You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
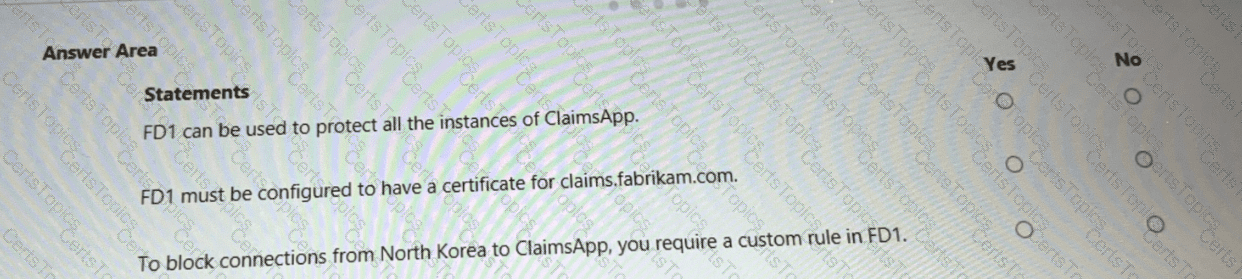
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
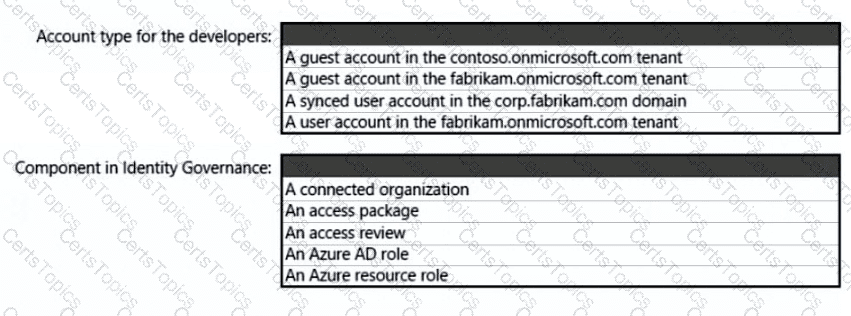
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
What should you create in Azure AD to meet the Contoso developer requirements?
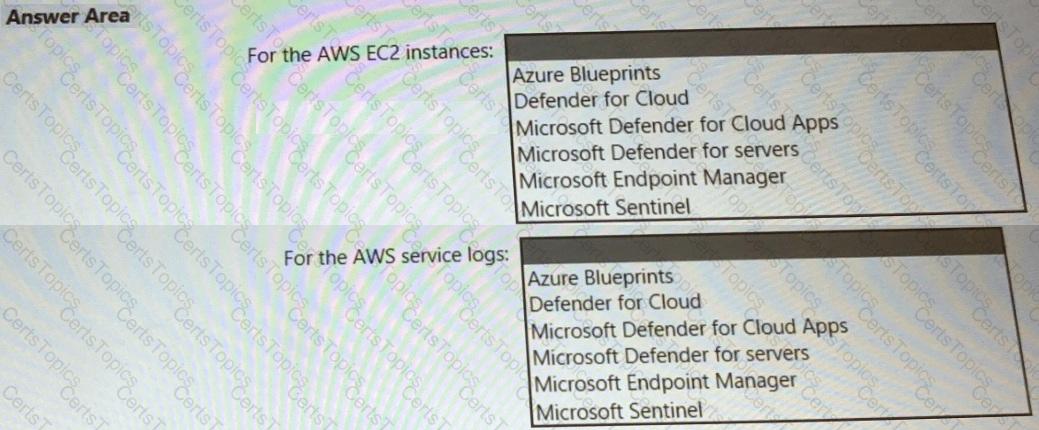
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
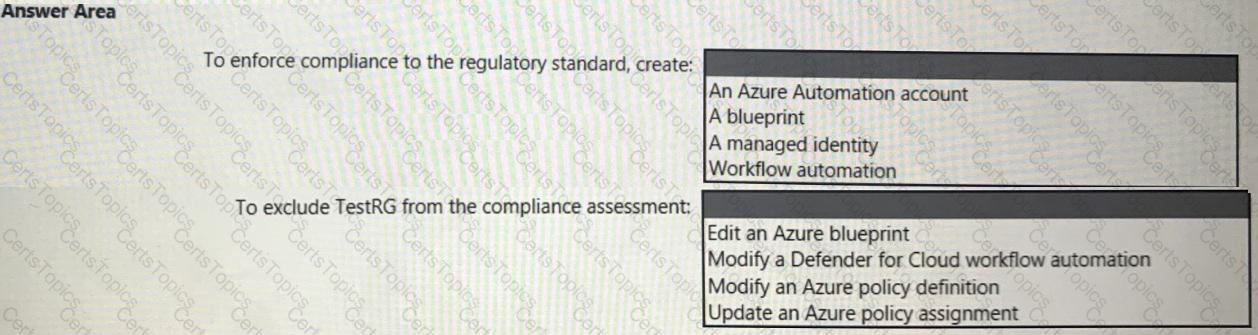
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
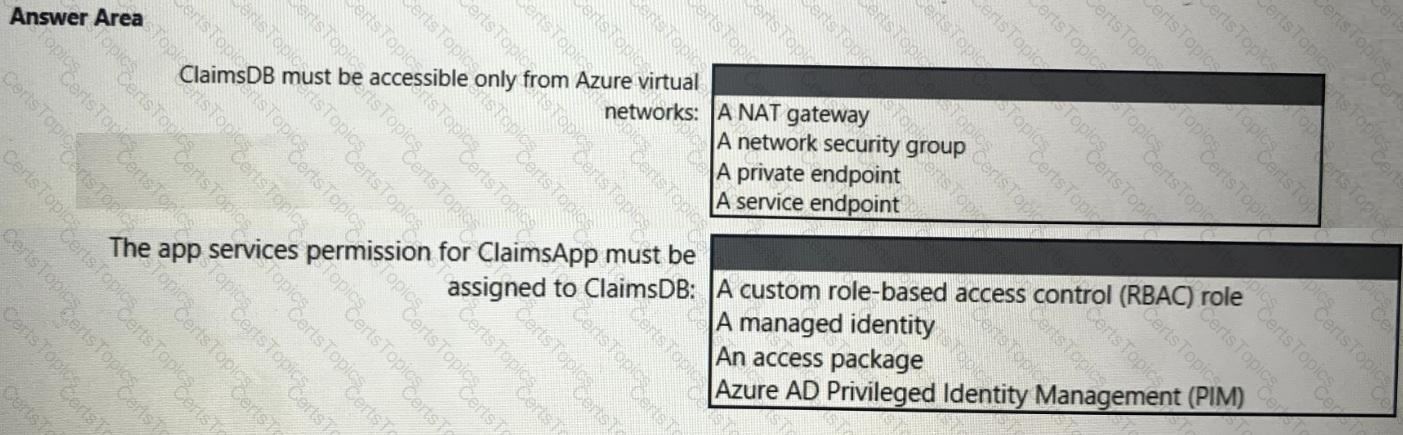
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company is developing a modern application that will run as an Azure App Service web app. You plan to perform threat modeling to identify potential security issues by using the Microsoft Threat Modeling Tool. Which type of diagram should you create?
You have an Azure subscription that contains a Microsoft Sentinel workspace.
Your on-premises network contains firewalls that support forwarding event logs m the Common Event Format (CEF). There is no built-in Microsoft Sentinel connector for the firewalls
You need to recommend a solution to ingest events from the firewalls into Microsoft Sentinel.
What should you include m the recommendation?
You have a Microsoft Entra tenant named contoso.com and use Microsoft Intune. Each user in contoso.com has a Microsoft Entra ID P1 license and a Windows 11 device that has the Global Secure Access client deployed.
You plan to deploy the following configuration of Microsoft Entra Internet Access:
• Enable a baseline profile.
• Create a security profile named Profile` that has a priority of 300 and contains a single web content filtering policy named WCFPolicy configure WCFPolicy1 as follows:
o Set Action to allow.
o Include a single rule that has a fully qualified domain name (FQDN) destination of ‘. adatum.com.
• Link Profile1 to a Conditional Access policy named CAPolicy1, apply CAPolicy1 to all users, and grant access unless a user's device is noncompliant
You need to evaluate the impact of the planned deployment on traffic to the following resources:
•
•
Which two traffic scenarios will occur? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point
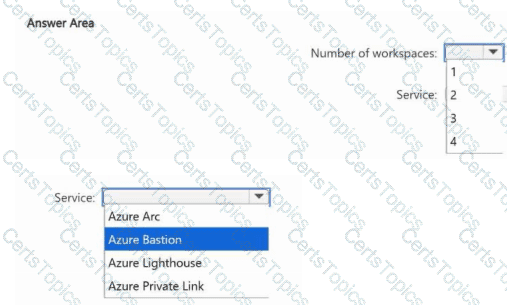
You have four Azure subscriptions named Sub1, Sub2, Sub3, and Sub4. Each subscription has a unique Microsoft Entra tenant that is linked to a Microsoft 365 subscription. Sub1 contains a user named User1.
You plan to implement Microsoft Sentinel.
You need to ensure that User1 can monitor Microsoft Entra ID events and Microsoft 365 events for Sub2, Sub3, and Sub4 by using Microsoft Sentinel. The solution must minimize administrative effort.
What is the minimum number of Microsoft Sentinel workspaces you should create, and which Azure service should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company develops several applications that are accessed as custom enterprise applications in Azure Active Directory (Azure AD). You need to recommend a solution to prevent users on a specific list of countries from connecting to the applications. What should you include in the recommendation?
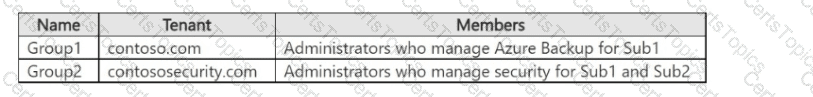
You have the Azure subscriptions shown in the following table.
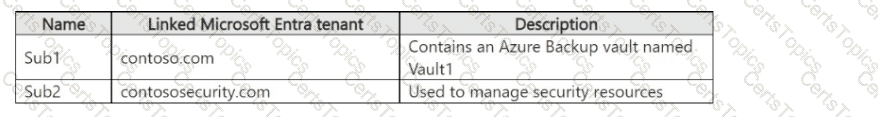
The tenants contain the groups shown in the following table.
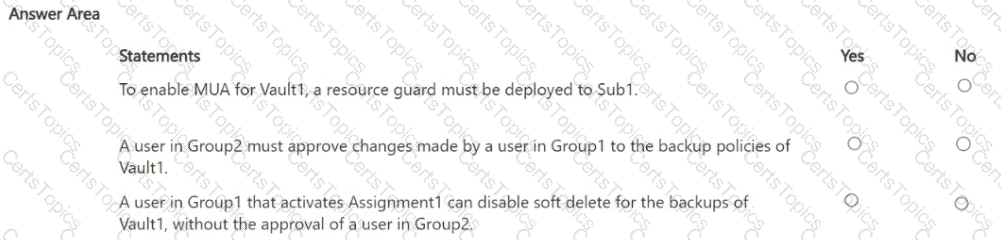
You perform the following actions:
• Configure multi-user authorization (MUA) for Vault1 by using a resource guard deployed to Sub2.
• Enable all available MUA controls for Vault1.
• In contoso.com, create a Privileged Identity Management (PIM) assignment named Assignment1.
• Configure Assignment1 to enable Group! to activate the Contributor role for Vault1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All the on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend configurations to meet the following requirements:
• Ensure that the security operations team can access the security logs and the operation logs.
• Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
You have an Azure SQL database named DB1 that contains customer information.
A team of database administrators has full access to DB1.
To address customer inquiries, operators in the customer service department use a custom web app named App1 to view the customer information.
You need to design a security strategy for D81. The solution must meet the following requirements:
• When the database administrators access DB1 by using SQL management tools, they must be prevented from viewing the content of the Credit Card attribute of each customer record.
• When the operators view customer records in App1, they must view only the last four digits of the Credit Card attribute.
What should you include in the design? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You have a Microsoft 365 subscription. You have an Azure subscription.
You need to implement a Microsoft Purview communication compliance solution for Microsoft Teams and Yammer. The solution must meet the following requirements:
• Assign compliance policies to Microsoft 365 groups based on custom Microsoft Exchange Online attributes.
• Minimize the number of compliance policies
• Minimize administrative effort
What should you include in the solution?
Your company has an on-premises network and an Azure subscription.
The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure.
You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network.
You need to recommend security standards that will allow the web apps to access the databases. The solution must minimize the number of open internet-accessible endpoints to the on-premises network.
What should you include in the recommendation?
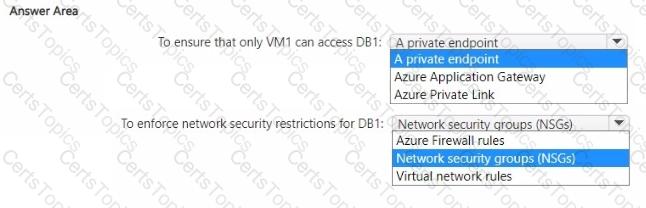
You have an Azure subscription that contains the resources shown in the following table.

You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Only the virtual machines that are connected to Subnet1 must be able to connect to D81.
• DB1 must be inaccessible from the internet
• Costs must be minimized.
What should you include in the recommendation? To answer, select the options in the answer area. NOTE: Each correct answer is worth one point.
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations. What should you recommend?
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags.
Does this meet the goal?
Your company has an on-premises network, an Azure subscription, and a Microsoft 365 E5 subscription. The company uses the following devices:
• Computers that run either Windows 10 or Windows 11
• Tablets and phones that run either Android or iOS
You need to recommend a solution to classify and encrypt sensitive Microsoft Office 365 data regardless of where the data is stored. What should you include in the recommendation?
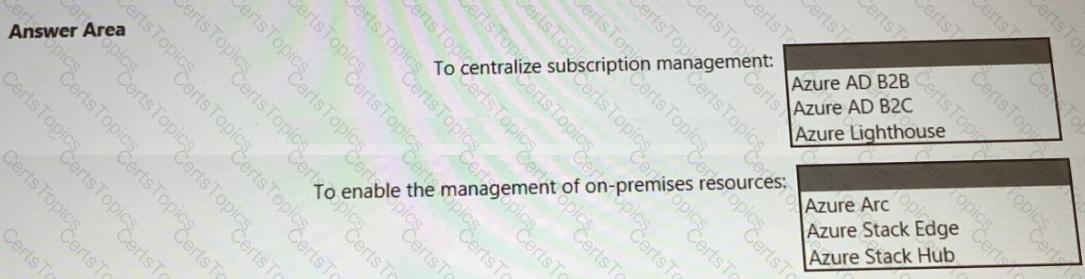
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
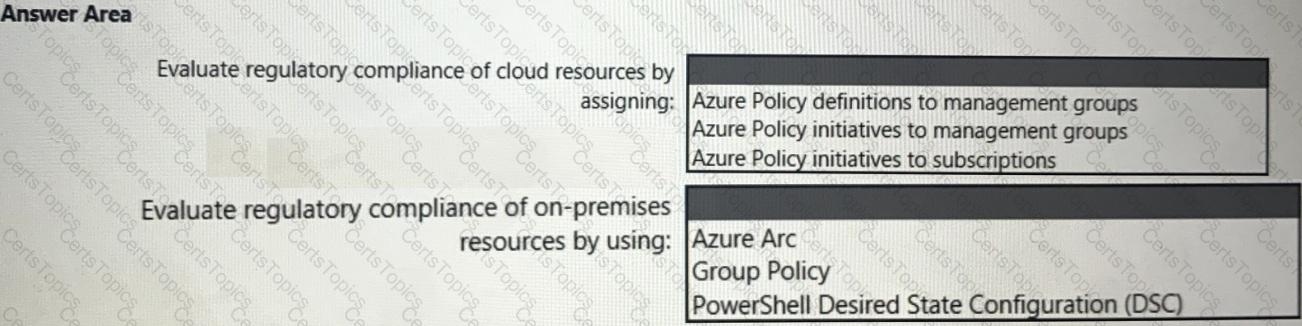
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
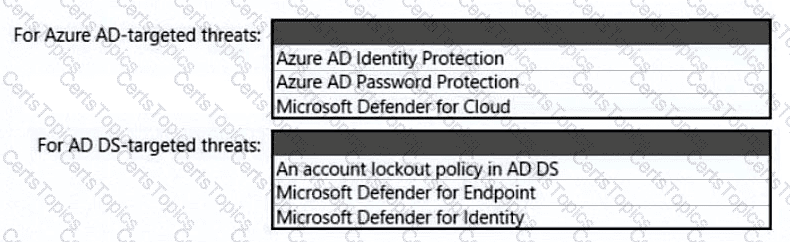
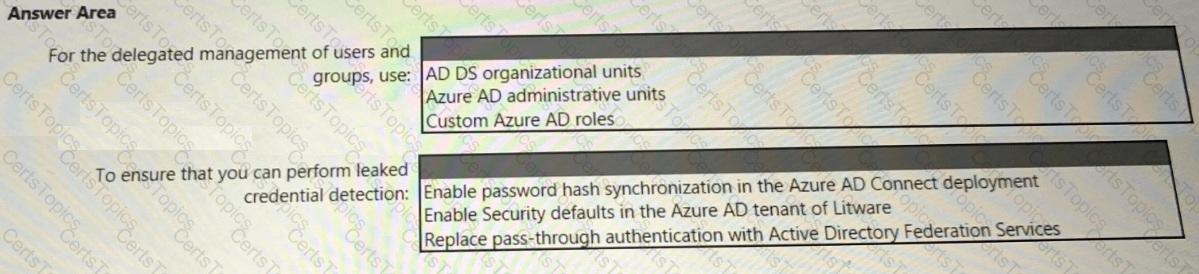
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
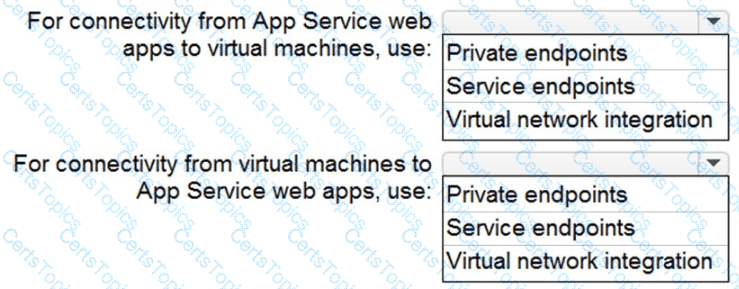
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
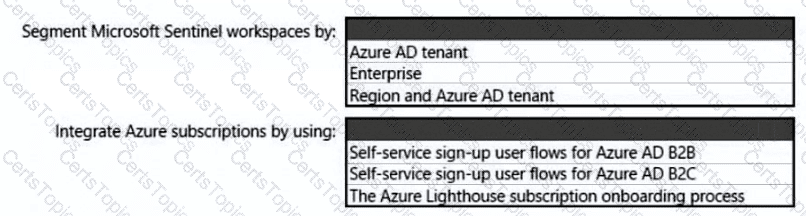
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.