An administrator must rename the administrator account on a Windows desktop. Which tool is best for this?
A user is unable to upload files to the corporate servers from their mobile phone when outside the office, but uploading files works without issue in the office. The user saw an error notification but dismissed it. Which of the following should a technician do to determine the root cause?
A popular game frequently freezes and crashes on a mobile phone. The user updates the OS, but the issue persists. The device is one year old and has plenty of free storage space. Which of the following is the most appropriate first step to troubleshoot this issue?
A network technician notices that most of the company's network switches are now end-of-life and need to be upgraded. What should the technician do first?
A user takes an iOS-based smartphone that is performing slowly to a repair shop. A shop technician finds the following information:
Battery charge: 25%
Battery health: 90%
Hot-spot: On
Mobile reception: |||
Roaming: Off
Used space: 63.76GB/64GB
Which of the following is the cause of the issue?
A help desk technician needs to remove RAM from retired workstations and upgrade other workstations that have applications that use more memory with this RAM. Which of the following actions would the technician most likely take?
A help desk support technician needs to ensure that the documentation for a software deployment is up to date. The documentation must also include all necessary information for future troubleshooting. Which of the following should the technician include?
Which of the following security technologies is designed to enable security visibility and respond to traffic outside of the host and at the network level?
What is found in an MSDS (Material Safety Data Sheet) for a battery backup?
A Microsoft OS laptop user frequently forgets their password. Which alternative login method should a technician enable?
A technician inspects the following workstation configuration:
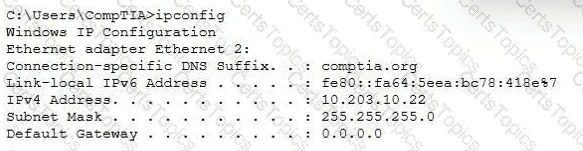
The workstation is unable to open any external websites. The browser displays an error message that says that the site cannot be reached.
Which of the following file types allows macOS users to uninstall software completely by placing the file in the trash?
A technician is securing a newly deployed workstation. Only authorized users should access it. Which actions should the technician take? (Select two)
A senior administrator asks a help desk technician to run a set of commands on a remote network switch. After running the commands, the technician needs to collect the output and provide it to the administrator. Which of the following should the technician use to fulfill the administrator's request?
Which of the following describes an attack in which an attacker sets up a rogue AP that tricks users into connecting to the rogue AP instead of the legitimate network?
An organization is experiencing an increased number of issues. A technician notices applications that are not installed by default. Users are reporting an increased number of system prompts for software licensing. Which of the following would the security team most likely do to remediate the root cause?
MFA for a custom web application on a user's smartphone is no longer working. The last time the user remembered it working was before taking a vacation to another country. Which of the following should the technician do first?
A user switches from Linux to Windows and tries to migrate data using an external USB drive. Windows prompts that the device must be formatted. It works fine on Linux. What should the user do?
A customer’s laptop will not turn on. The customer is distraught and panicking because the laptop contains family pictures that can never be replaced. Which of the following communication techniques is most important for the technician to demonstrate in this situation?
A user is working from home and is unable to access work files on a company laptop. Which of the following should a technician configure to fix the network access issue?
An end user wants to have a sales printer added to their computer. The printer is on the domain. Which of the following is the best method for the technician to add the printer?
Technicians are failing to document user contact information, device asset tags, and a clear description of each issue in the ticketing system. What should the help desk management implement?
Due to recent security issues, the finance department requires a shorter screensaver timeout. Which of the following should a technician use to accomplish this task?
A help desk technician recently installed an SSH client on a workstation in order to access remote servers. What does this enable?
A project team needs special access on a shared repository to add new content, edit existing content, and prevent content deletion. Which of the following should an administrator do to configure this setup with the least amount of effort?
Which of the following is used in addition to a password to implement MFA?
A Windows 11 Home device is receiving constant pop-ups about an urgent need to update antivirus software to remove a detected threat. The user has been clicking the "X" button in the window frame but it always reappears. The pop-up includes an "OK" button to install the update and remove the threat. Which of the following should the user do next?
An end user's laptop is having network drive connectivity issues in the office. The end user submits a help desk ticket, and a support technician is able to establish a remote connection and fix the issue. The following day, however, the network drive is disconnected again. Which of the following should the technician do next?
A technician installs VPN client software that has a software bug from the vendor. After the vendor releases an update to the software, the technician attempts to reinstall the software but keeps getting an error message that the network adapter for the VPN already exists. Which of the following should the technician do next to mitigate this issue?
Which of the following is the best reason for a network engineering team to provide a help desk technician with IP addressing information to use on workstations being deployed in a secure network segment?
A technician notices that the weekly backup is taking too long to complete. The daily backups are incremental. Which of the following would most likely resolve the issue?
A user needs to test several software replacement possibilities. Part of the process involves installing the different software options on a corporate-imaged sandboxed PC. Which of the following is the best option to allow the user to install the required software?
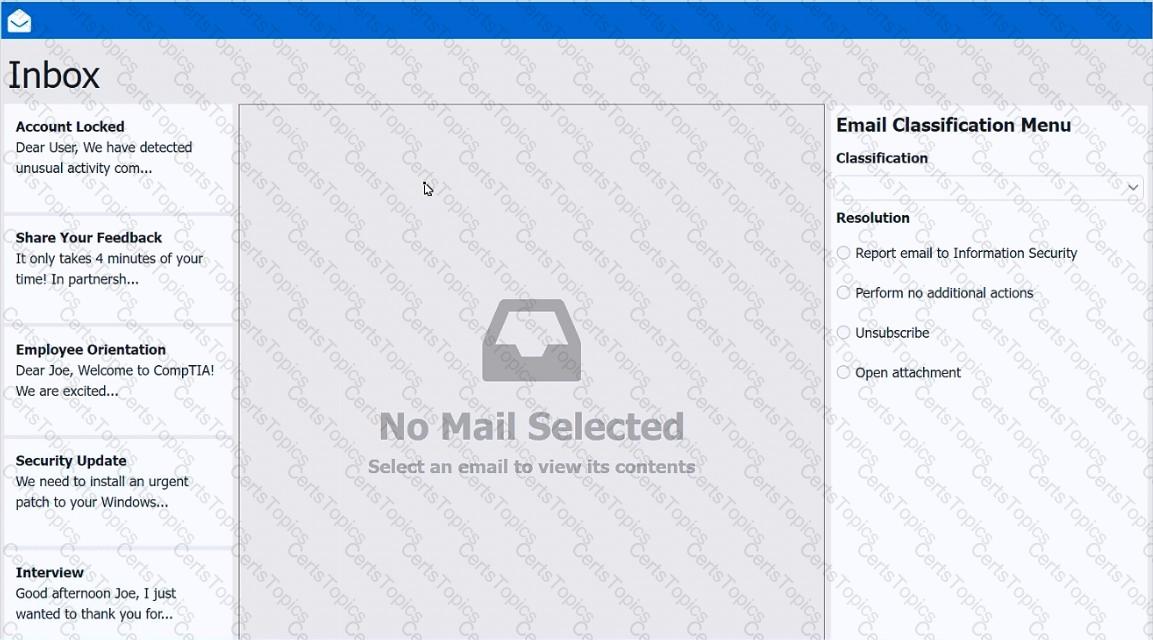
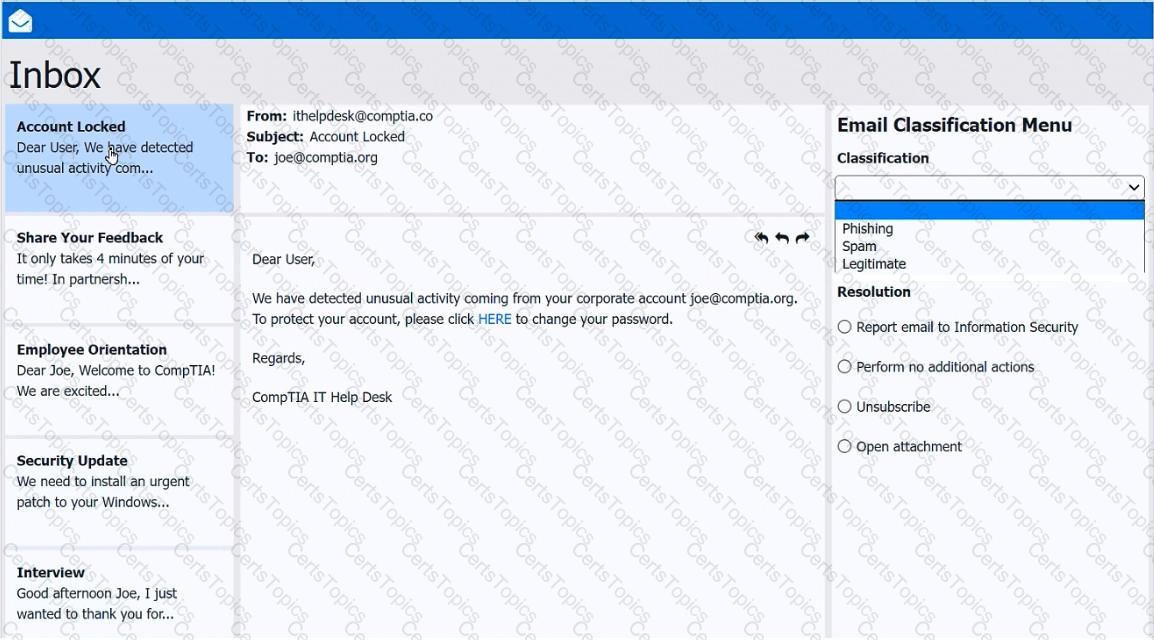
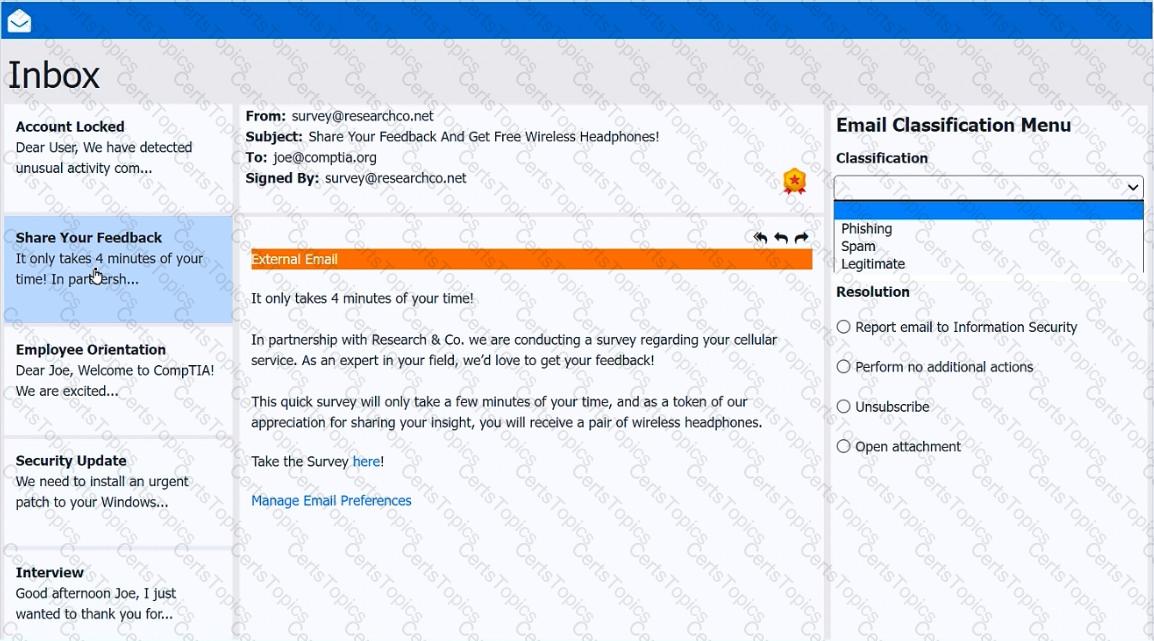
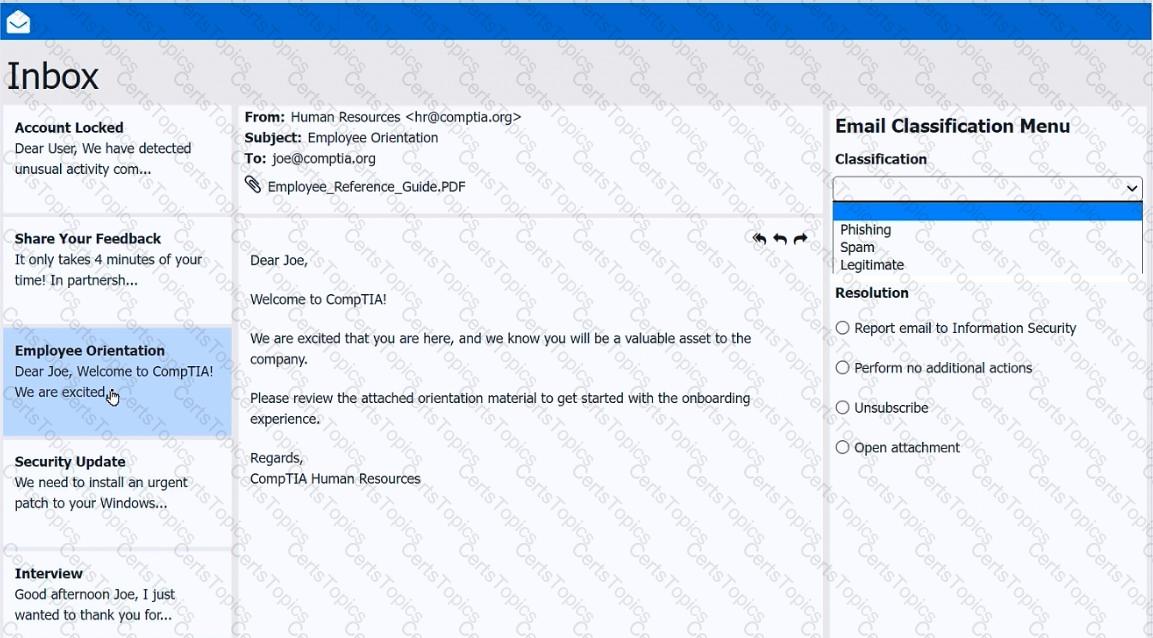
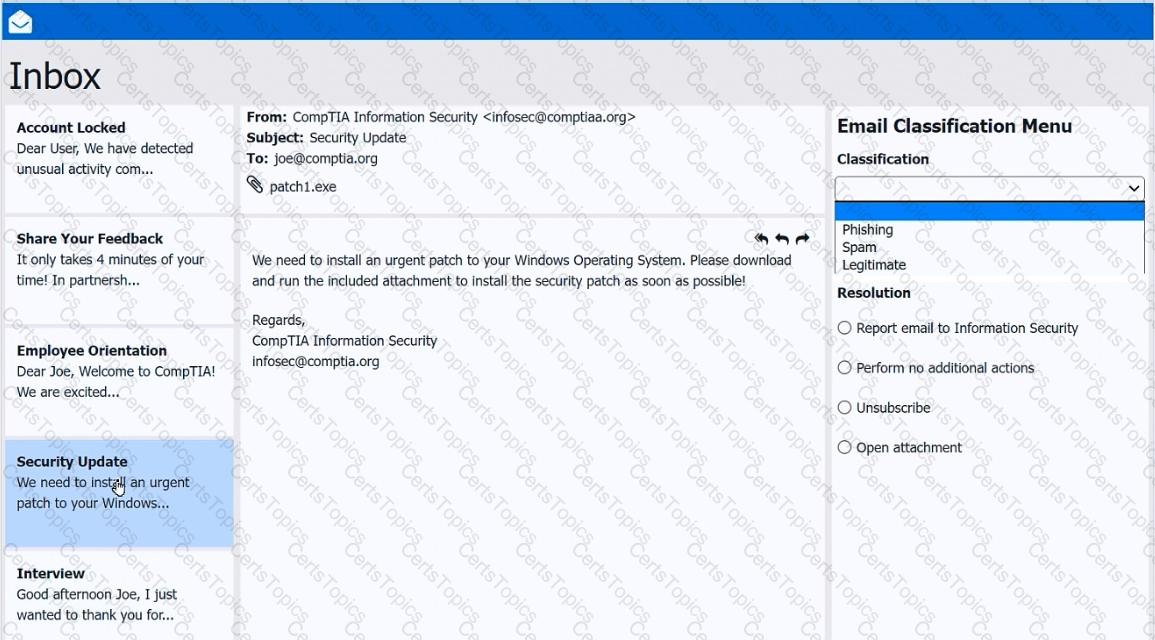
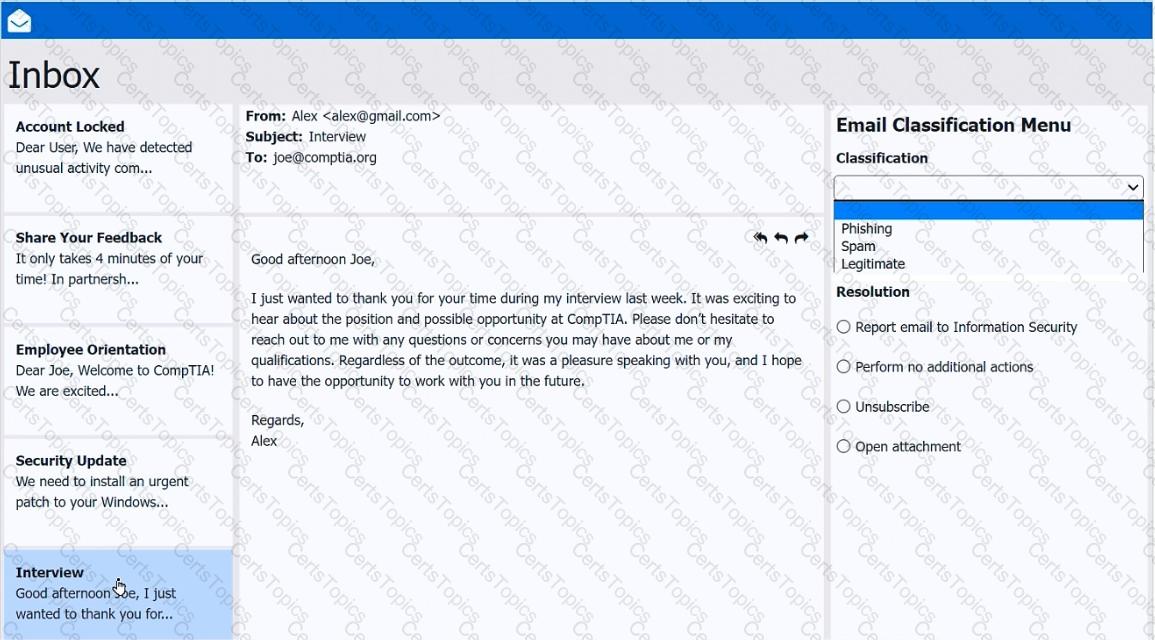
As a corporate technician, you are asked to evaluate several suspect email messages on a client's computer. Corporate policy requires the following:
>All phishing attempts must be reported.
>Future spam emails to users must be prevented.
INSTRUCTIONS
Review each email and perform the following within the email:
>Classify the emails
>Identify suspicious items, if applicable, in each email
>Select the appropriate resolution
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
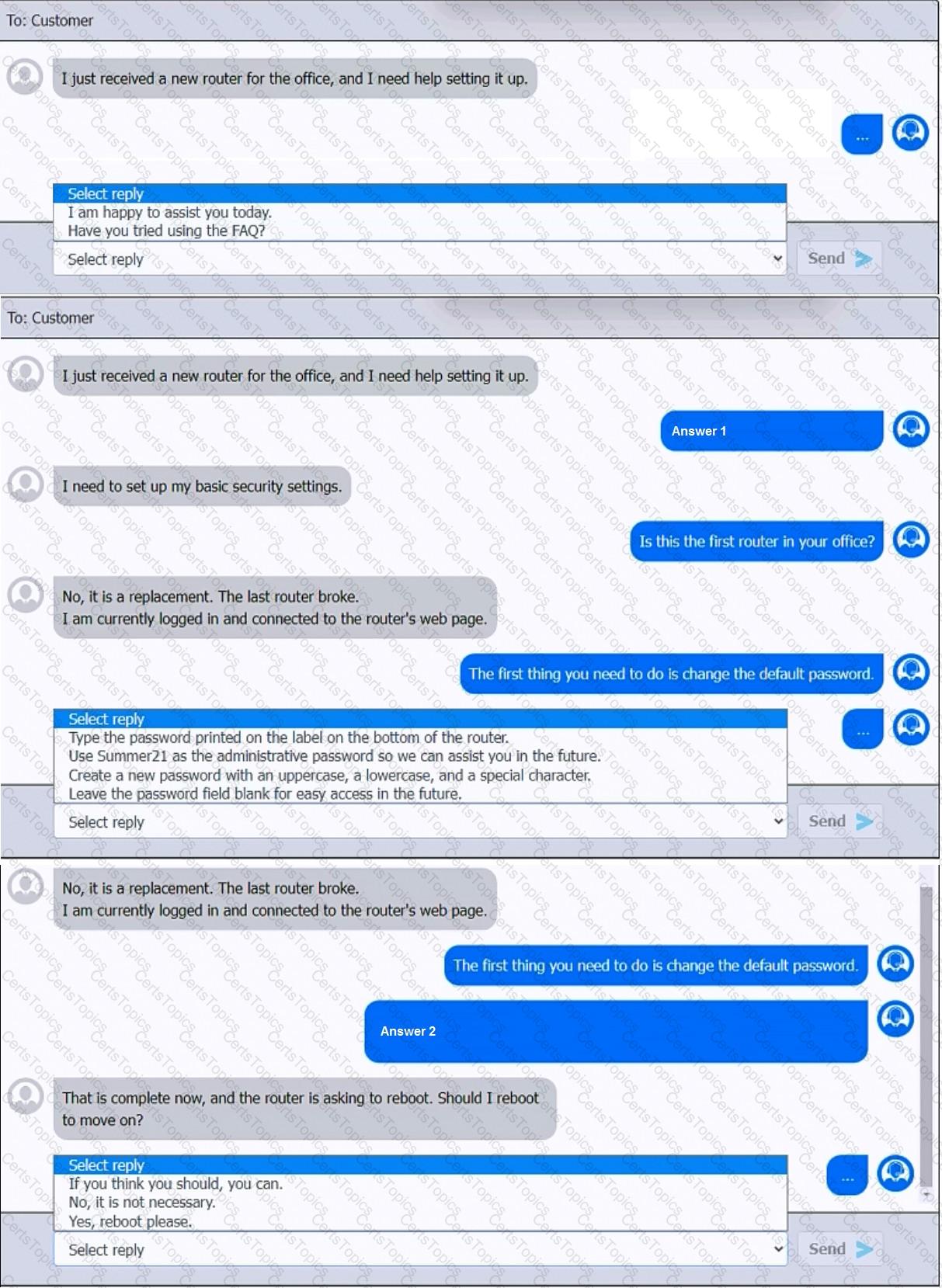
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
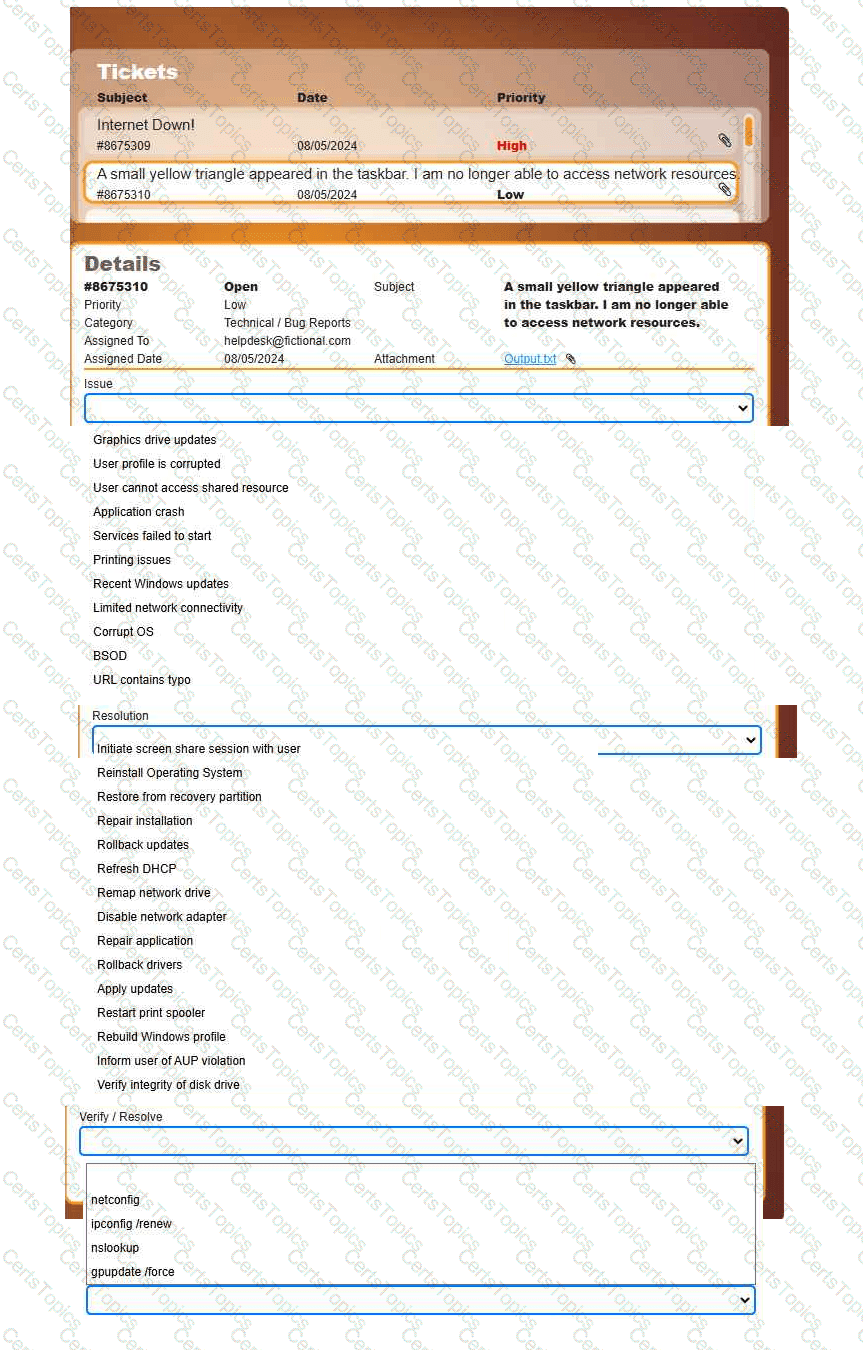
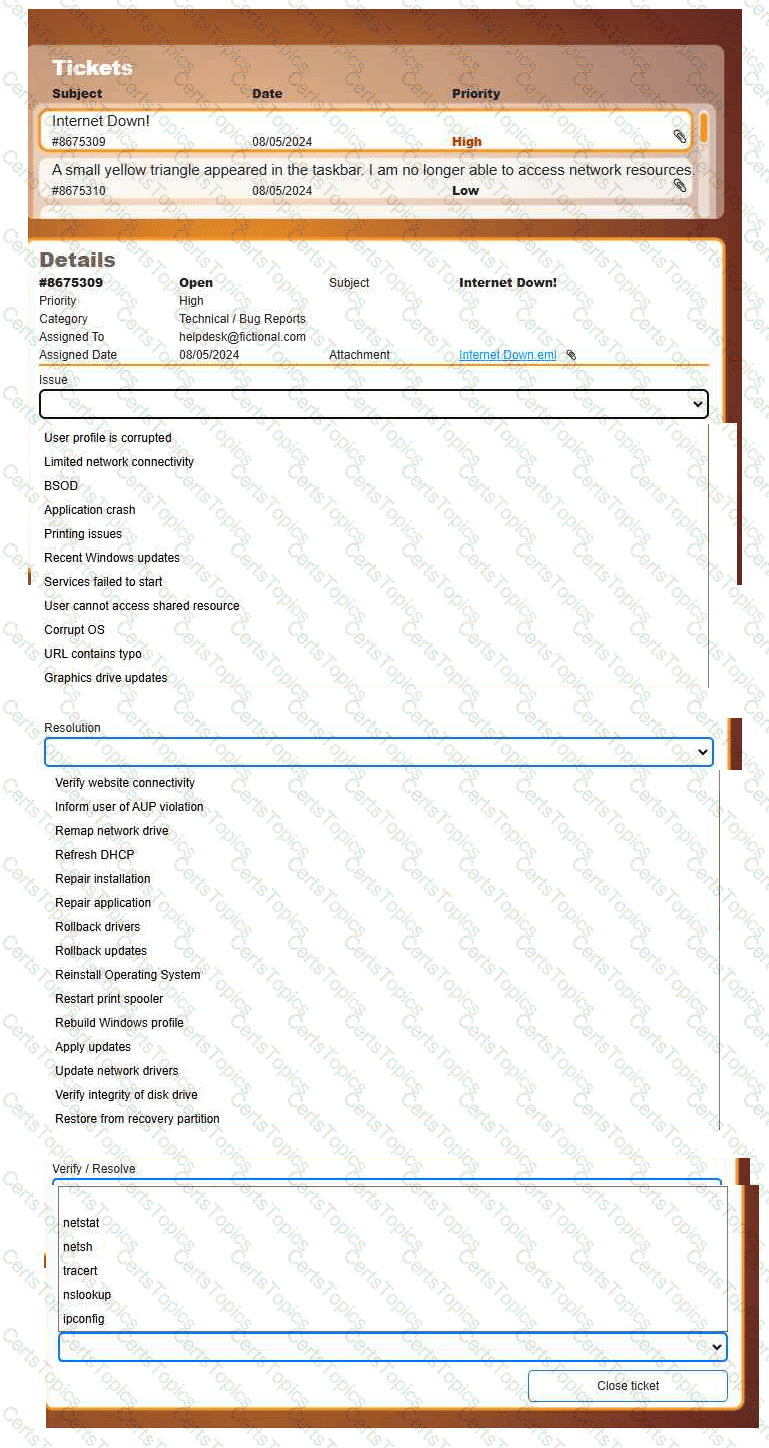
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
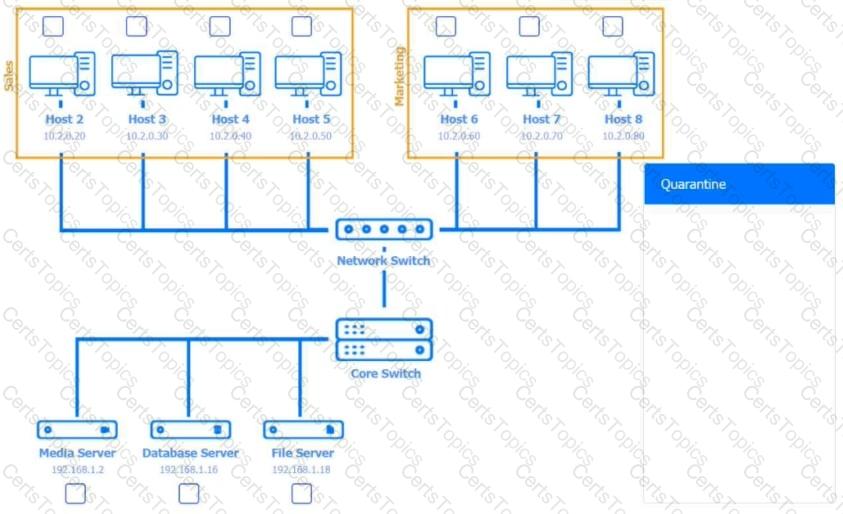
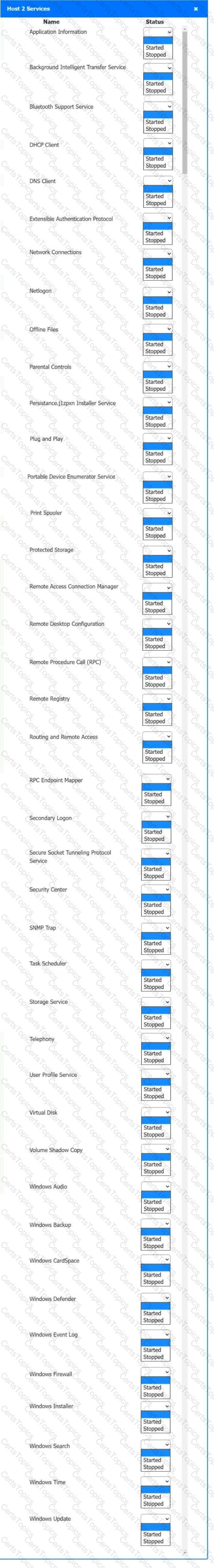
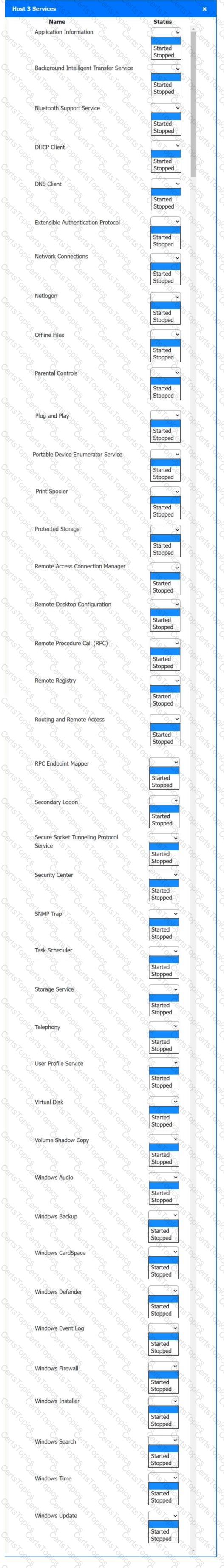
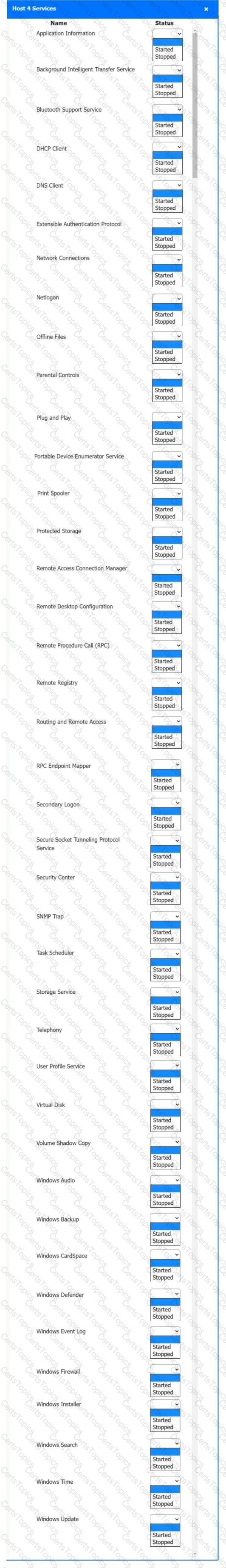
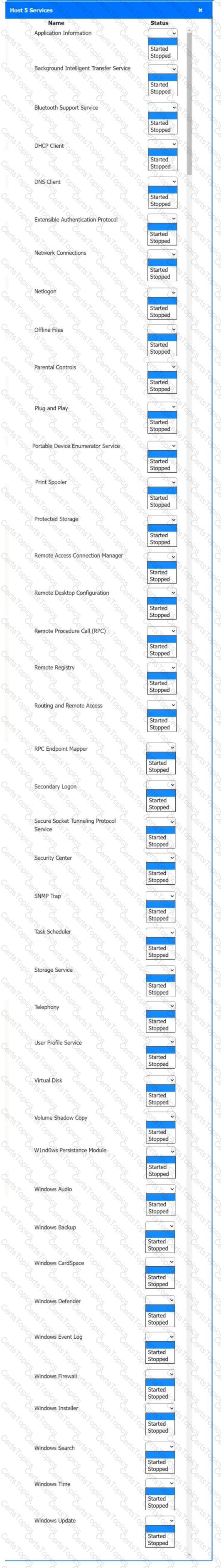
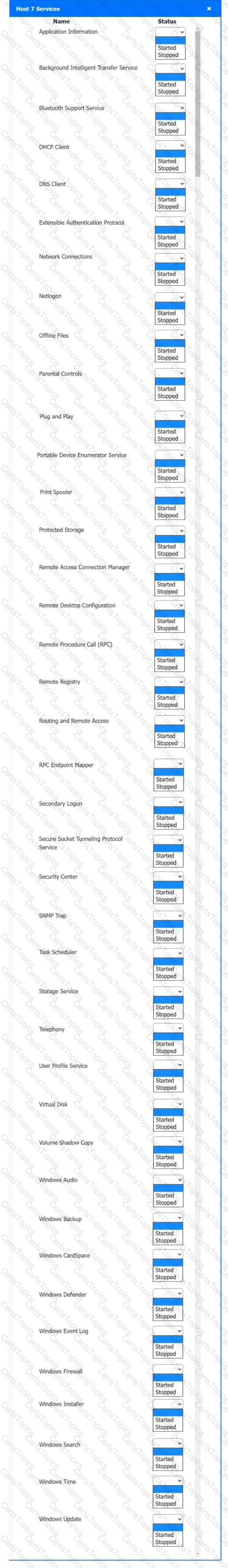
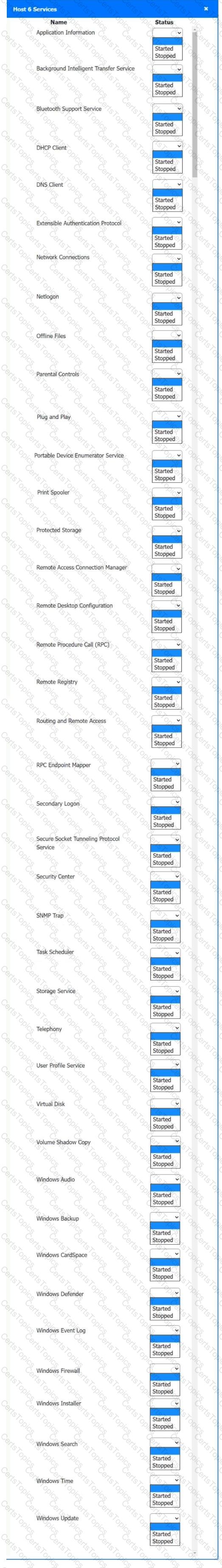
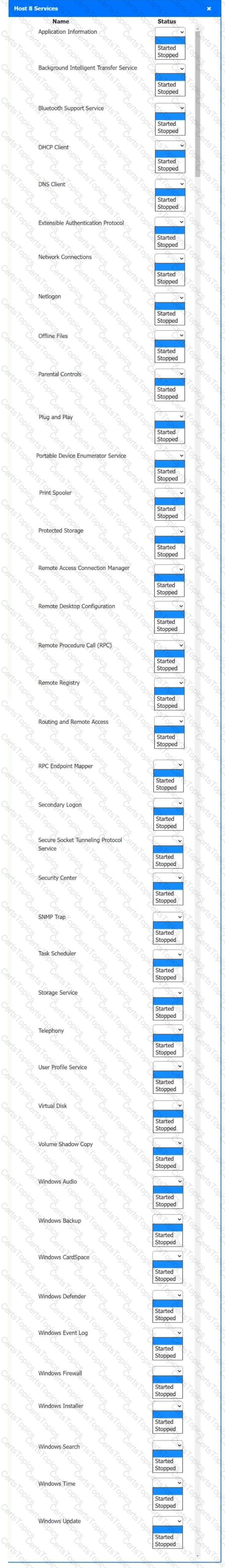
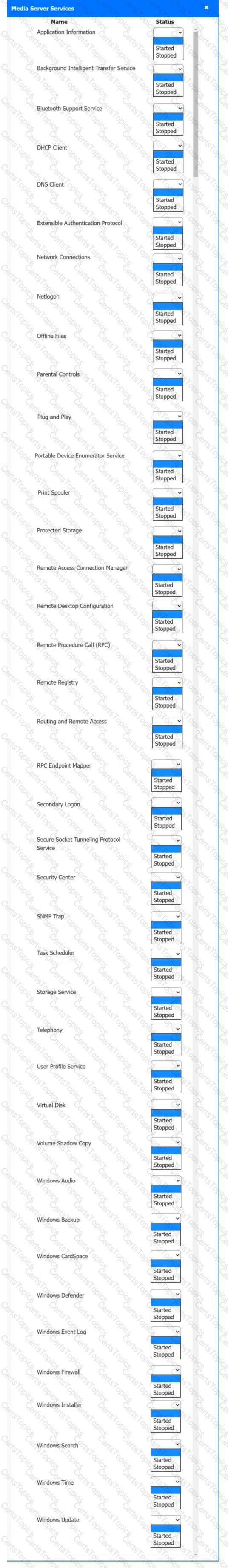
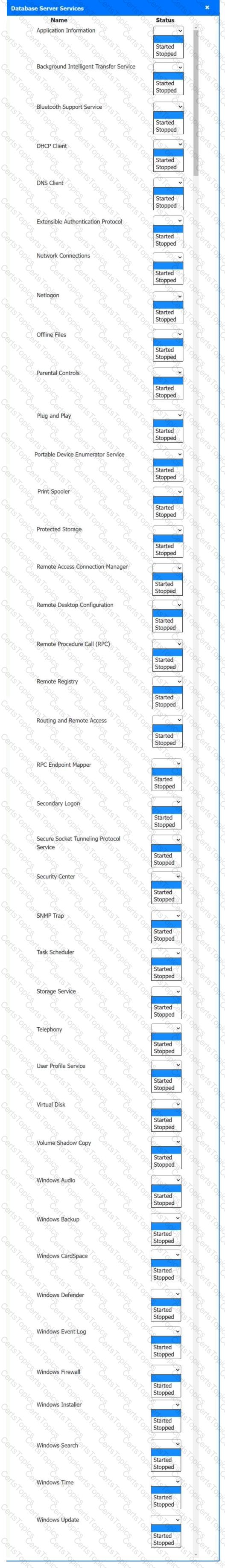
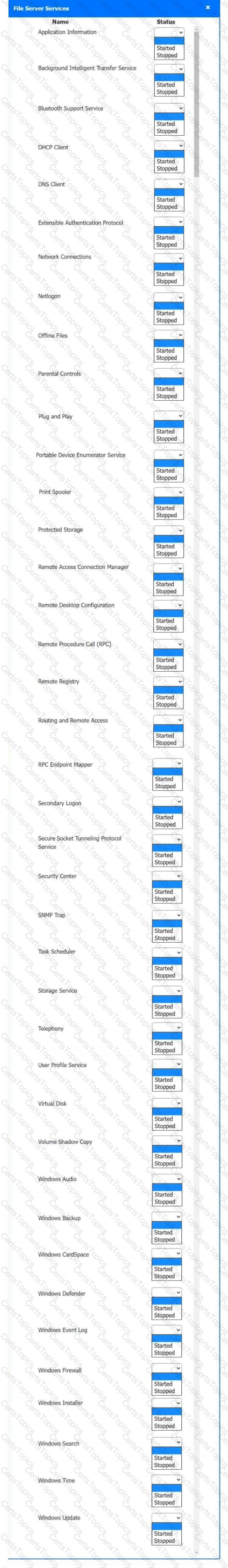
Multiple users are reporting audio issues as well as performance issues after downloading unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users’ audio issues are resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
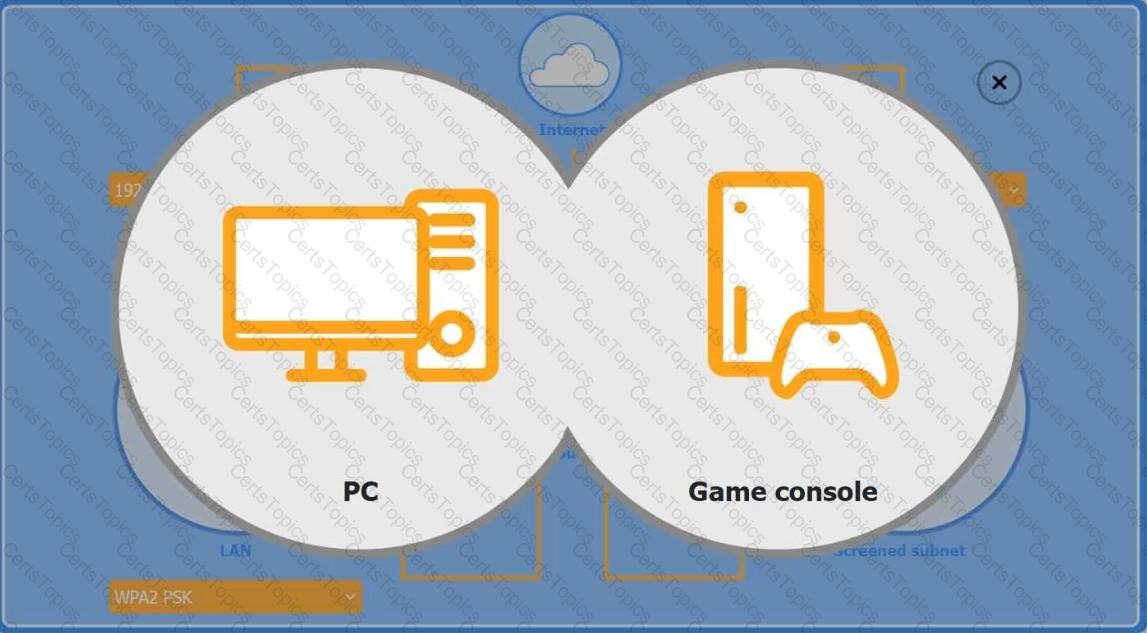
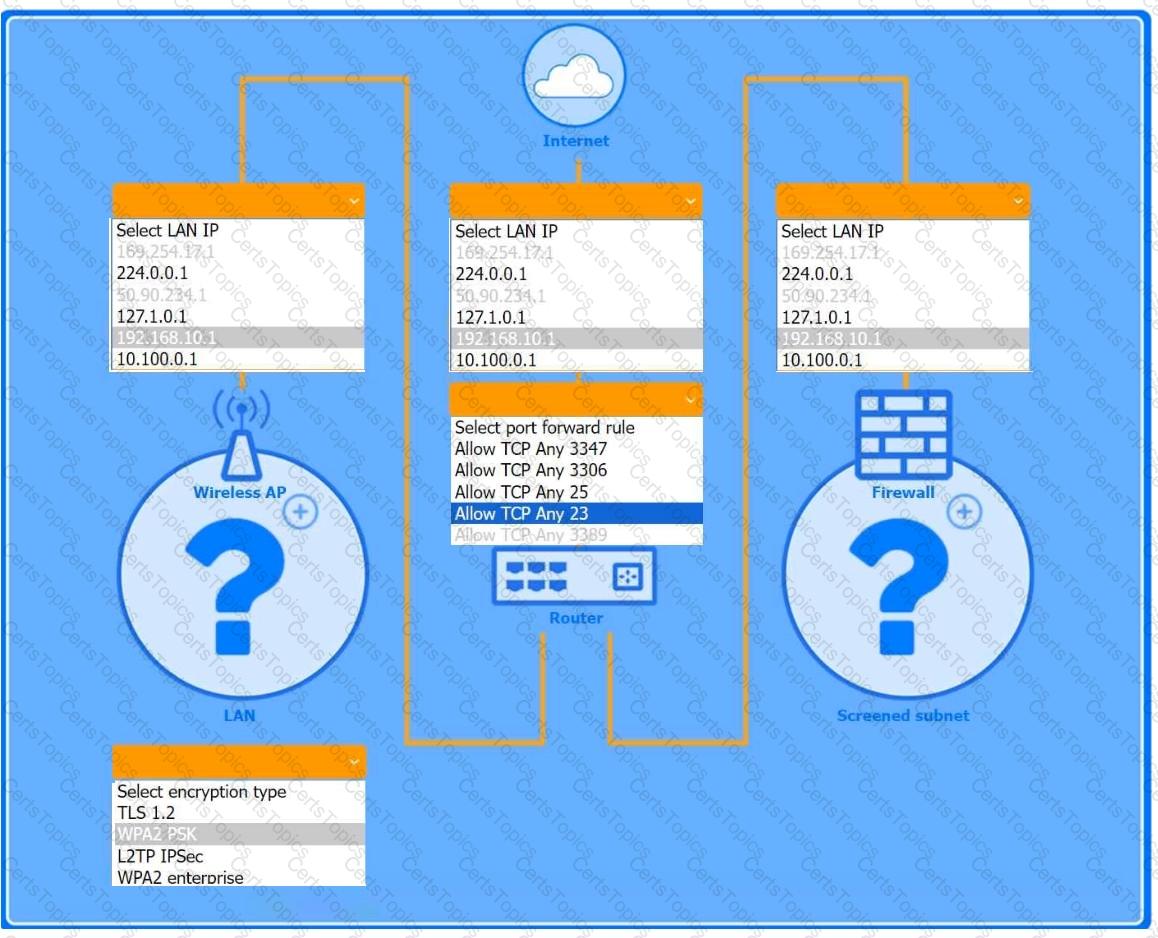
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used.
Then, click the + sign to place each device in its appropriate location.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Wireless AP LAN
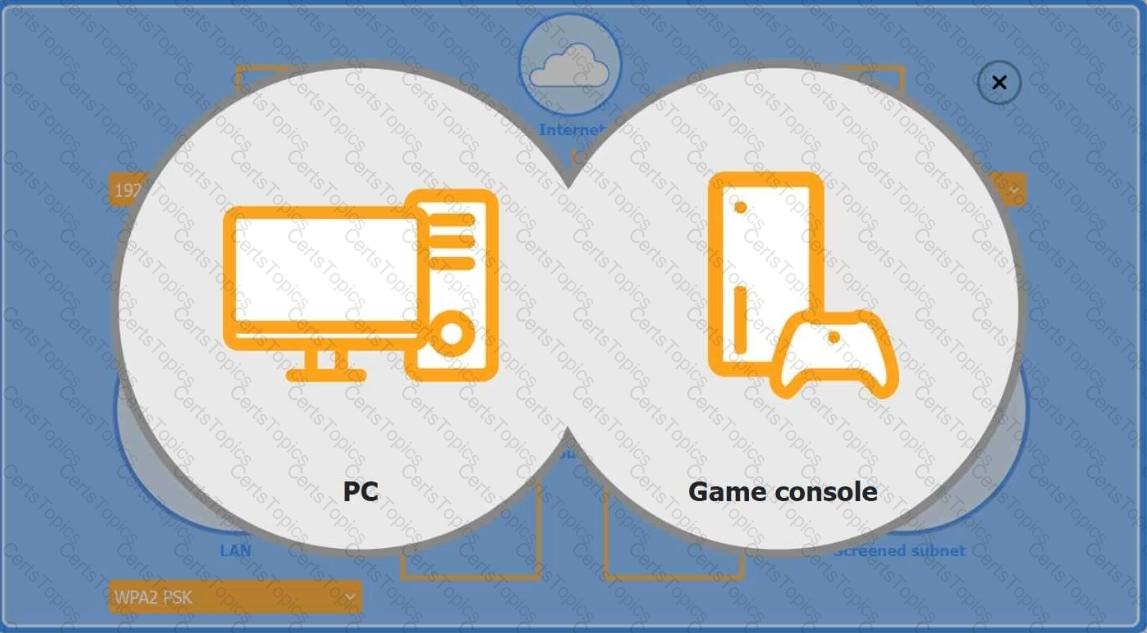
Firewall Screened Subnet
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
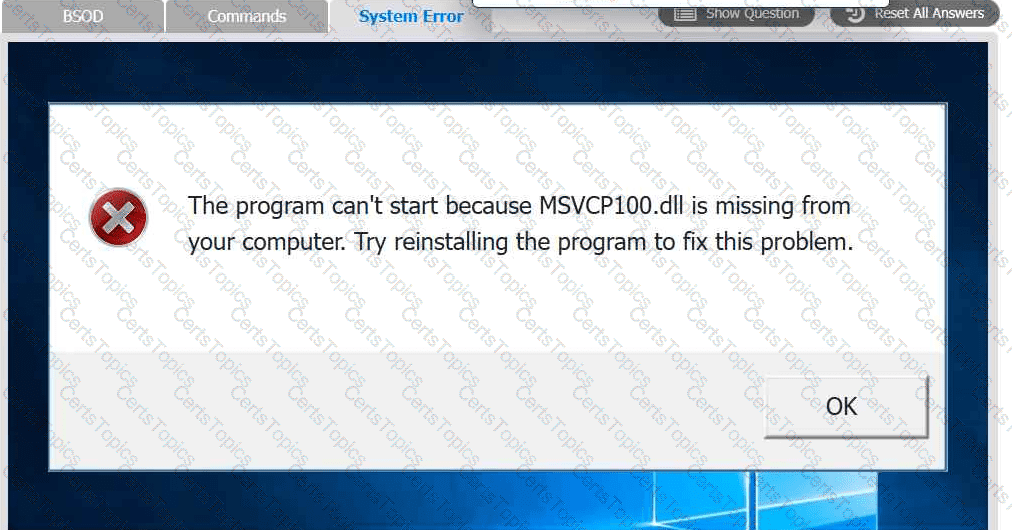
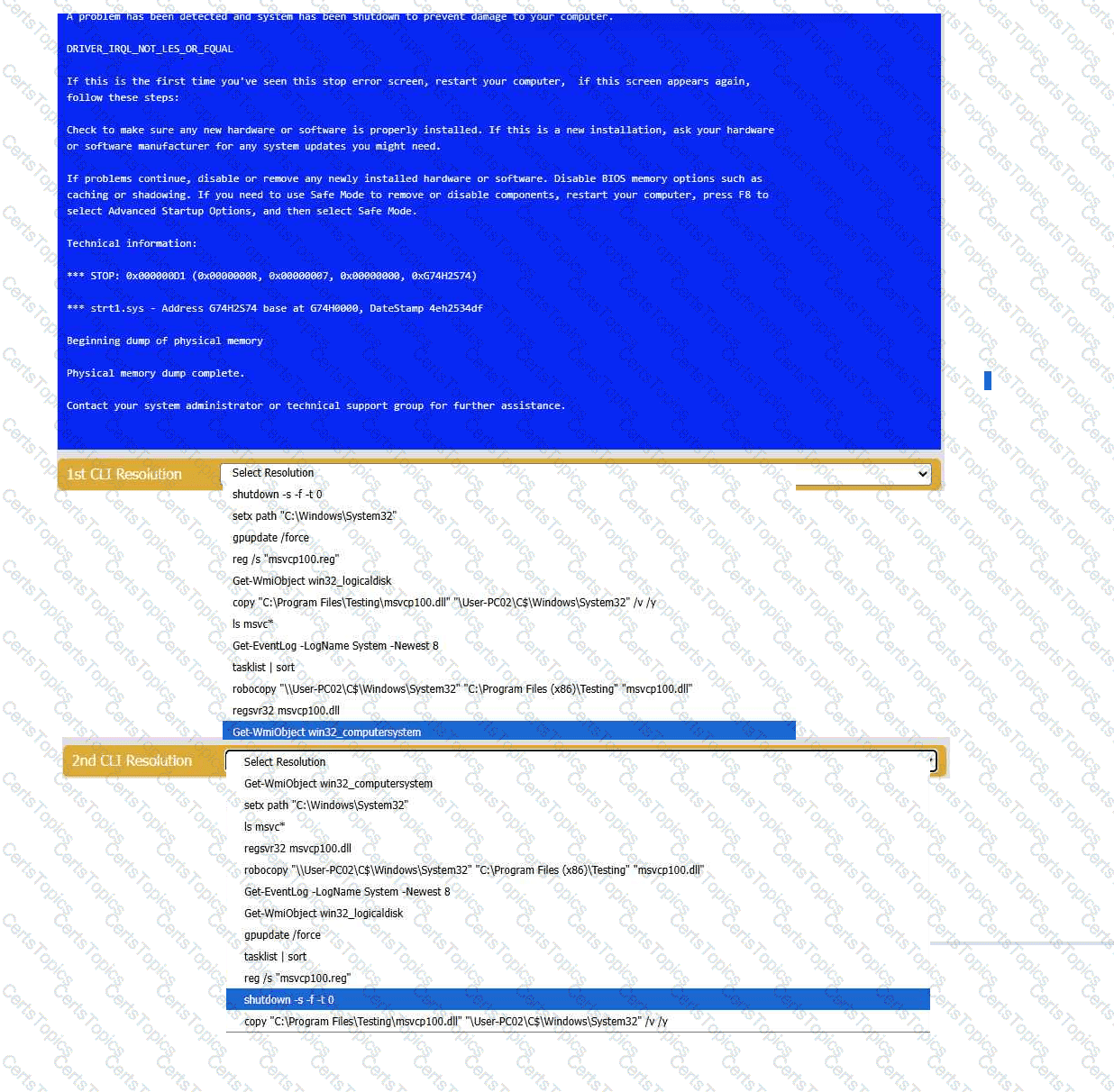
A user reports that after a recent software deployment to upgrade the Testing application, they can no longer use it. However, other employees can successfully
use the Testing program.
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve
any issues discovered by selecting the:
· First command to resolve the issue
· Second command to resolve the issue