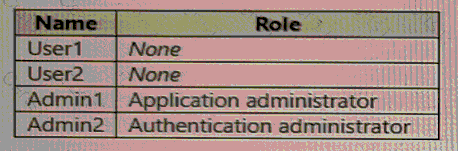
You have an Azure AD tenant that contains the users shown in the following table.
The User settings for enterprise applications have the following configuration.
• Users can consent to apps accessing company data on their behalf:
• Users can consent to apps accessing company data for the groups they
• Users can request admin consent to apps they are unable to consent to: Yes
• Who can review admin consent requests: Admin2, User2
User1 attempts to add an app that requires consent to access company data.
Which user can provide consent?
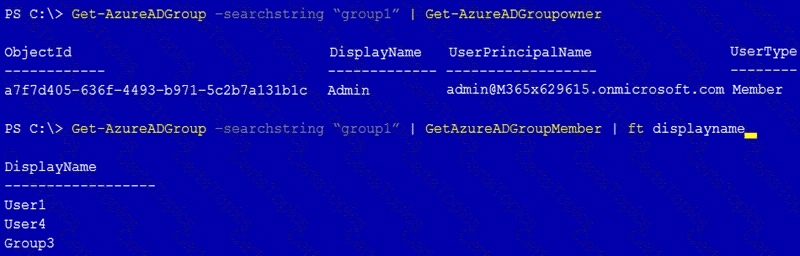
You have a Microsoft 365 tenant that contains a group named Group1 as shown in the Group1 exhibit. (Click theGroup1tab.)
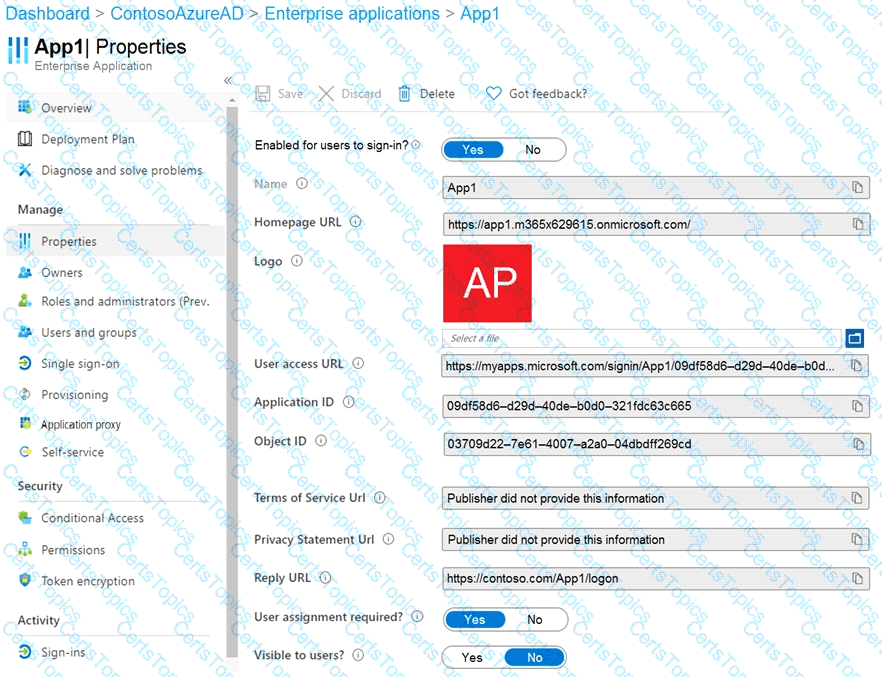
You create an enterprise application named App1 as shown in the App1 Properties exhibit. (Click theApp1 Propertiestab.)
You configure self-service for App1 as shown in the App1 Self-service exhibit. (Click theApp1Self-servicetab.)
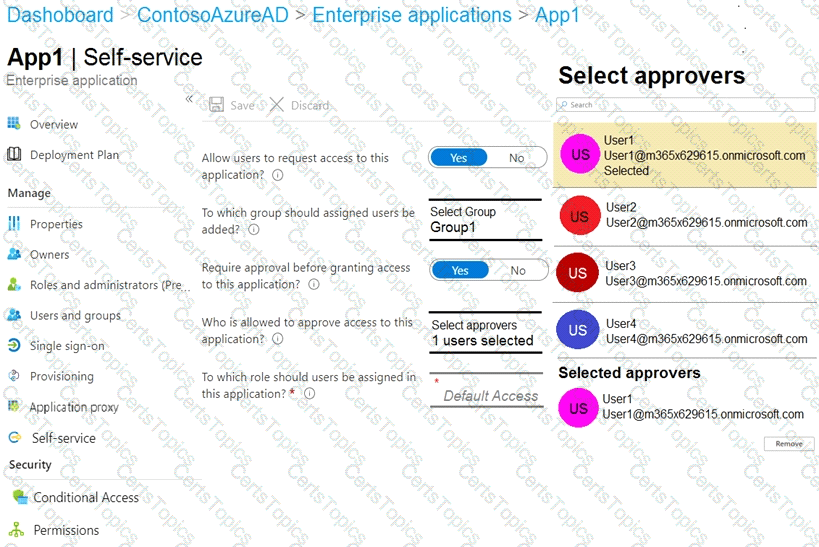
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE:Each correct selection is worth one point.

You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not Initiate.
Solution: From the Azure portal, you configure the Account lockout settings for multi-factor authentication (MFA).
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Active Directory forest that syncs to a Microsoft Entra tenant.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Microsoft Entra for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Microsoft Entra.
Solution: You configure Microsoft Entra Password Protection.
Does this meet the goal?