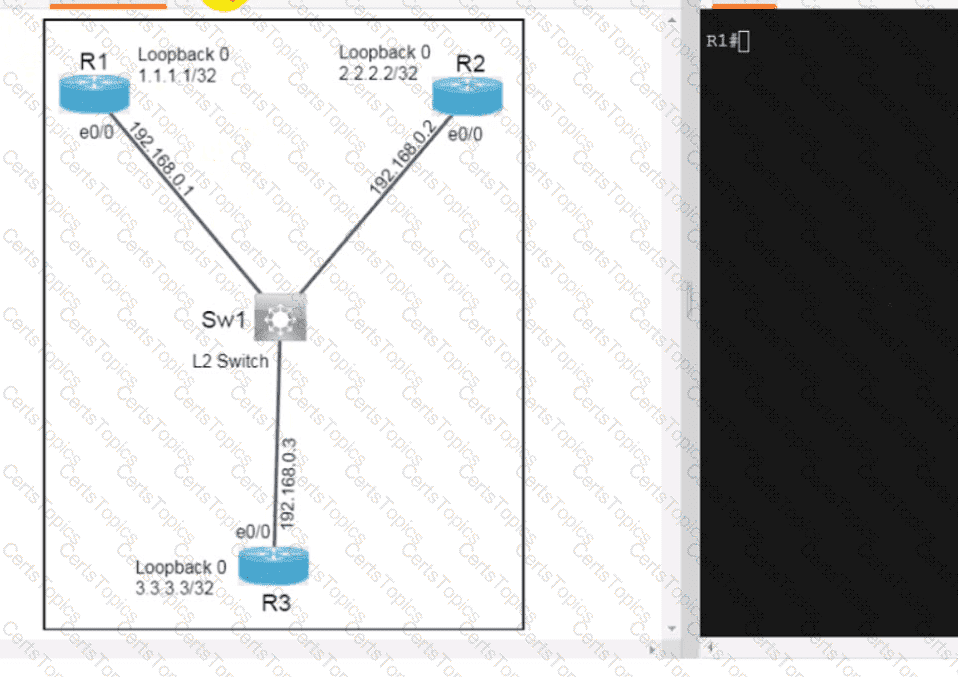
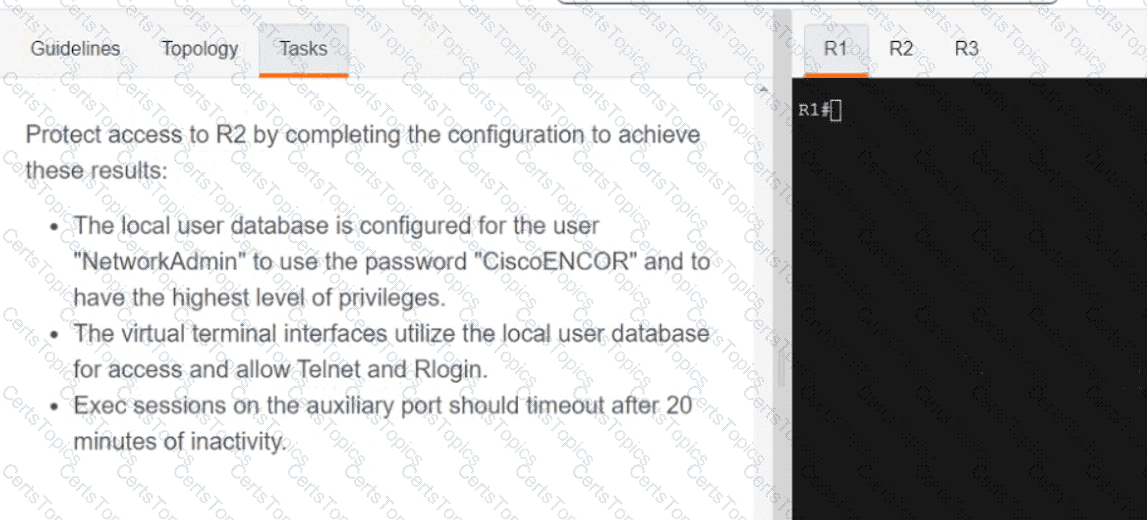
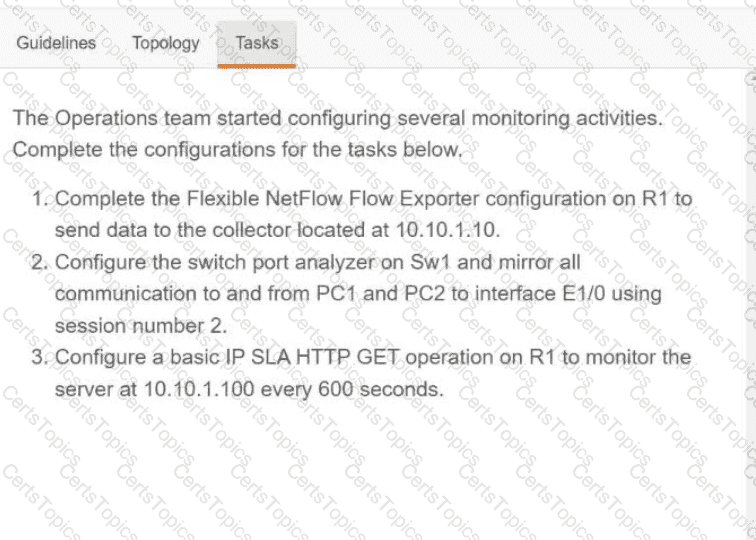
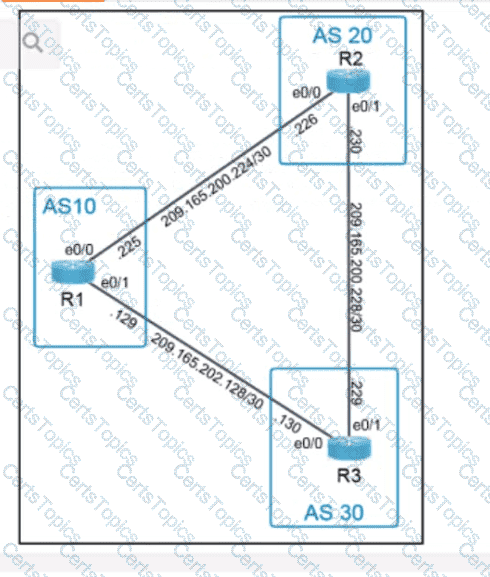
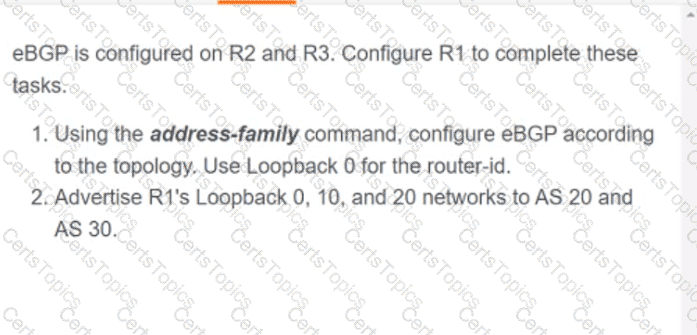
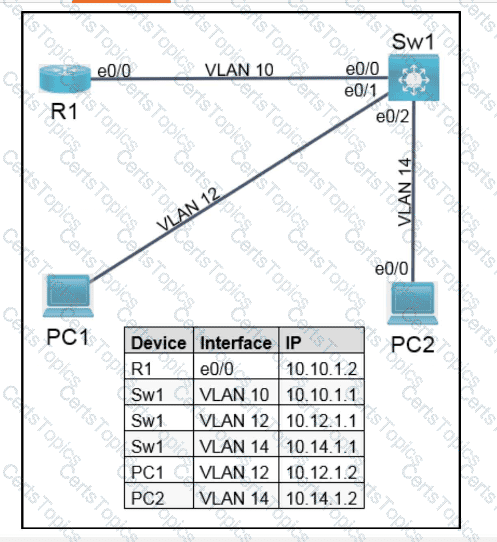

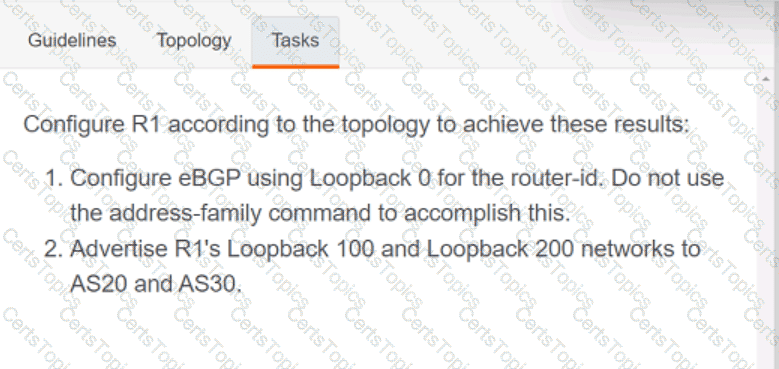
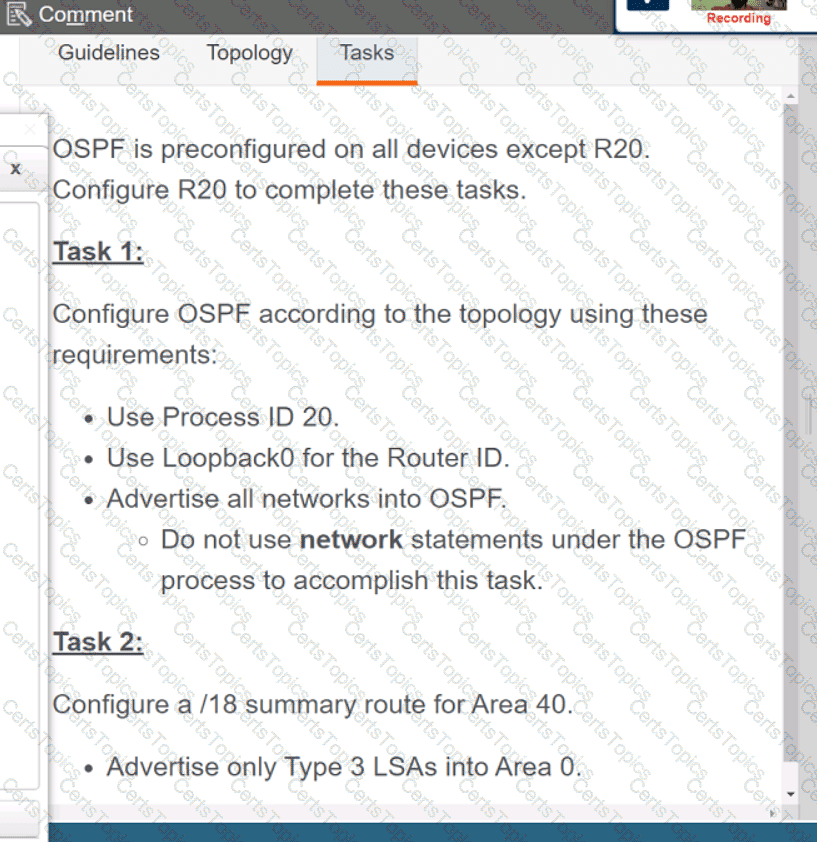
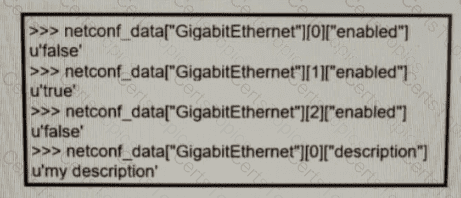
Refer to the exhibit. Which python code snippet prints the descriptions of disabled interface only?


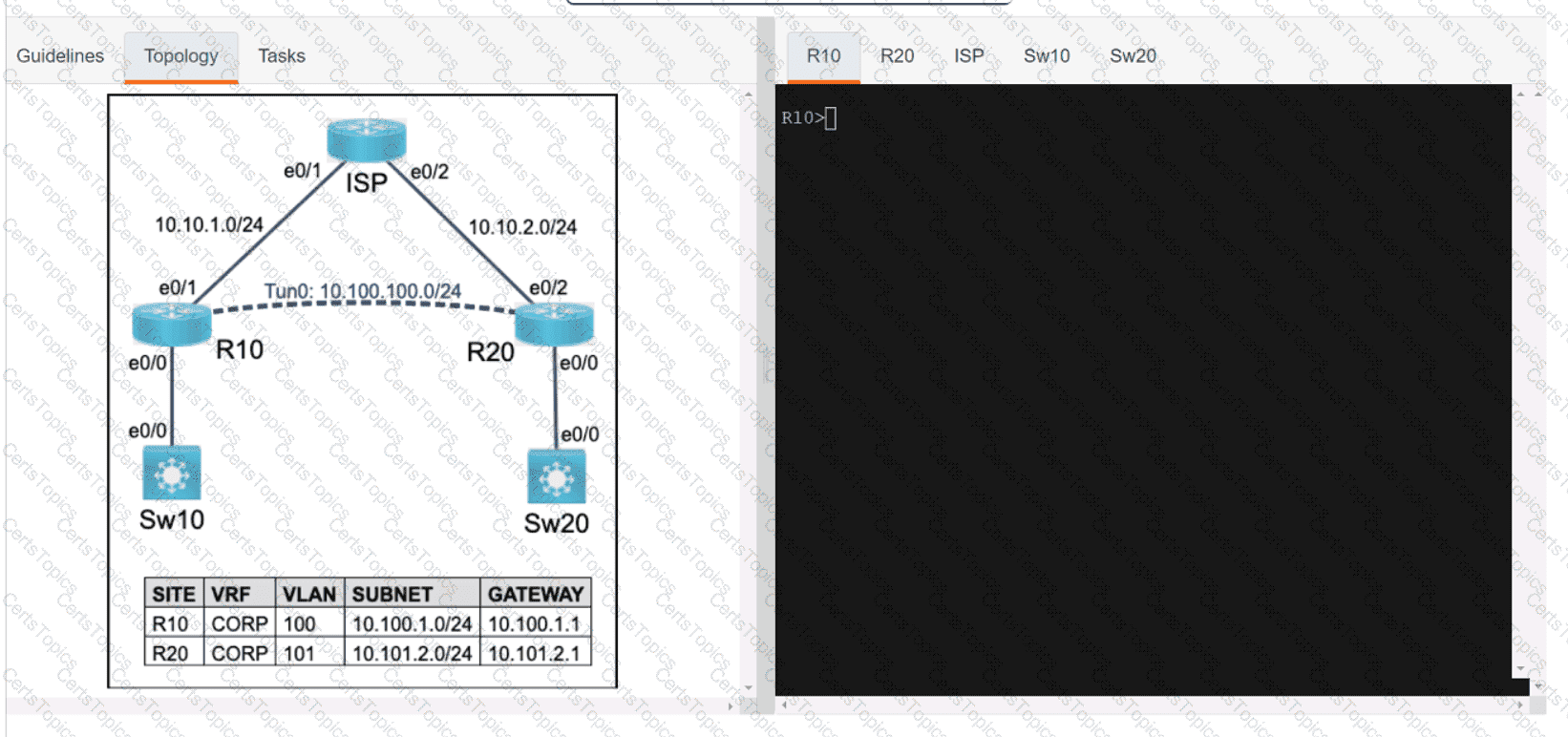
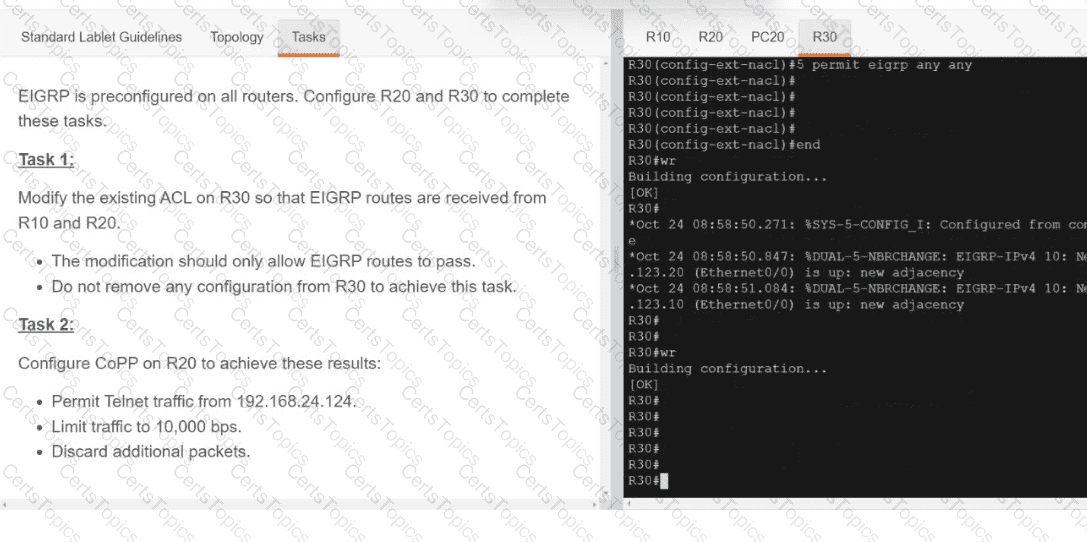
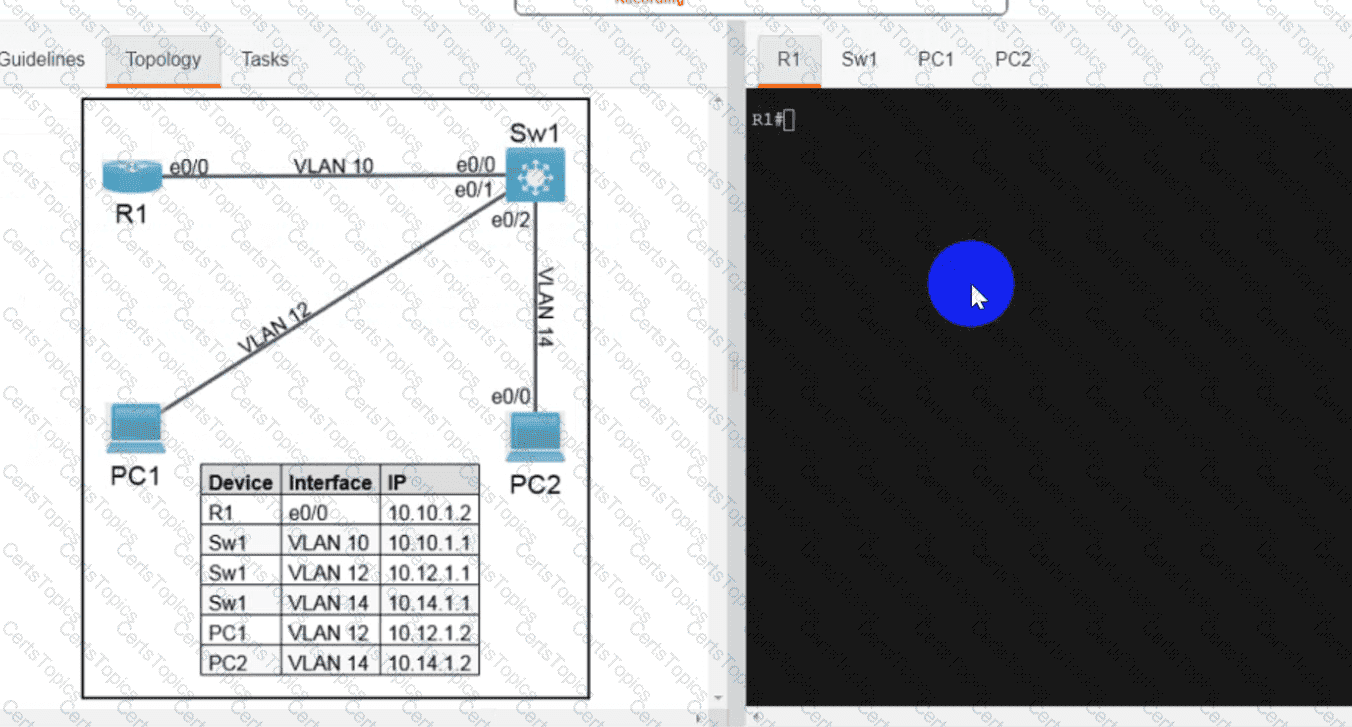
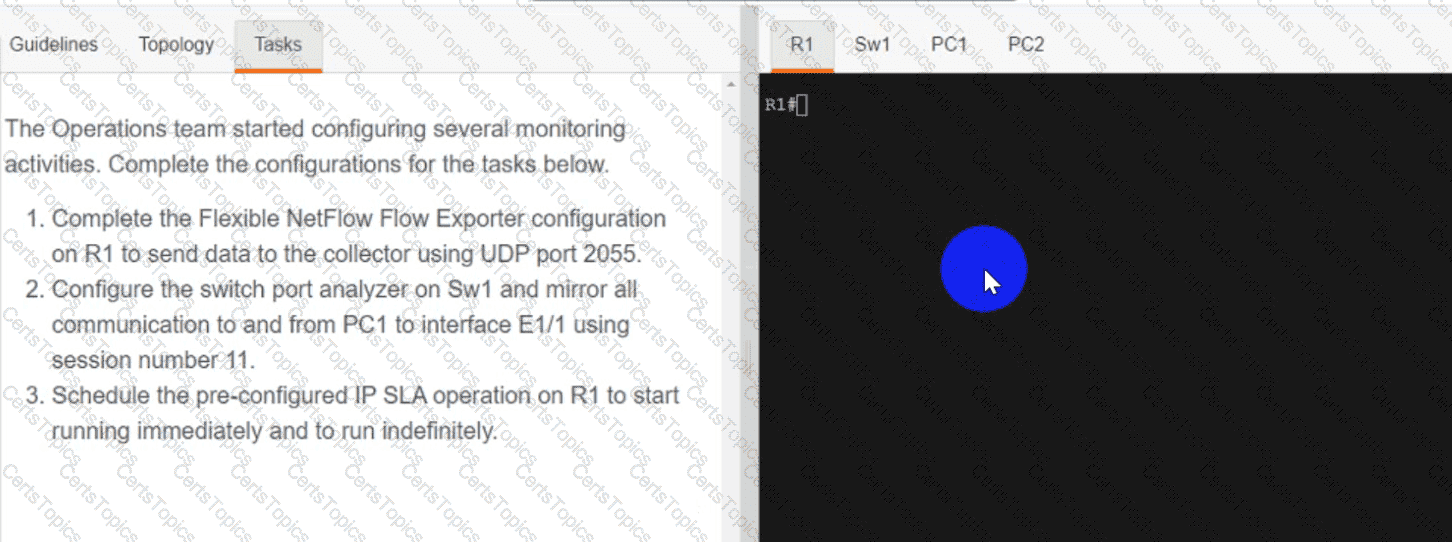
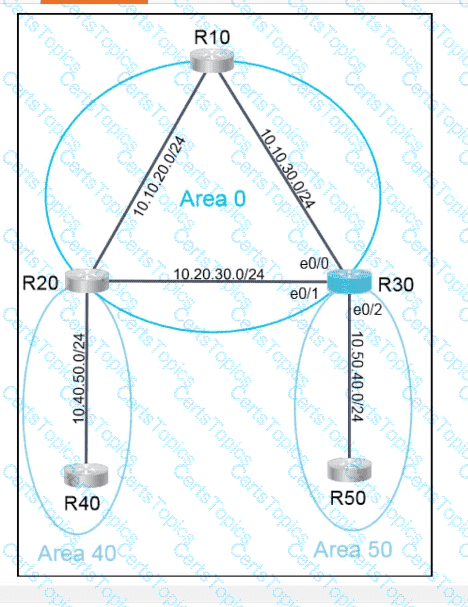
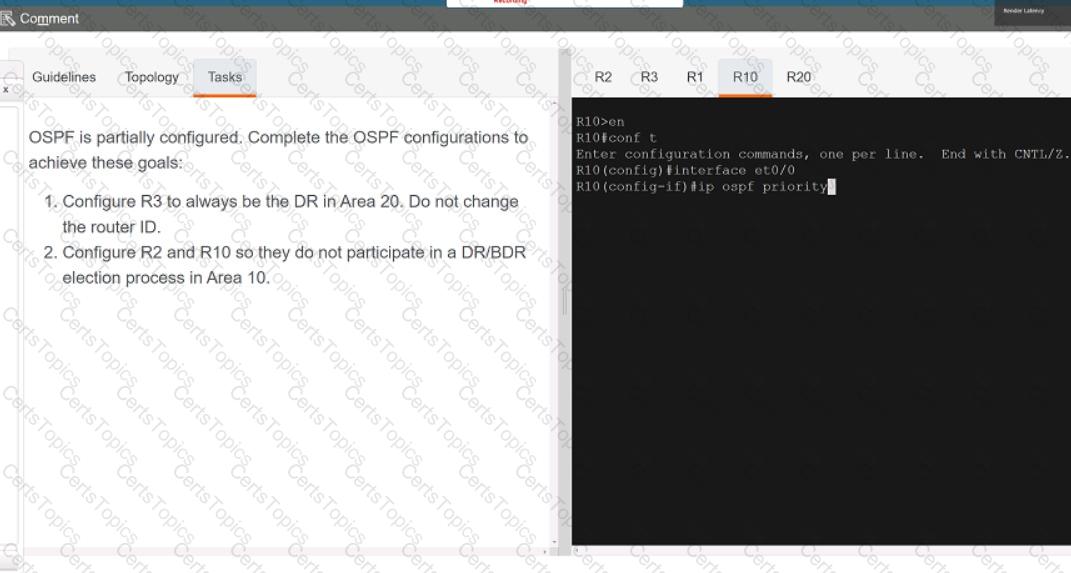
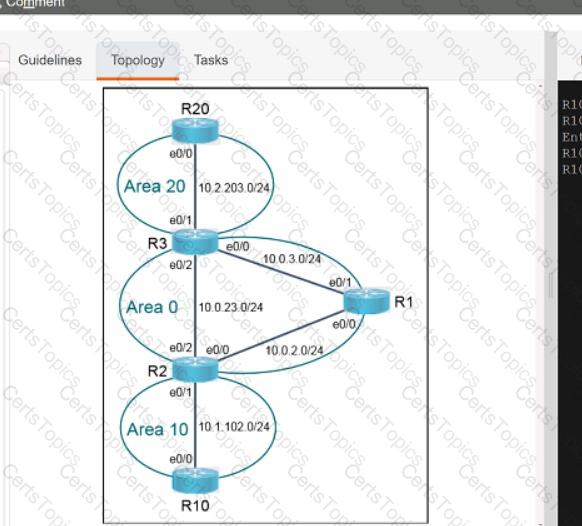
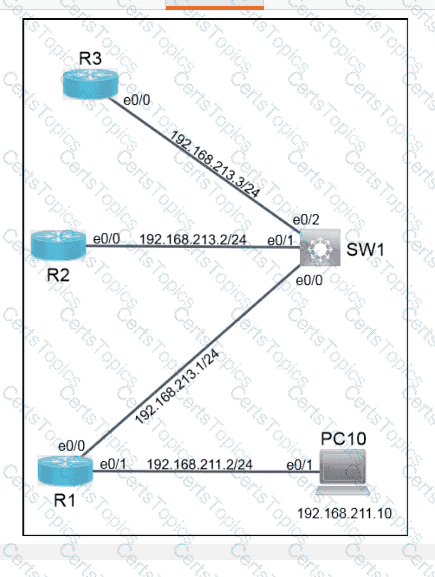
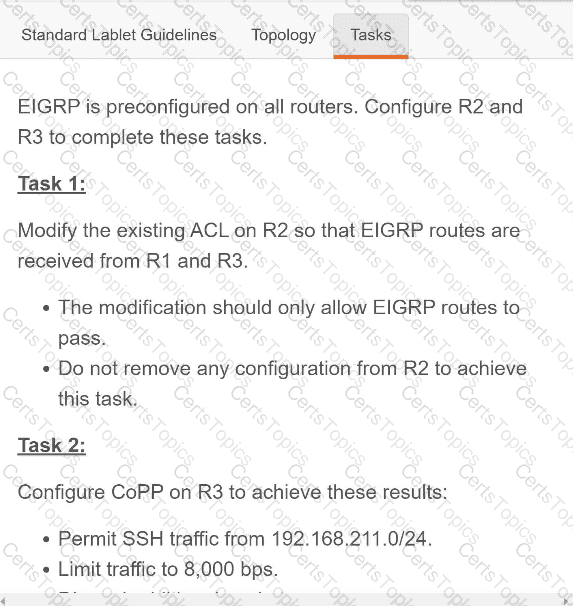
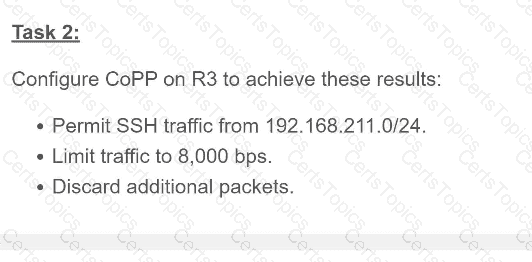
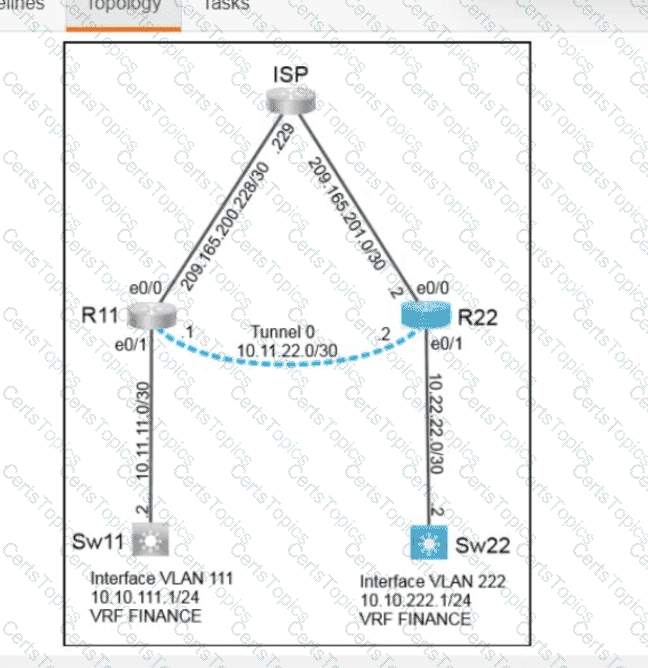
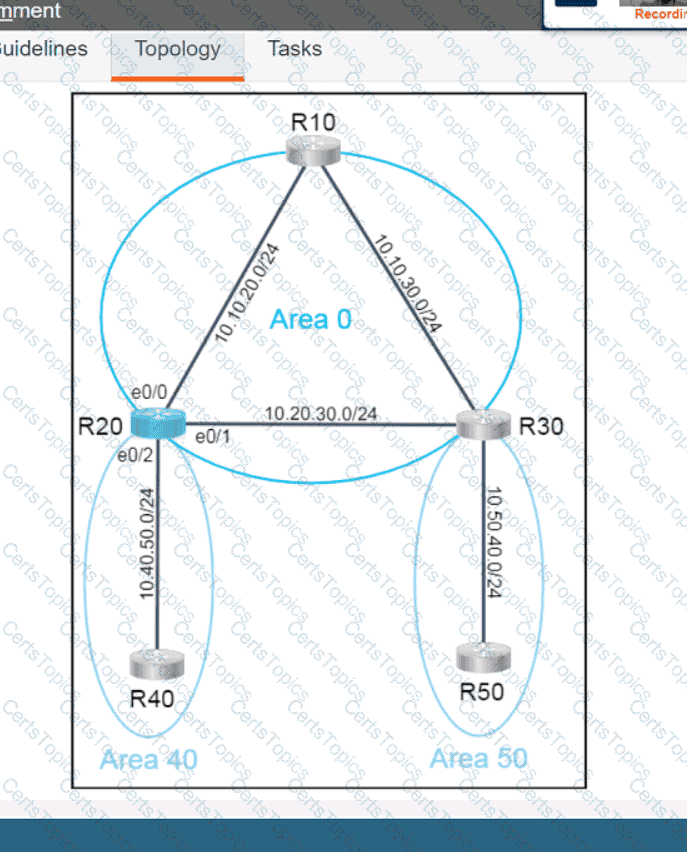
Refer to the exhibit. An engineer must create a script that appends the output of the show process cpu sorted command to a file.
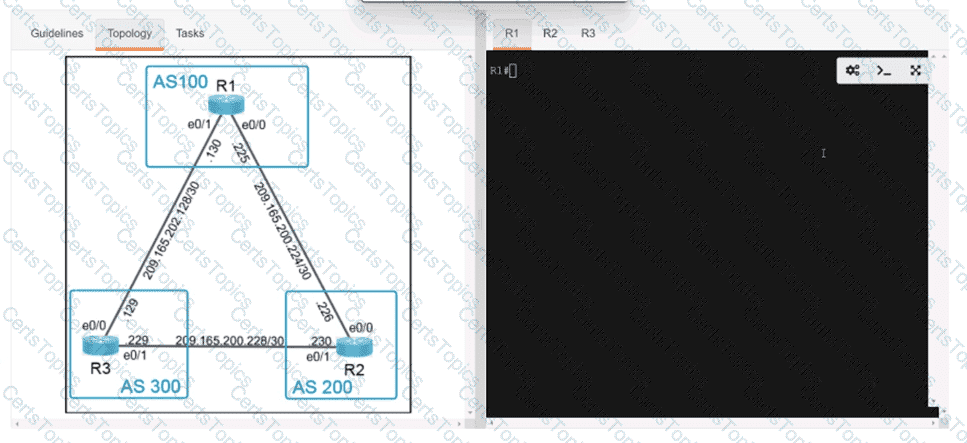
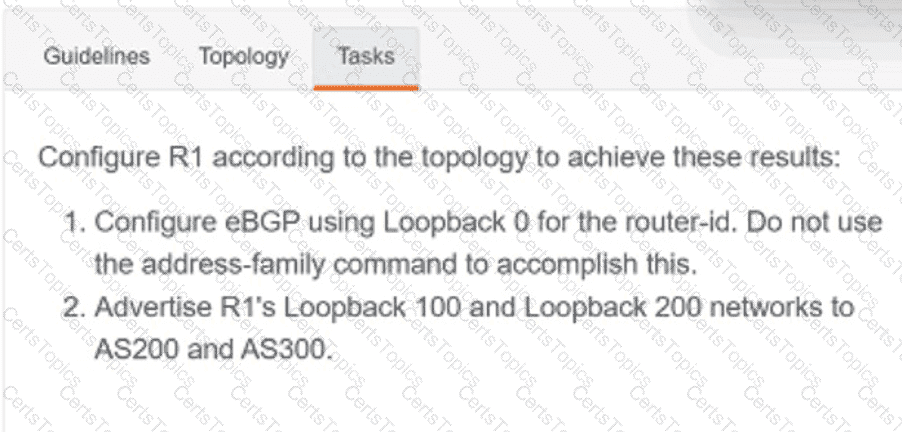
Which two components are needed when a Cisco SD-Access fabric is designed? (Choose two.)
Which AP mode allows an engineer to scan configured channels for rogue access points?
Which mechanism is used to protect the confidentiality of sensitive information exchanged over REST APIs?
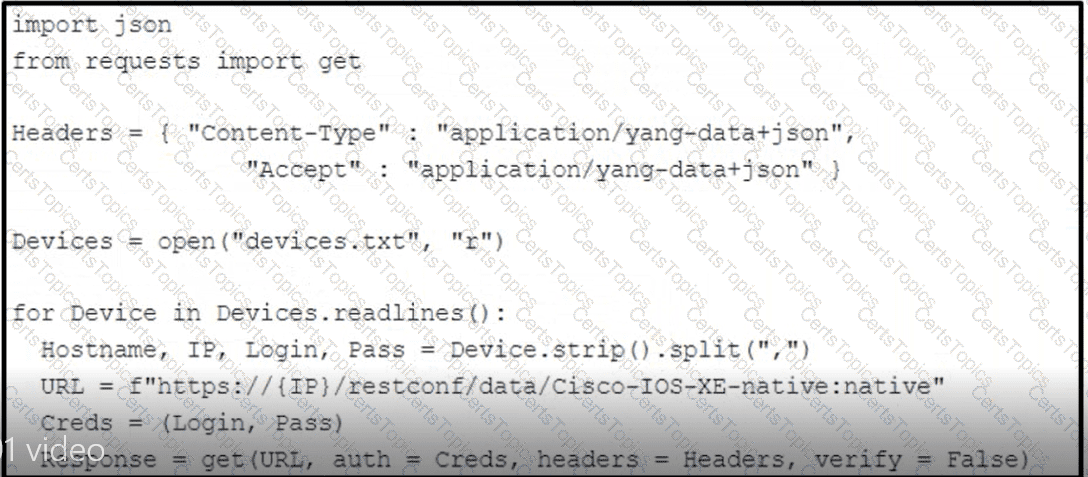
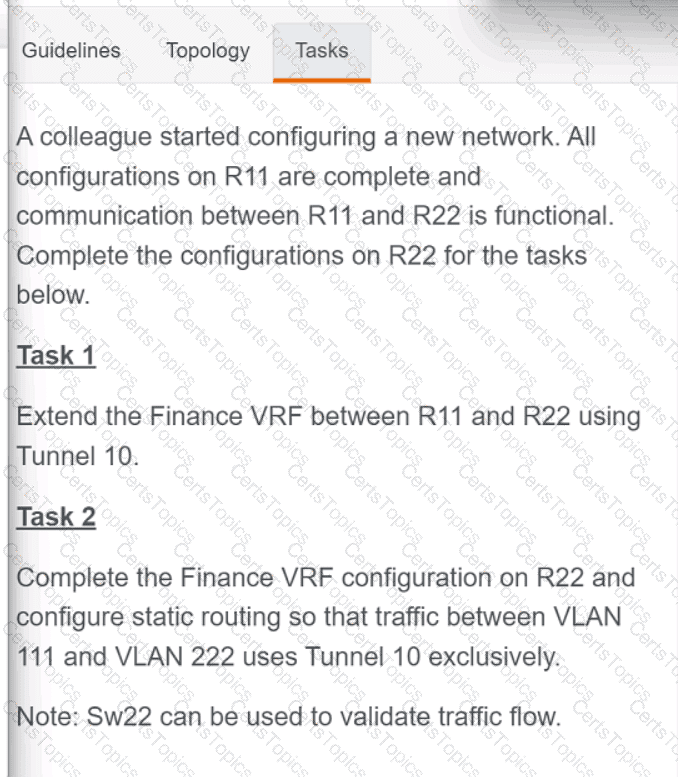
Refer to the exhibit. How should the script be completed so that each device configuration is saved into a JSON-formatted file under the device name?

Which statement describes the IP and MAC allocation requirements for virtual machines on types 1 hypervisors?
An engineer is configuring RADIUS-Based Authentication with EAP. MS-CHAPv2 is configured on a client device. Which outer method protocol must be configured on the ISE to support this authentication type?
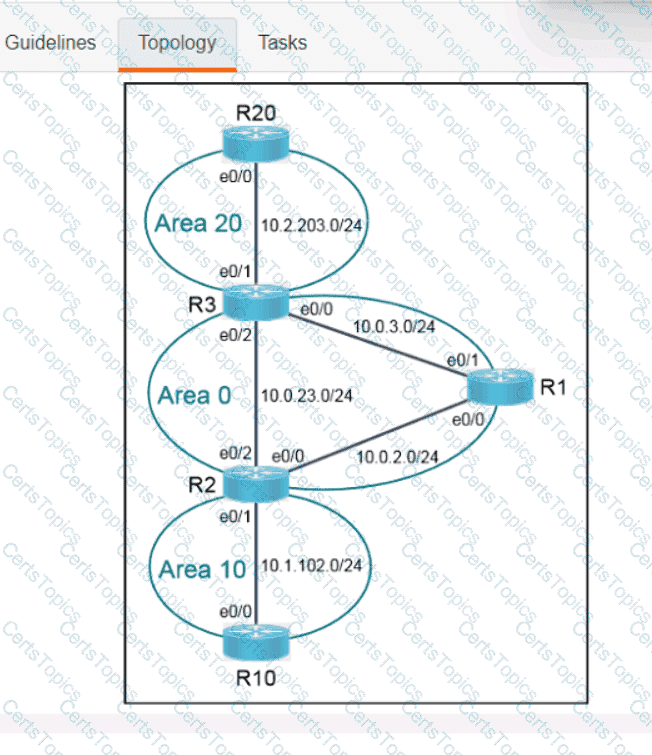
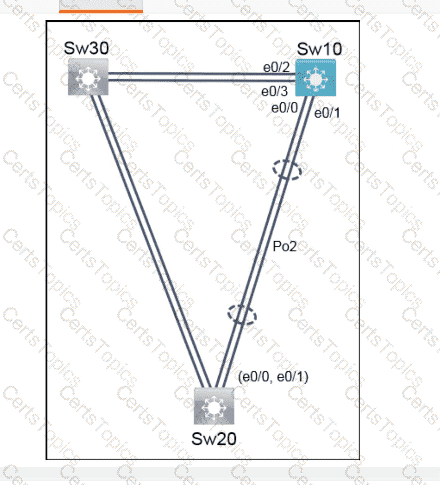
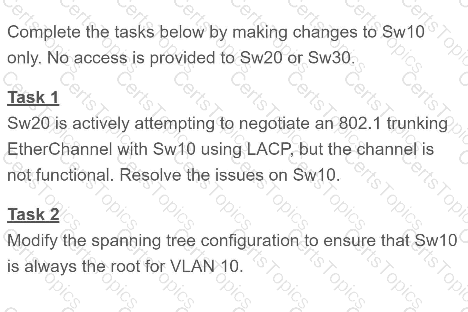
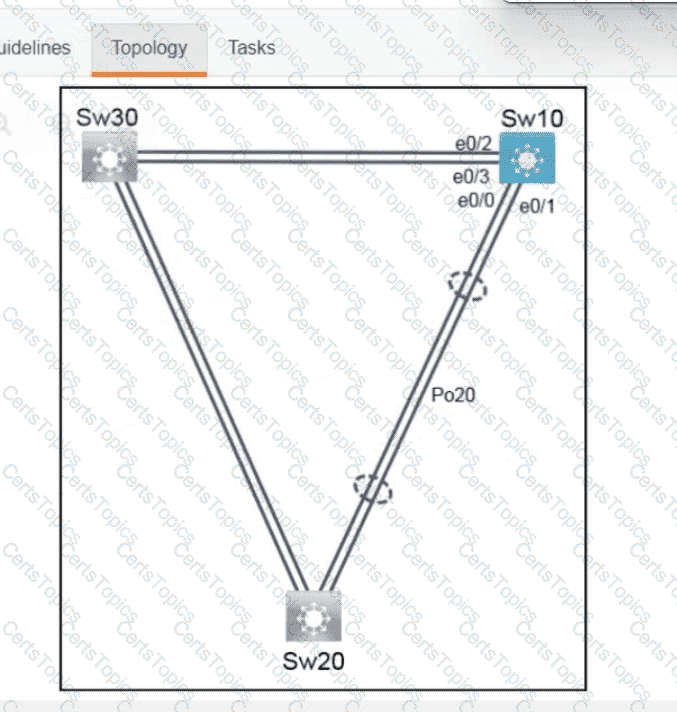
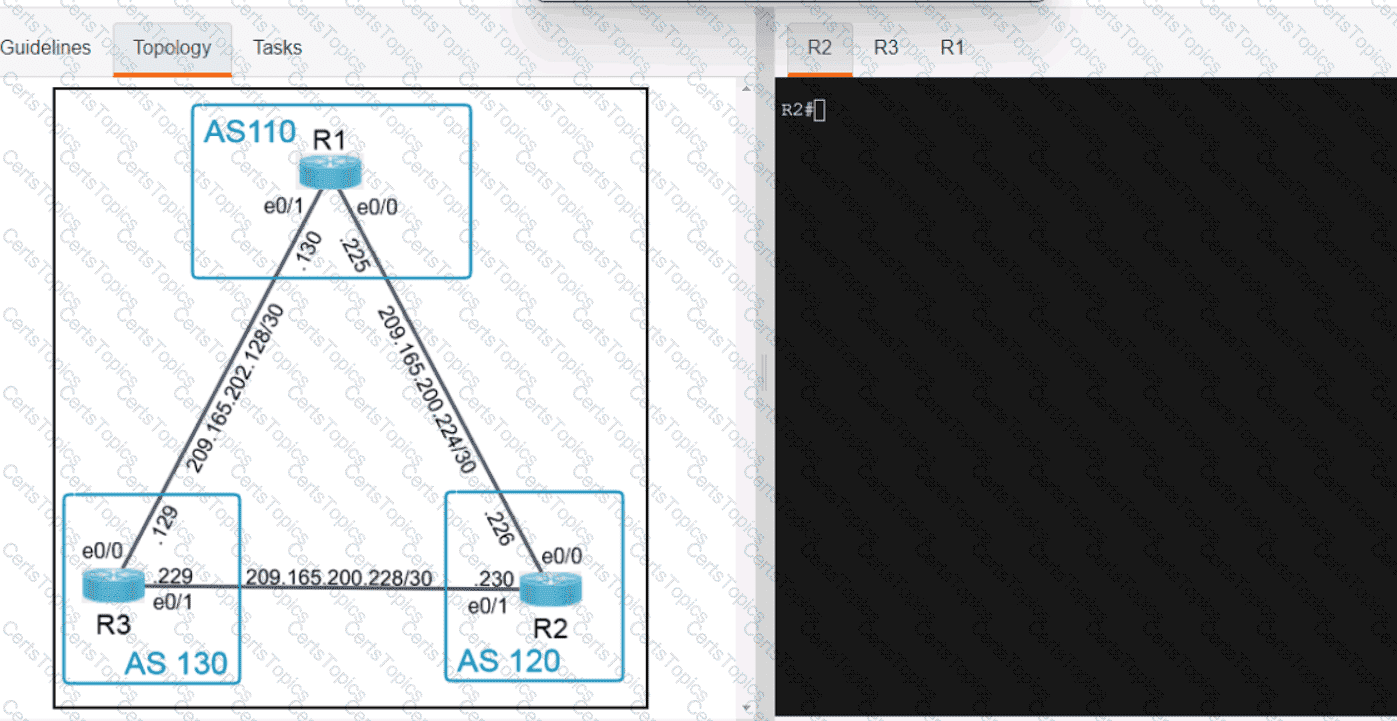
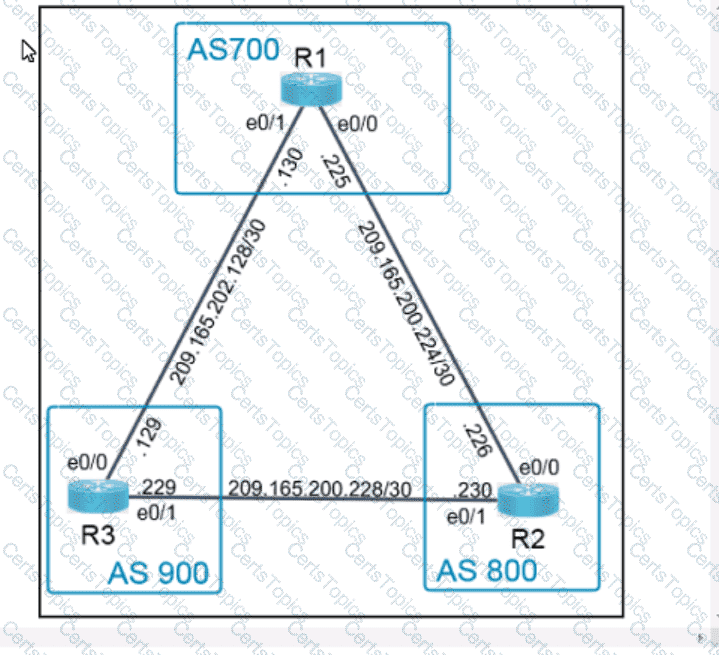
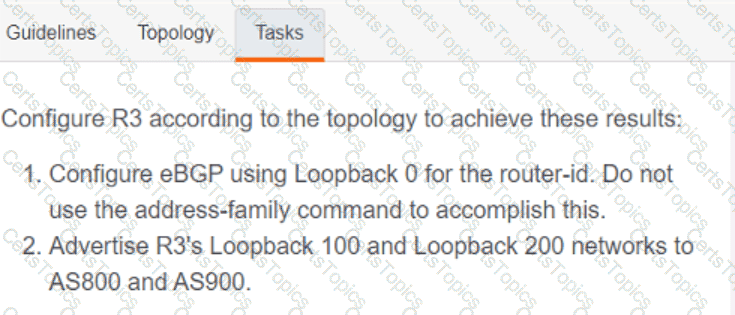
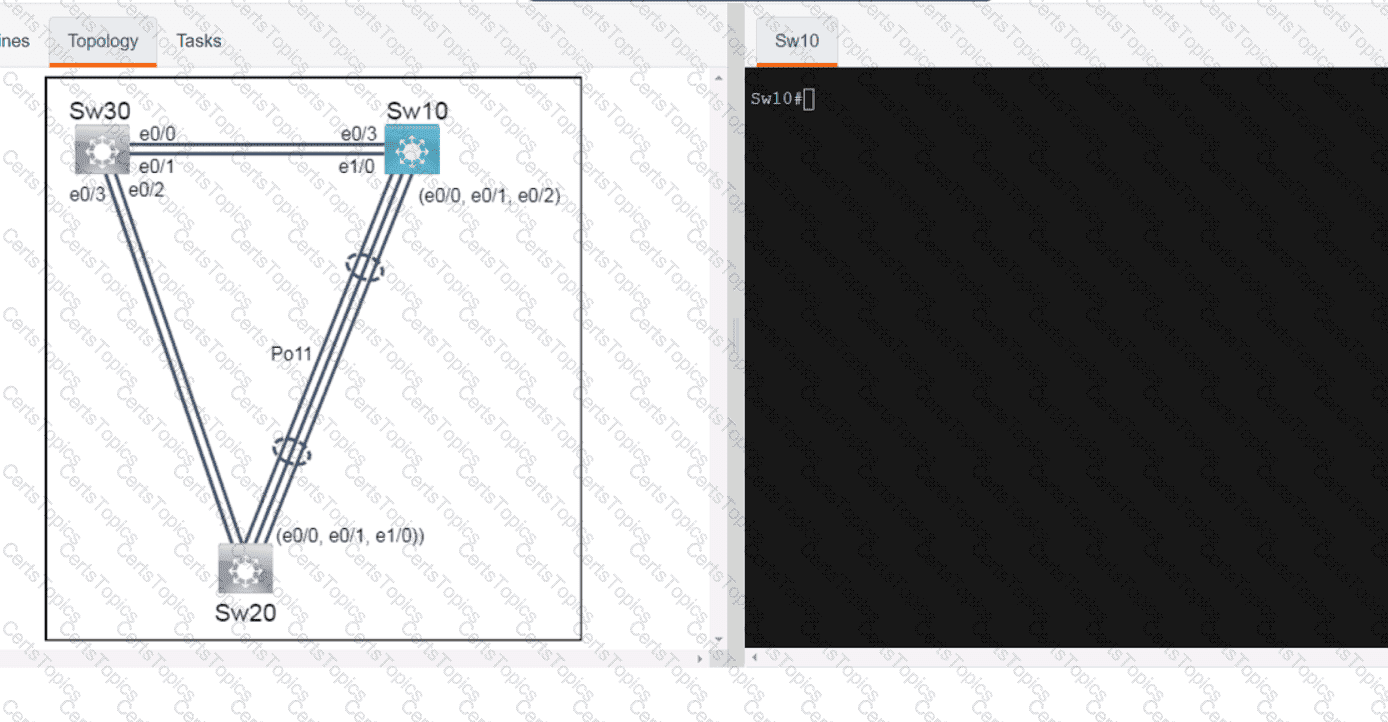
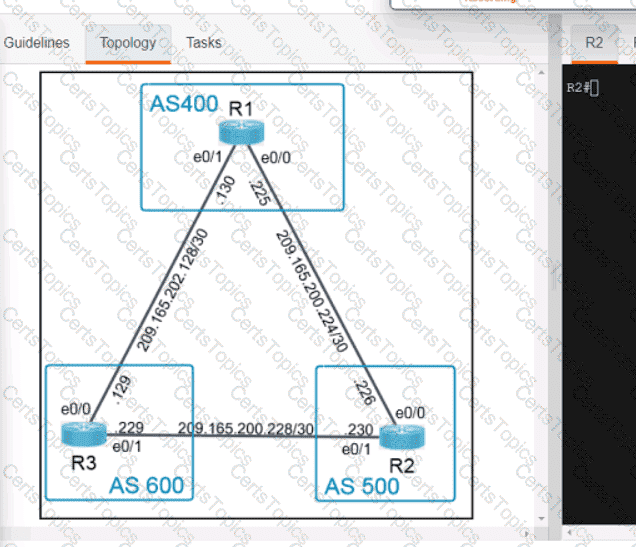
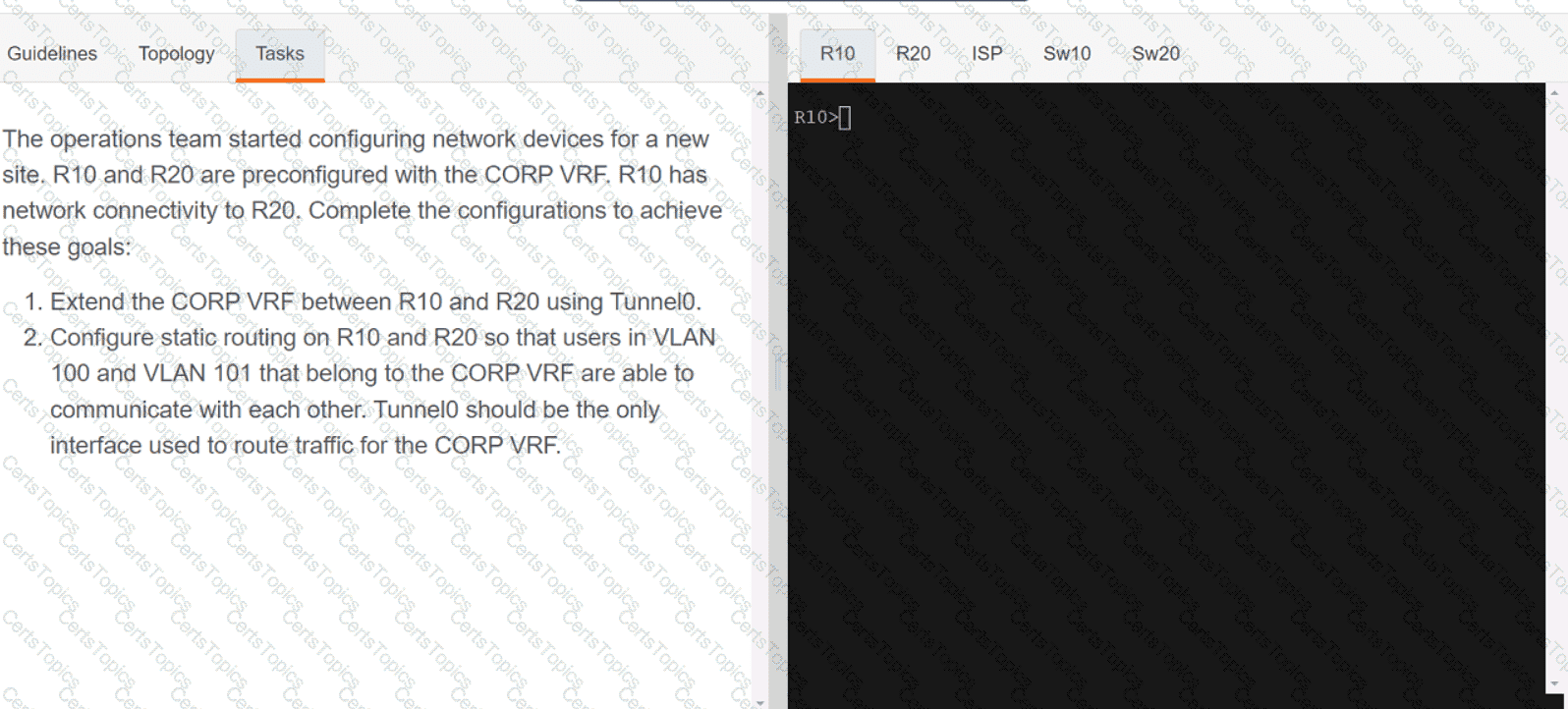
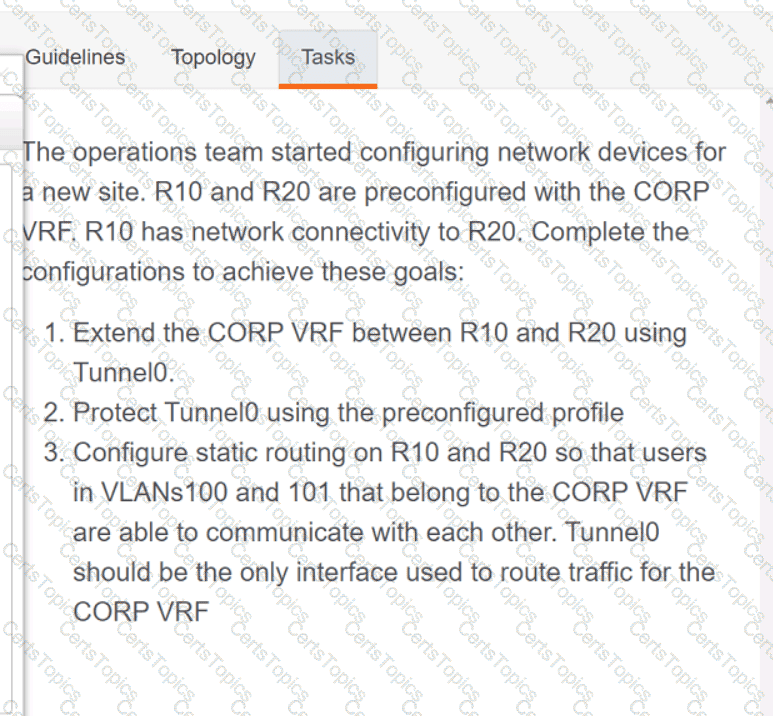
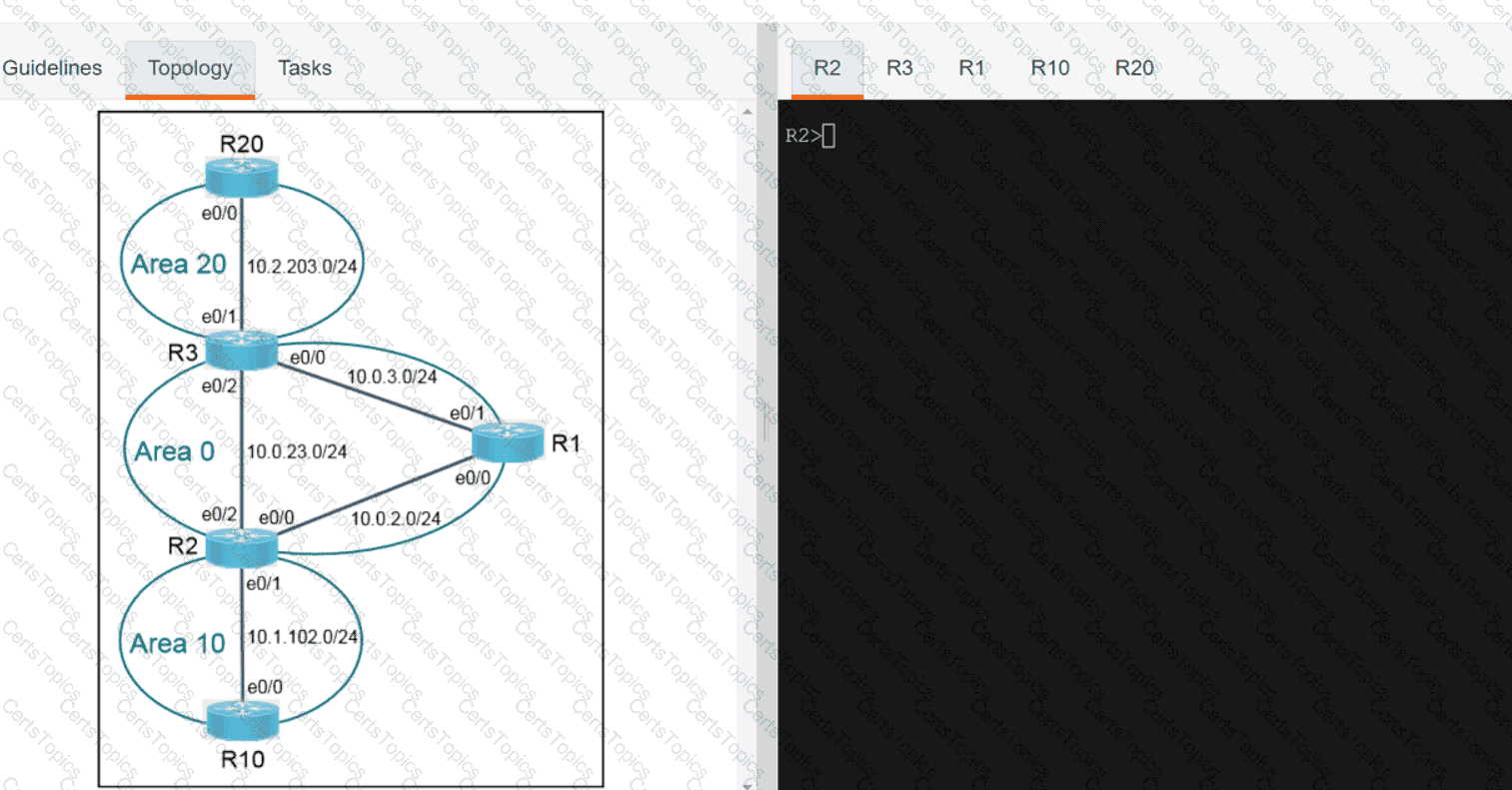
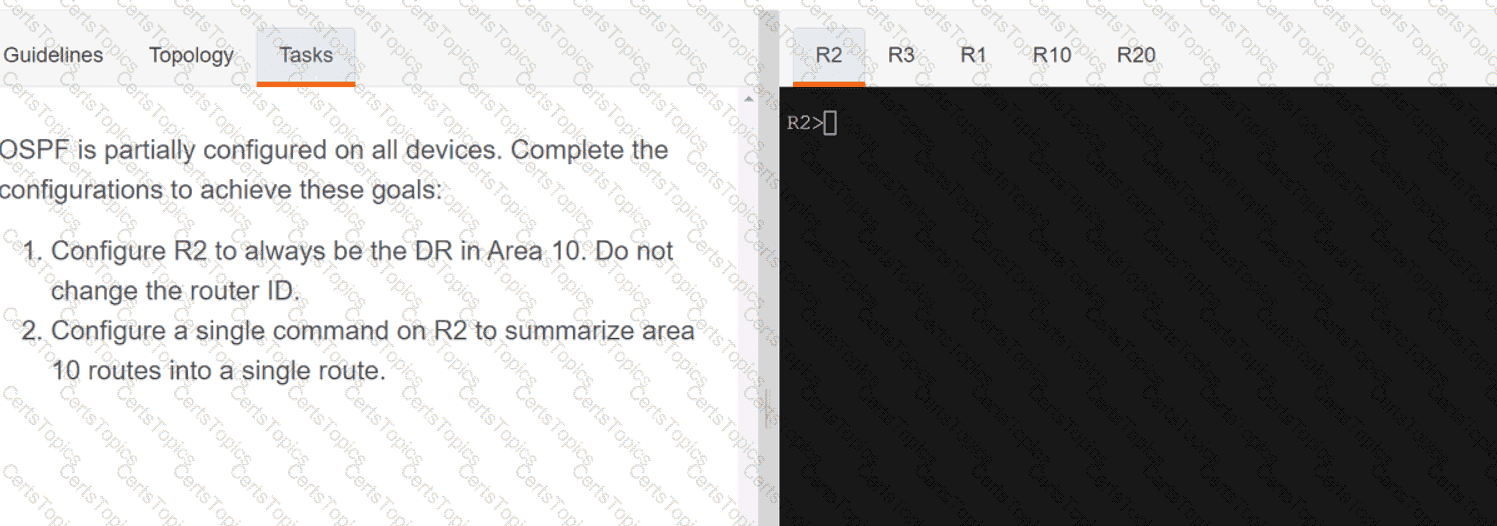
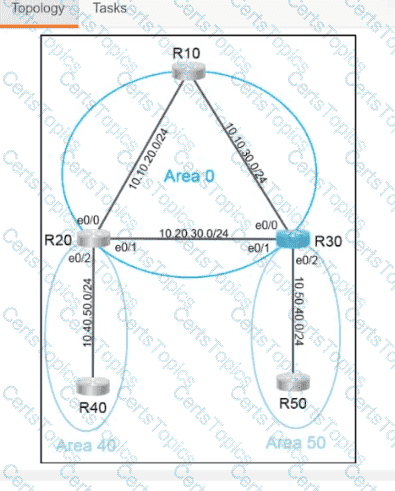
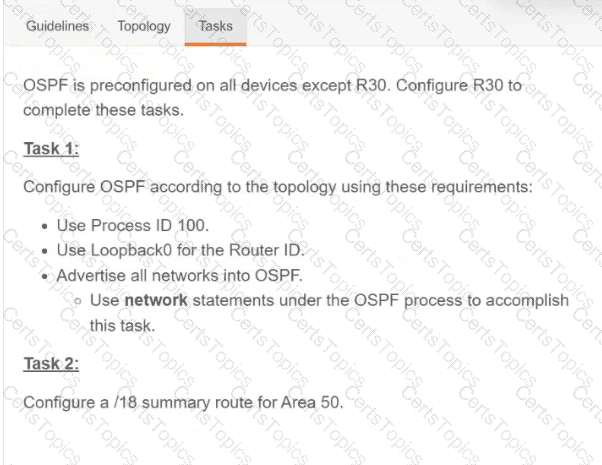
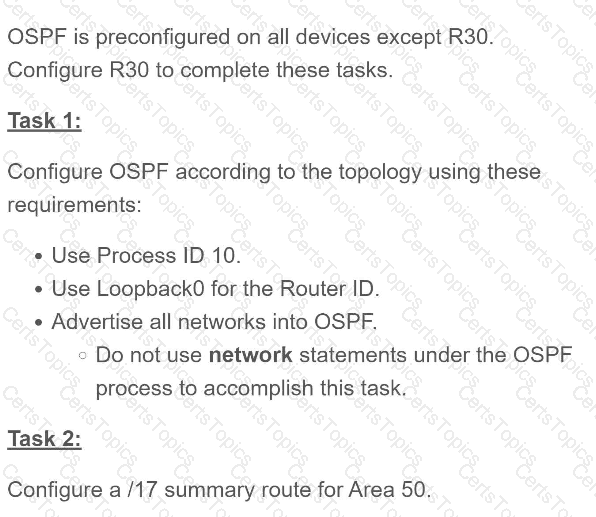
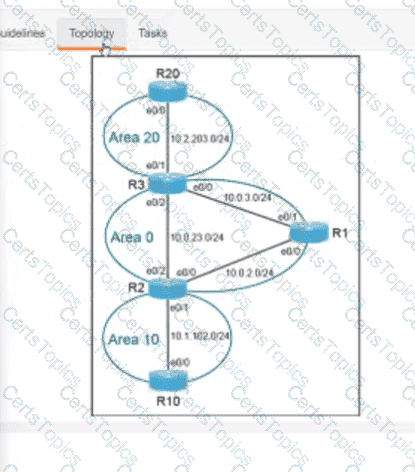
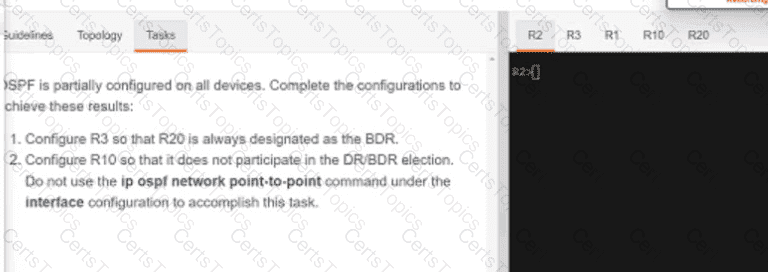
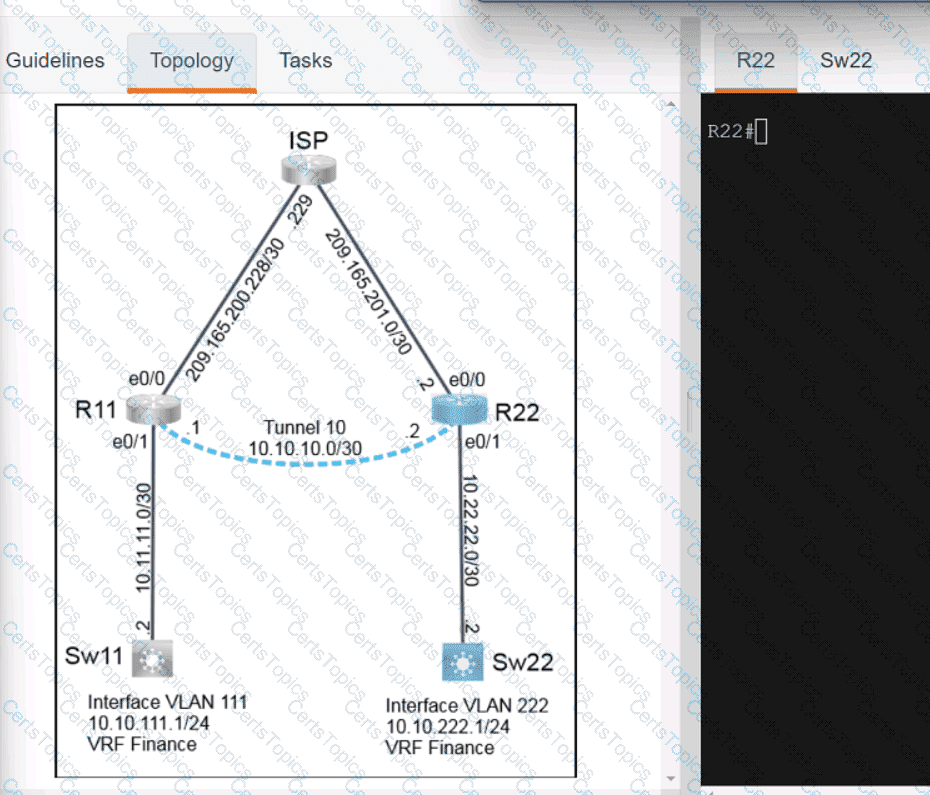
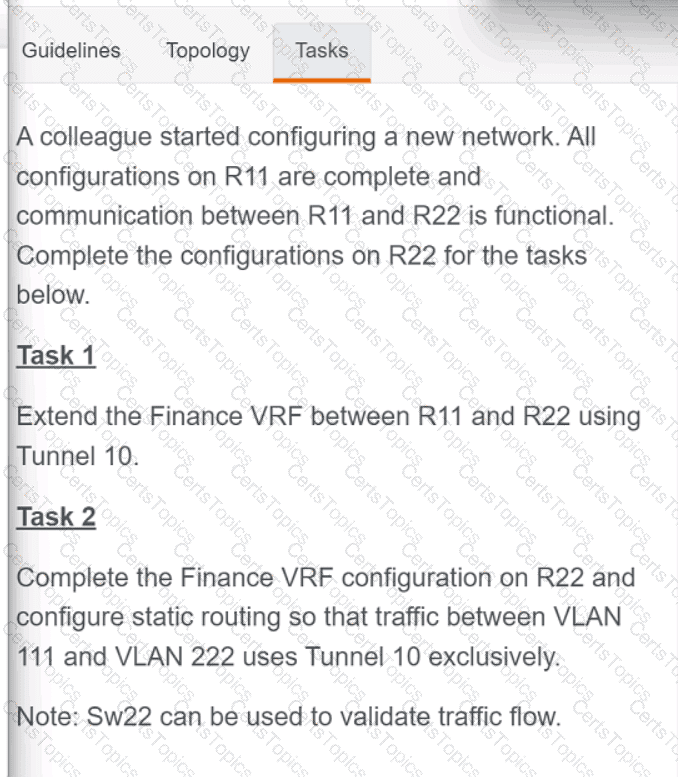
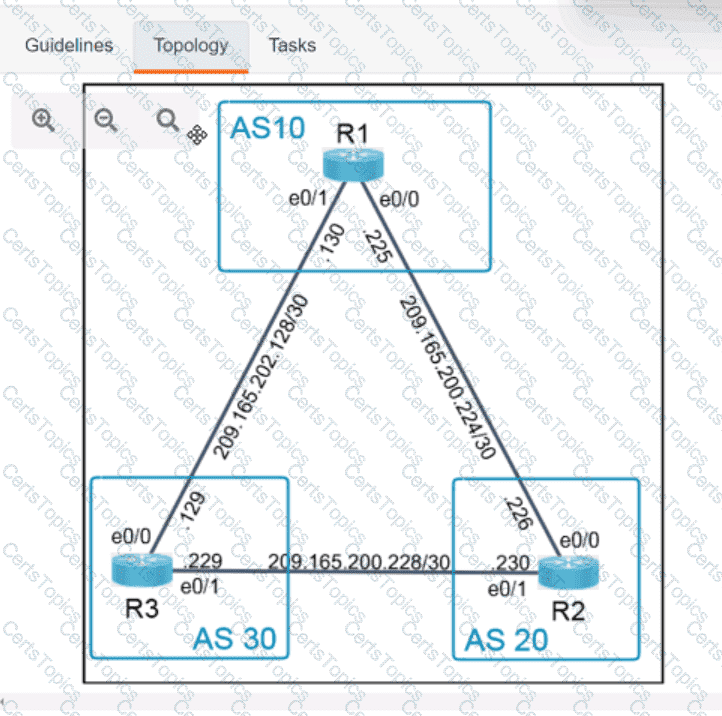
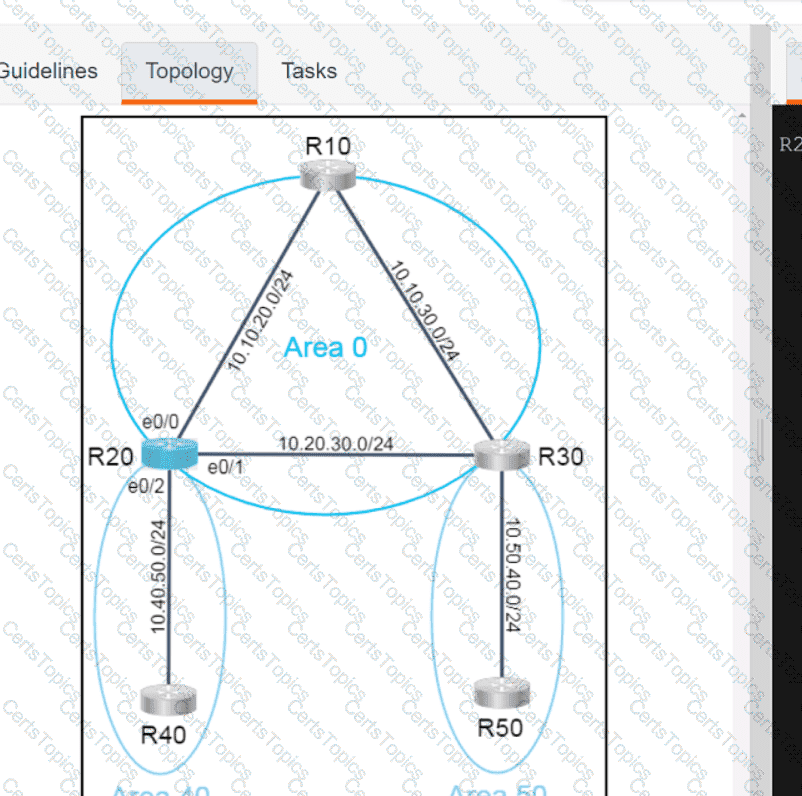
Refer to the exhibit.

Which JSON syntax is derived from this data?

Which authorization framework gives third-party applications limited access to HTTP services?
How do FHRPs differ from SSO?
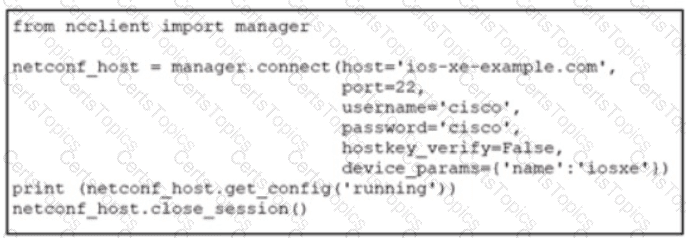
Refer to lhe exhibit. An engineer deploys a script to retrieve the running configuration from a NETCONF-capable CiscoIOSXE device that Is configured with default settings. The script fails. Which configuration must be applied to retrieve the configuration using NETCONF?
What is a characteristic of VXLAN?
Which method does FastLocate use to collect location-based information?
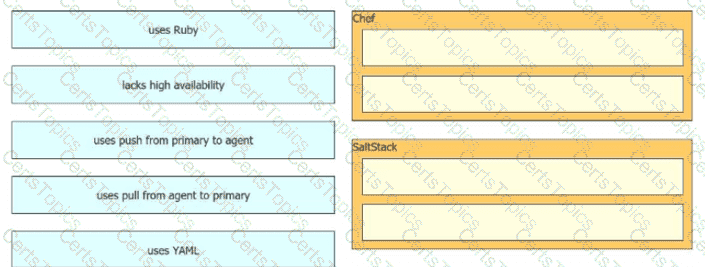
Drag and drop the automation characteristics from the left onto the appropriate tools on the right. Not all options are used.
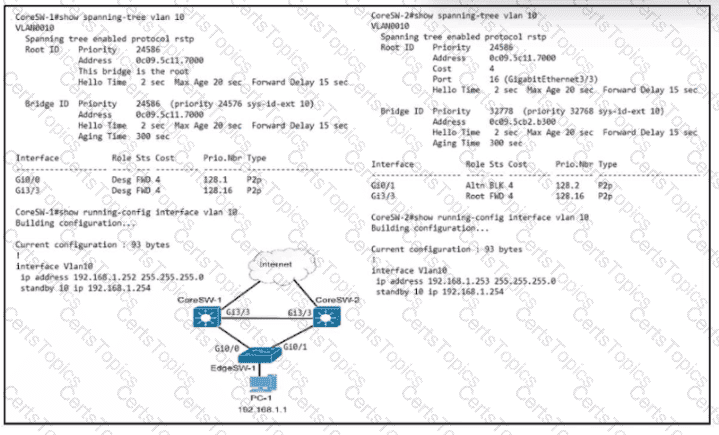
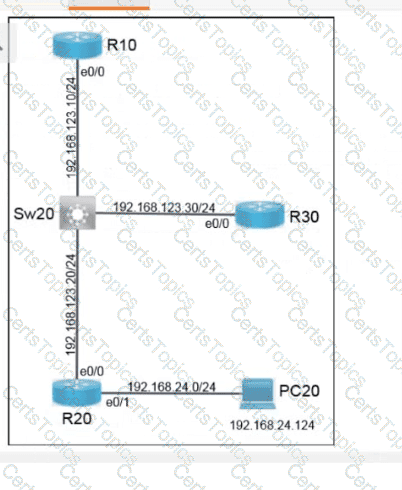
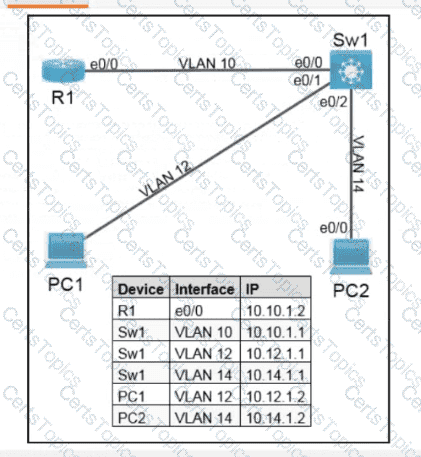
Refer to the exhibit. Which configuration causes the traffic from PC-1 to the internet to use the link between CoreSW-1 and CoreSW-2 when both switches are up?

Which A record type should be configured for access points to resolve the IP address of a wireless LAN controller using DNS?
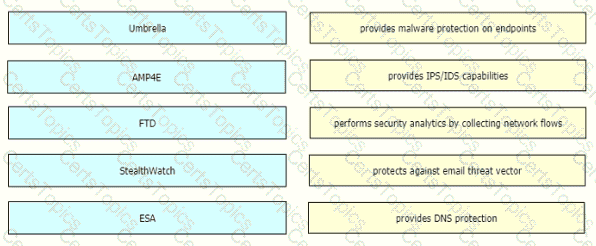
Drag and drop the threat defense solutions from the left onto their descriptions on the right.
Which new security enhancement is introduced by deploying a next-generation firewall at the data center in addition to the Internet edge?
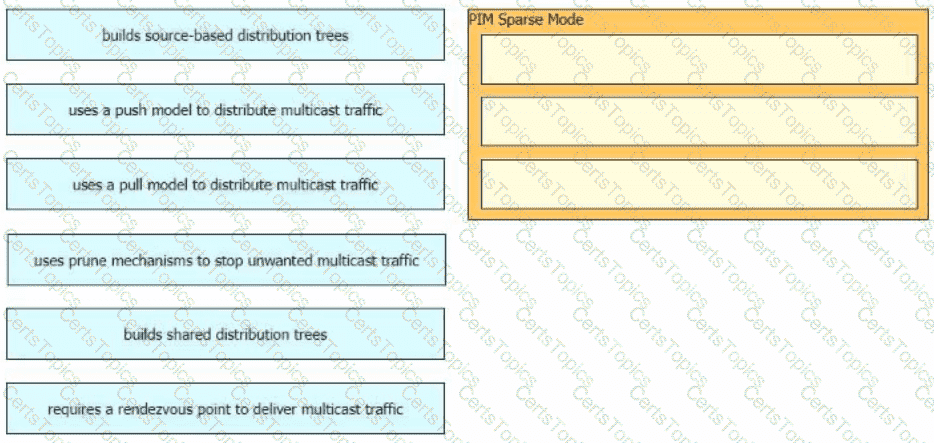
Drag and drop the characteristics of PIM Sparse Mode from the left to the right. Not all options are used.
What is the name of the numerical relationship of the wireless signal compared to the noise floor?
What is a capability of the Cisco DNA Center southbound API?
A customer requires their wireless data traffic to egress at the switch port of the access point. Which access point mode supports this?
A system must validate access rights to all its resources and must not rely on a cached permission matrix. If the access level to a given resource is revoked but is not reflected in the permission matrix, the security is violates Which term refers to this REST security design principle?
A script contains the statement •white loop != 999 ’ Which value terminates the loop?
An engineer is reviewing a PCAP file that contains a packet capture of a four-way handshake exchange between a dient and AP using WPA2 Enterprise Which EAPOL message validates and confirms that the client device has successfully Installed the GTK?
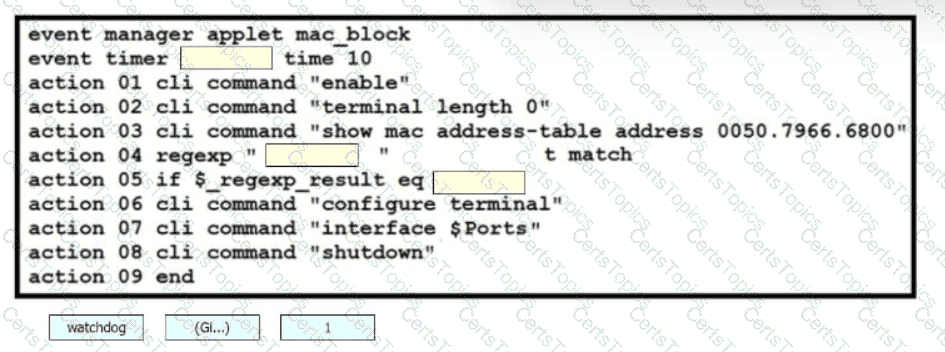
Drag and drop the snippets onto the blanks within the code to construct a script that blocks a MAC address.
What is contained in the VXLAN header?
Why is a Type 1 hypervisor more efficient than a Type 2 hypervisor?
A customer has two Cisco WLCs that manage separate APs throughout a building. Each WLC advertises the same SSID but terminates on different interfaces. Users report that they drop their connections and change IP addresses when roaming. Which action resolves this issue?