What is a function of the metadata service in an object-based storage device (OSD)?
How is NVMe used to connect a host to M.2 storage devices?
What is a benefit of unified storage systems?
What does the “variability” characteristic of big data signify?
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
Which process eliminates data redundancy in a data set?
Refer to the exhibit:
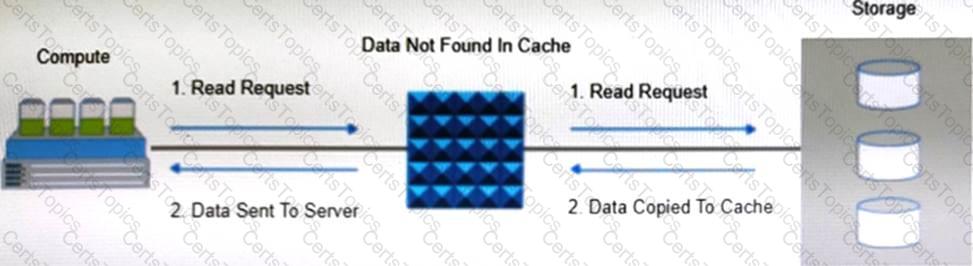
Which operation is represented?
What is a purpose of the policy engine in a data archiving environment?
In a data center environment, what is an advantage of using parity-based RAID protection over mirroring?
Cloud tiering is the part of which tier?
A customer uses FCIP to connect local and remote FC SANs. The remote SAN is continuously replicated to, and used to store
daily backup data. Latency over the IP WAN increases to unacceptable levels during peak replication periods. No other data
transfer services using the WAN experience the same latency problem.
What is the likely cause of the data replication performance issue?
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
What is the functionality of the application server in a Mobile Device Management?
A backup administrator has defined a backup policy The policy requires full backups to be performed at 9 PM every Sunday and incremental backups performed at 9 PM the remaining days If files were accidentally deleted Thursday morning, how many backup copies are required to restore the files?
What is a function of a continuous data protection (CDP) appliance?
What is true about scale-out NAS storage architecture?
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
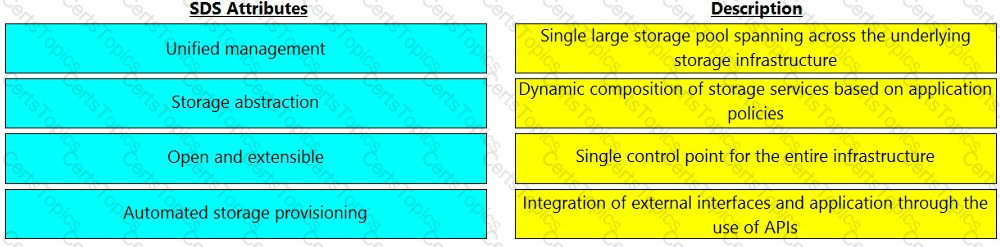
Match the software-defined storage (SDS) attributes with their respective description.
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called'?
What is the maximum number of VLANs that can be supported with one VLAN tag field?
What is a function of VM hardening?