ECCouncil Related Exams
412-79v10 Exam







ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.
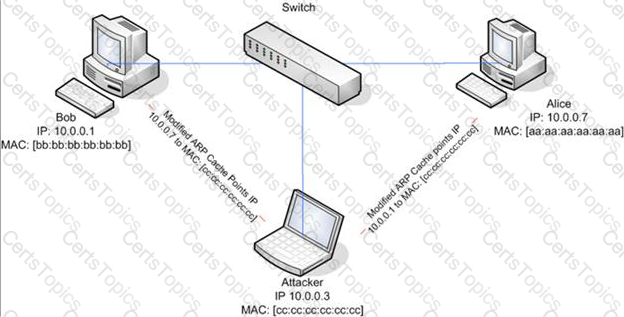
What type of attack would you launch after successfully deploying ARP spoofing?
Timing is an element of port-scanning that can catch one unaware. If scans are taking too long to complete or obvious ports are missing from the scan, various time parameters may need to be adjusted.
Which one of the following scanned timing options in NMAP’s scan is useful across slow WAN links or to hide the scan?
Transmission Control Protocol (TCP) is a connection-oriented four layer protocol. It is responsible for breaking messages into segments, re-assembling them at the destination station, and re-sending. Which one of the following protocols does not use the TCP?