Task 5
You need to assign a Windows 10/11 Enterprise E3 license to the Sg-Retail group.
Task 10
You need to create a group named Audit. The solution must ensure that the members of Audit can activate the Security Reader role.
Task 6
You need to implement additional security checks before the members of the Sg-Executive can access any company apps. The members must meet one of the following conditions:
• Connect by using a device that is marked as compliant by Microsoft Intune.
• Connect by using client apps that are protected by app protection policies.
Your network contains an on-premises Active Directory domain that syncs to an Azure Active Directory (Azure AD) tenant. The tenant contains the users shown in the following table.

All the users work remotely.
Azure AD Connect is configured in Azure AD as shown in the following exhibit.
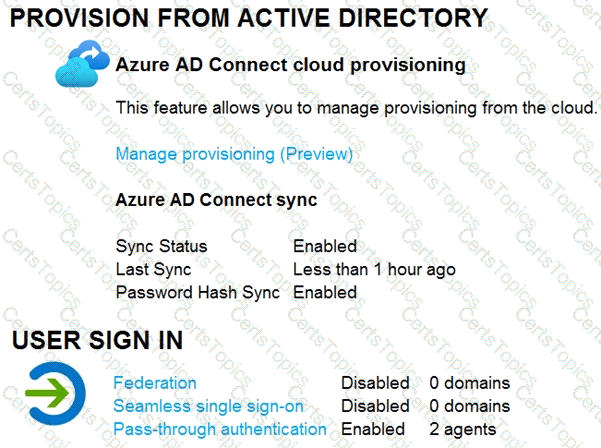
Connectivity from the on-premises domain to the internet is lost.
Which users can sign in to Azure AD?