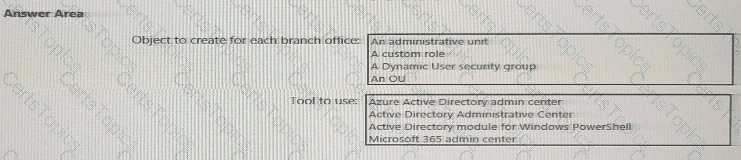
You need to meet the technical requirements for license management by the helpdesk administrators.
What should you create first, and which tool should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Task 1
You need to deploy multi factor authentication (MFA). The solution must meet the following requirements:
• Require MFA registration only for members of the Sg-Finance group.
• Exclude Debra Berger from having to register for MFA.
• Implement the solution without using a Conditional Access policy.
Task 2
You need to implement a process to review guest users who have access to the Salesforce app. The review must meet the following requirements:
• The reviews must occur monthly.
• The manager of each guest user must review the access.
• If the reviews are NOT completed within five days, access must be removed.
• If the guest user does not have a manager, Megan Bowen must review the access.
Task 9
You need to ensure that when users in the Sg-Operations group go to the My Apps portal a tab named Operations appears that contains only the following applications:
• Unkedln
• Box