EMC Related Exams
D-ISM-FN-23 Exam







Refer to the exhibit.
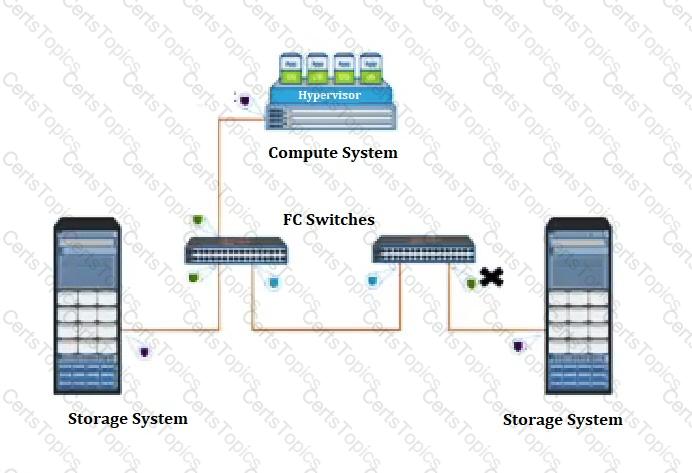
What type of Fibre Channel port does the “X” represent?
What is an accurate statement about data shredding?