You have a Microsoft Entra tenant named contoso.com and use Microsoft Intune. Each user in contoso.com has a Microsoft Entra ID P1 license and a Windows 11 device that has the Global Secure Access client deployed.
You plan to deploy the following configuration of Microsoft Entra Internet Access:
• Enable a baseline profile.
• Create a security profile named Profile` that has a priority of 300 and contains a single web content filtering policy named WCFPolicy configure WCFPolicy1 as follows:
o Set Action to allow.
o Include a single rule that has a fully qualified domain name (FQDN) destination of ‘. adatum.com.
• Link Profile1 to a Conditional Access policy named CAPolicy1, apply CAPolicy1 to all users, and grant access unless a user's device is noncompliant
You need to evaluate the impact of the planned deployment on traffic to the following resources:
•
•
Which two traffic scenarios will occur? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point
You have four Azure subscriptions named Sub1, Sub2, Sub3, and Sub4. Each subscription has a unique Microsoft Entra tenant that is linked to a Microsoft 365 subscription. Sub1 contains a user named User1.
You plan to implement Microsoft Sentinel.
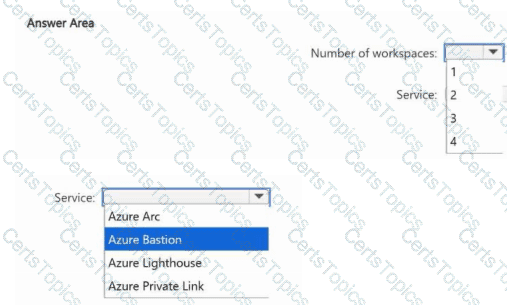
You need to ensure that User1 can monitor Microsoft Entra ID events and Microsoft 365 events for Sub2, Sub3, and Sub4 by using Microsoft Sentinel. The solution must minimize administrative effort.
What is the minimum number of Microsoft Sentinel workspaces you should create, and which Azure service should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company develops several applications that are accessed as custom enterprise applications in Azure Active Directory (Azure AD). You need to recommend a solution to prevent users on a specific list of countries from connecting to the applications. What should you include in the recommendation?
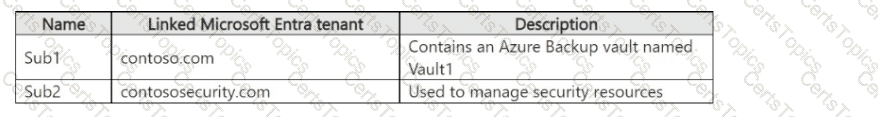
You have the Azure subscriptions shown in the following table.
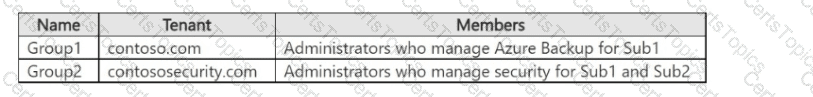
The tenants contain the groups shown in the following table.
You perform the following actions:
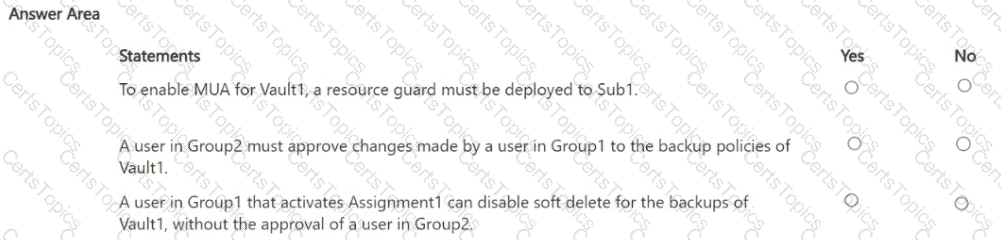
• Configure multi-user authorization (MUA) for Vault1 by using a resource guard deployed to Sub2.
• Enable all available MUA controls for Vault1.
• In contoso.com, create a Privileged Identity Management (PIM) assignment named Assignment1.
• Configure Assignment1 to enable Group! to activate the Contributor role for Vault1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.