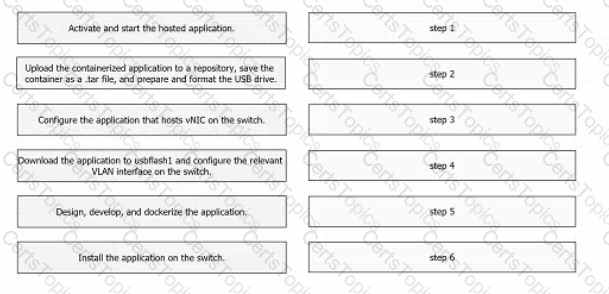
Drag and drop the steps from the left into the order on the right to host a Docker-contained application on a Cisco Catalyst 9000 Series Switch.
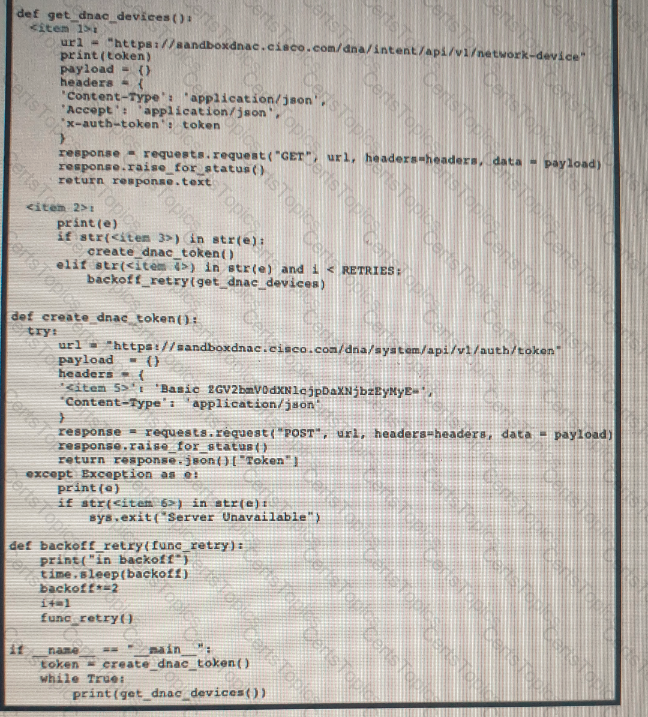
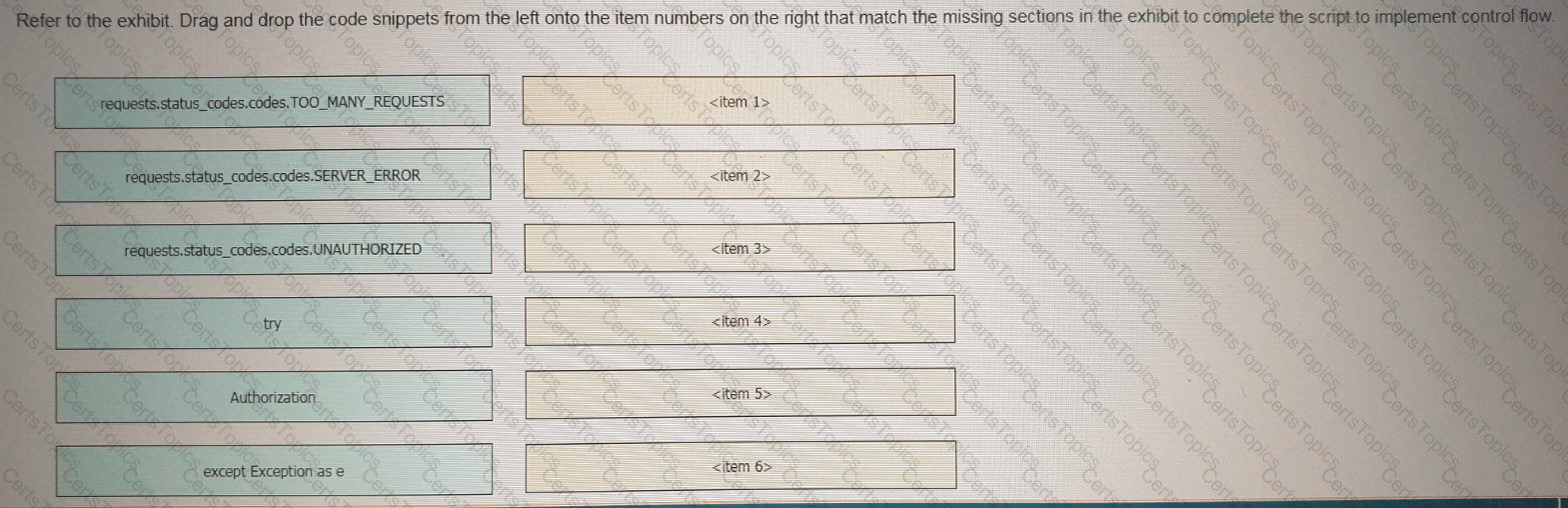
Refer to the exhibit Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
Refer to the exhibit.
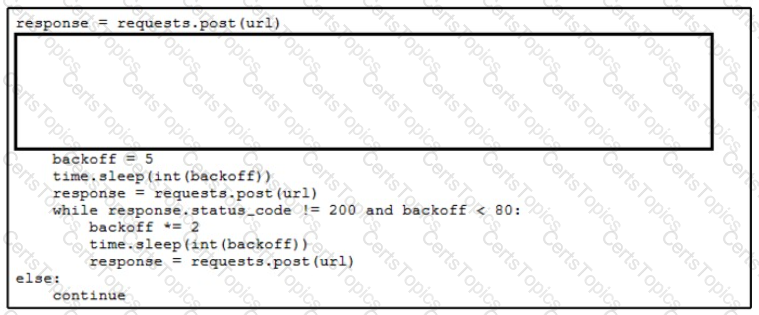
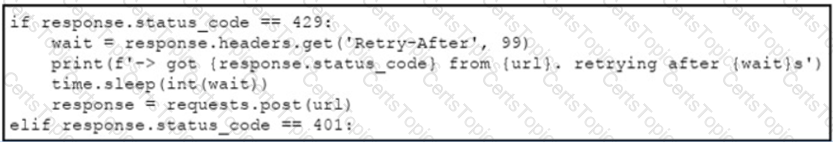
An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present. Which code snippet must be placed into the blank in the code to complete the API request?
A)
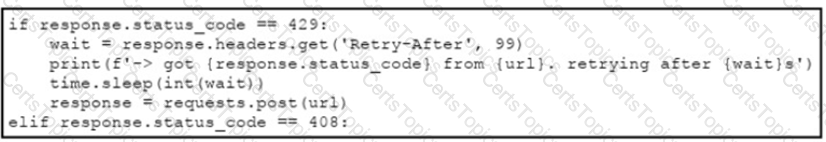
B)
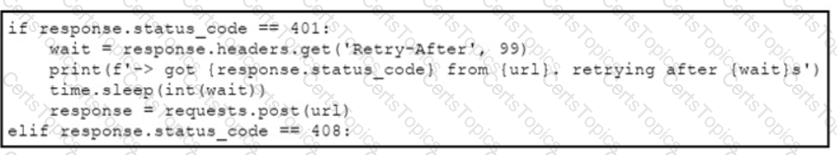
C)

D)
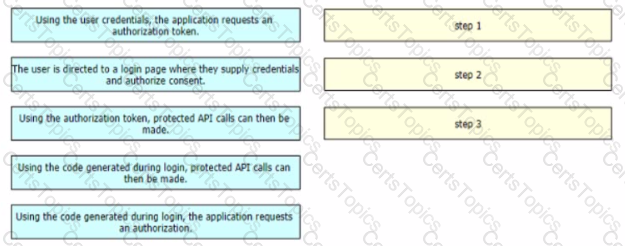
Drag and drop the steps from the left into the sequence on the fight to implement an OAuth2 three-legged authorization code flow grant type in an application Not all options are used.
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
Refer to the exhibit.
A)
B)
C)
D)
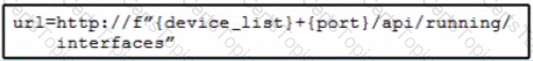
An engineer must enable an SSID in a Meraki network. Which request accomplishes this task?
What is submitted when an SSL certificate is requested?
What is the result of a successful OAuth2 authorization grant flow?
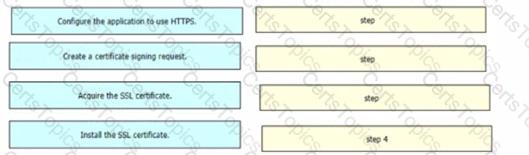
An engineer is developing a web-based application that will be used as a central repository for the HR department The application needs to authenticate user access and encrypt communication. Drag and drop the steps from the left into the order on the right to install an application-specific SSL certificate.
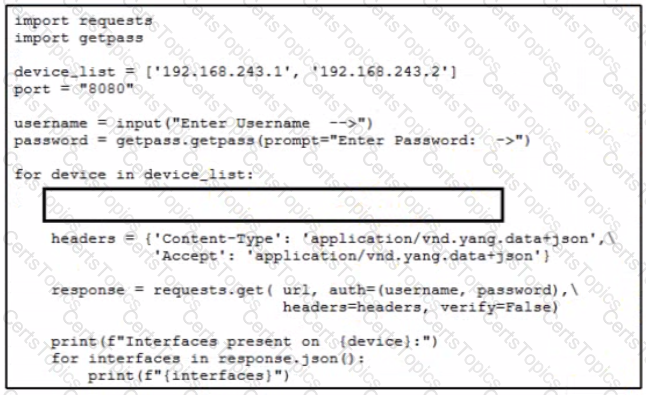
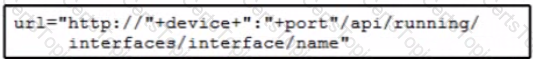
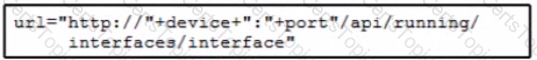
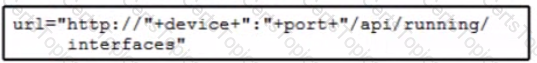
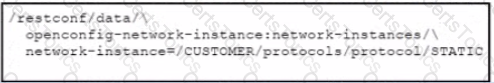
Refer to the exhibit. Which URI string retrieves configured static routes in a VRF named CUSTOMER from a RESTCONF-enabled device?
A)

B)
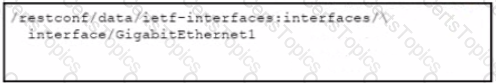
C)

D)
Refer to the exhibit.


An engineer writes a script to retrieve data from a REST API and must build support for cases where the response that contains data from the server may take a longer time than normal Which code must be added to the snippet where the code is missing to catch such a timeout?
An engineer needs to automate the configuration on a Cisco NX-OS switch. The solution must meet these requirements:
•Ansible is used
•The transport protocol is encrypted
•Support for Asynchronous requests.
Which two access mechanisms must be used? (Choose two.)
Given an application that implements a basic search function as Well as a video upload function , which two load-balancing approaches
optimize the application's user experience? (Choose two.)
Refer to the exhibit.
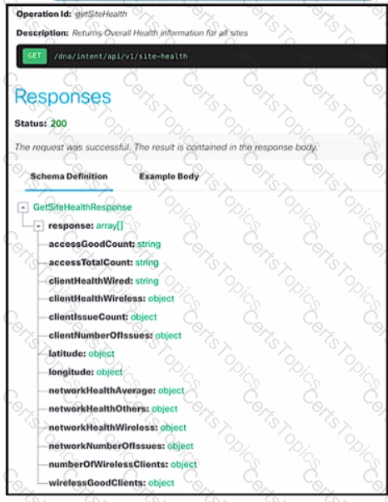
A developer is creating a Python script by using Cisco DNA Center APIs Drag and drop the code from the bottom onto the box where the code is missing in the Python script to retrieve and display wireless health information for each site Not all options are used.

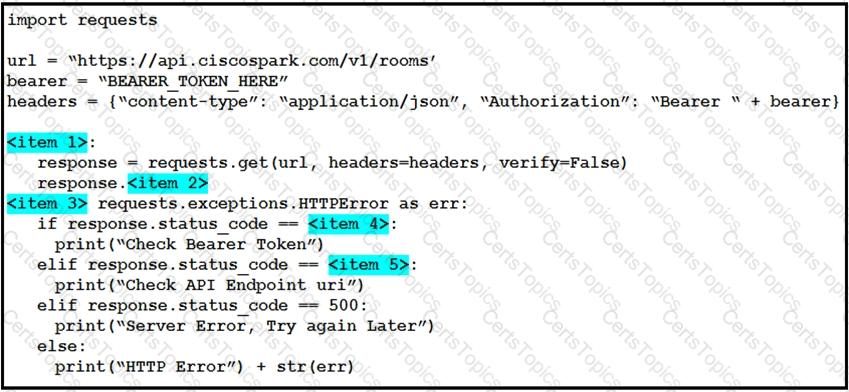
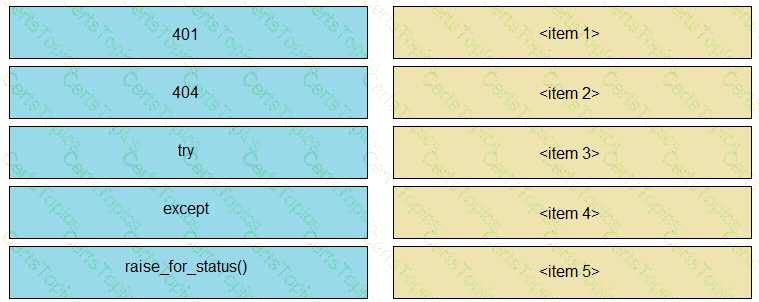
A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, and gracefully handle and print the errors it receives. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script.
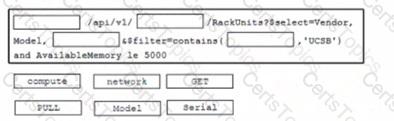
Click on the resource lab in the top left comer to view resources to help with this question An engineer is managing a data center with 6000 Cisco UCS servers installed and running The engineer is asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB Drag and drop the code from the bottom onto the blanks in the code snippet to construct a REST API call to accomplish this task Not all options are used.
How is client code that consumes gRPC telemetry implemented, assuming that the preferred language is able to be chosen?
Refer to the exhibit.
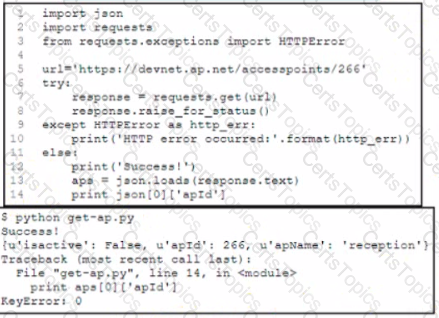
A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points The developer is retrieving an access point ID by using a REST API The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14?
A)

B)

C)

D)

Refer to the exhibit.

An application has been created to serve a whole enterprise. Based on use and department requirements, changes are requested on a quarterly basis. When evaluating the application design, which two actions improve code maintainability?
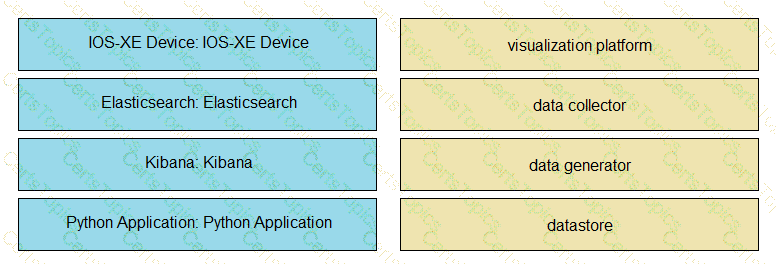
An application is being built to collect and display telemetry streaming data. Drag and drop the elements of this stack from the left onto the correct element functions on the right.
What is an effective logging strategy according 10 the 12-factor app tenets?
Which two statements are considered best practices according to the 12-factor app methodology for application design? (Choose two.)
Refer to the exhibit.
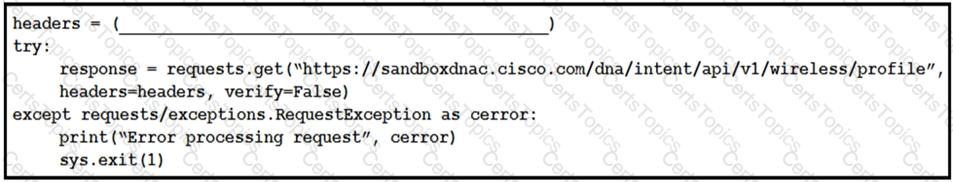
Which code snippet is required in the headers to successfully authorize wireless information from Cisco DNA Center?
An engineer is developing a Docket container for an application in Python For security reasons the application needs to be accessible on port 5001 only Which line should be added to the dockerfile m order to accomplish this?
A developer releases a new application for network automation of Cisco devices deployed m a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability-driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
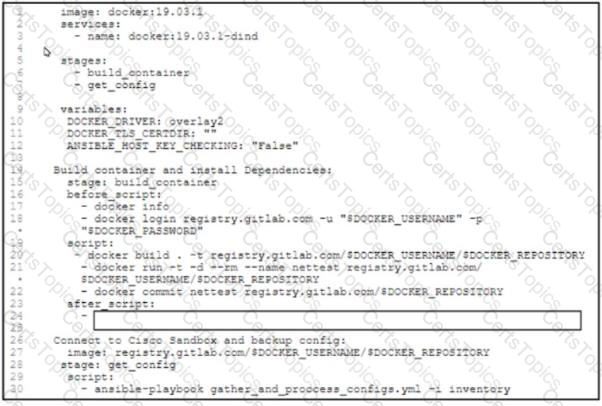
Refer to the exhibit. A developer wants to automatically deploy infrastructure for a containerized application. A .gitlab-ci.yml file must describe a pipeline that builds a container based on a supplied Dockerfile and executes an Ansible playbook on the configured container. What must be added where the code S missing to complete the script?
A)

B)

C)

D)

Drag and drop the code from the bottom onto the box where the code is missing to construct a contact tracking application that dynamically returns all the Bluetooth clients on a given Meraki network. Not all options are used.

A developer is building an application to access a website. When running the application, an HTTP 403 error
code has been received. How should the application be modified to handle this code?
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
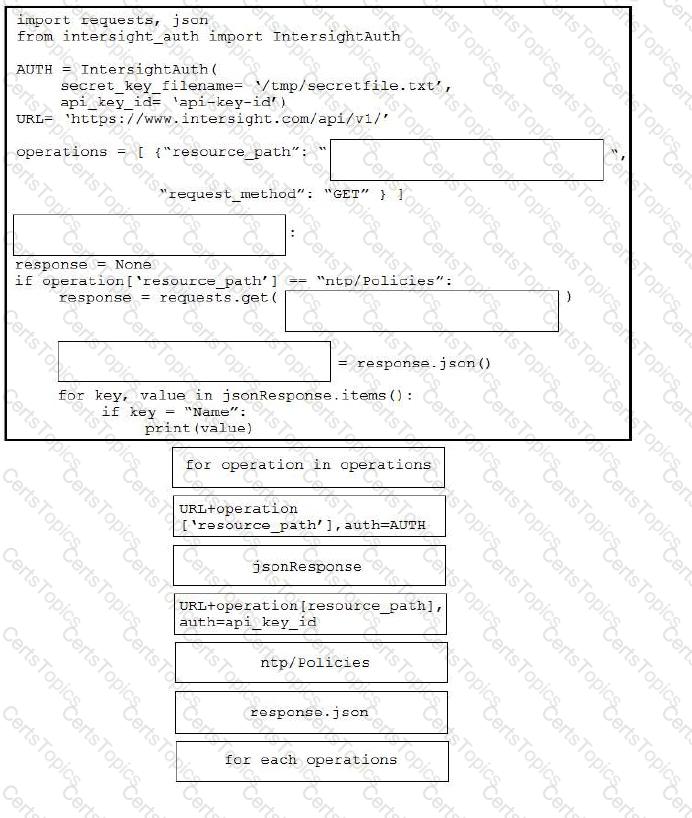
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to execute a REST API call to query all the NTP policy names and print the name of each policy. Not all options are used.
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API Not all options are used.

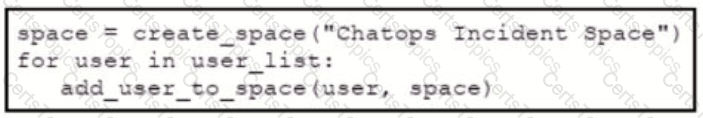
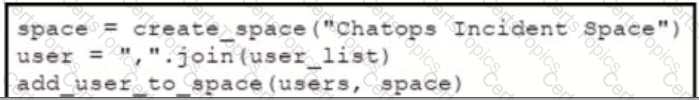
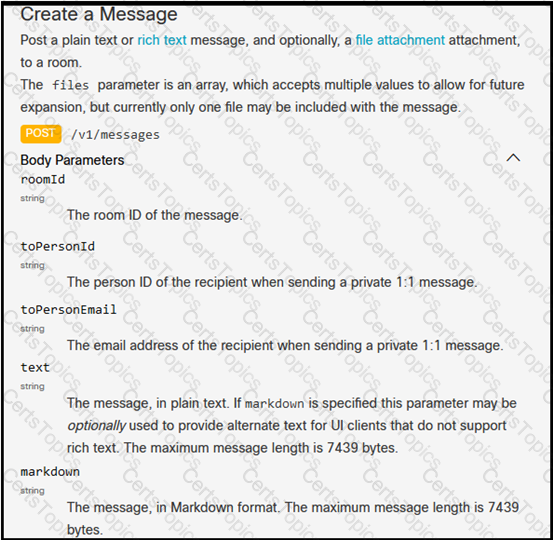
Refer to the exhibit. Which snippet creates a Webex Teams space and adds the users in the variable user list to that space?
A)
B)
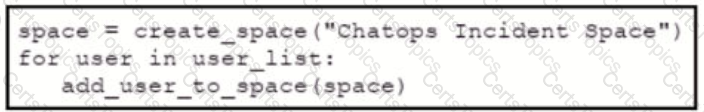
C)
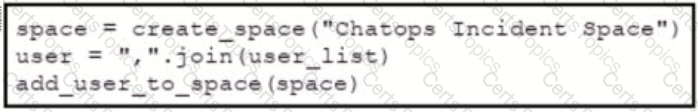
D)
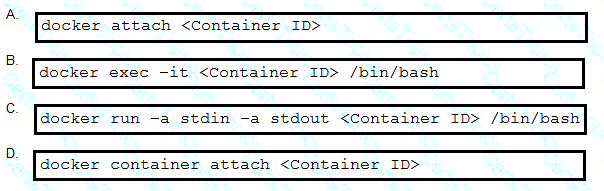
A local Docker container with a Container ID of 391441516e7a is running a Python application. Which
command is used to connect to a bash shell in the running container?
Refer to the exhibit.
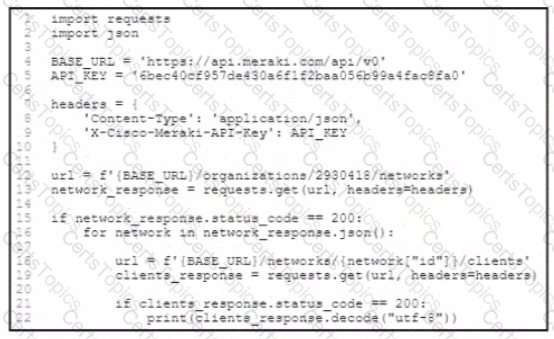
One part of an application routinely uses the Cisco Meraki API to collate data about all clients Other parts of the application also use the Meraki API, but a single API key is used within the application The organization has approximately 4.000 clients across 30 networks Some of the application users report poor performance and missing data. Which two changes improve the performance of the application? (Choose two.)
Refer to the exhibit.
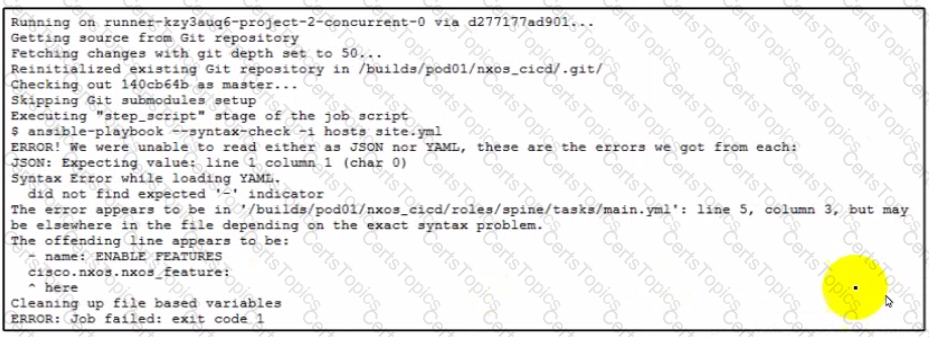
A network engineer developed an Ansible playbook and committed it to GitLab. A GitLab CI pipeline is started but immediately fails. What is the issue?
Refer to the exhibit.

A developer must configure an SSL certificate for an nginx web server Which code must be added on the script to accomplish this configuration?
A)

B)

C)

D)

{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
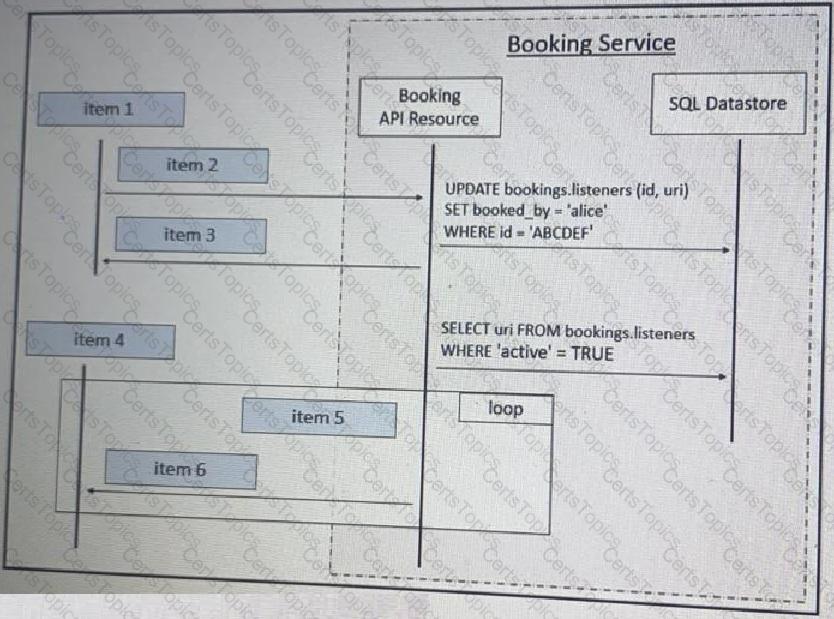
Refer to the exhibit above and click on the tab in the top left corner to view a diagram that describes the typical flow of requests involved when a webhook is created for a booking service. Drag and drop the requests from the left onto the item numbers on the right that match the missing sections in the sequence diagram to design the complete flow of requests involved as a booking is updated from a web application.

Which two situations are flagged by software tools designed for dependency checking in continuous integration environments, such as OWASP? (Choose two.)

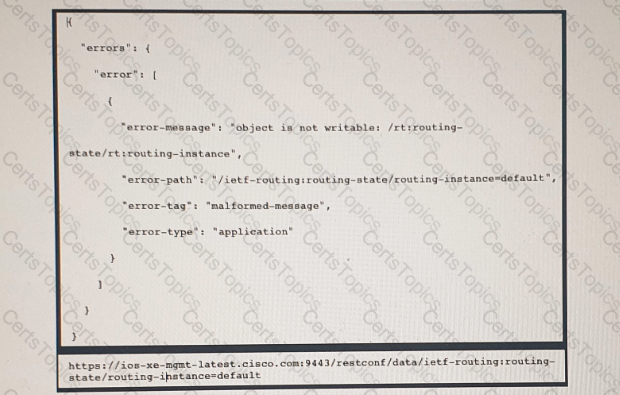
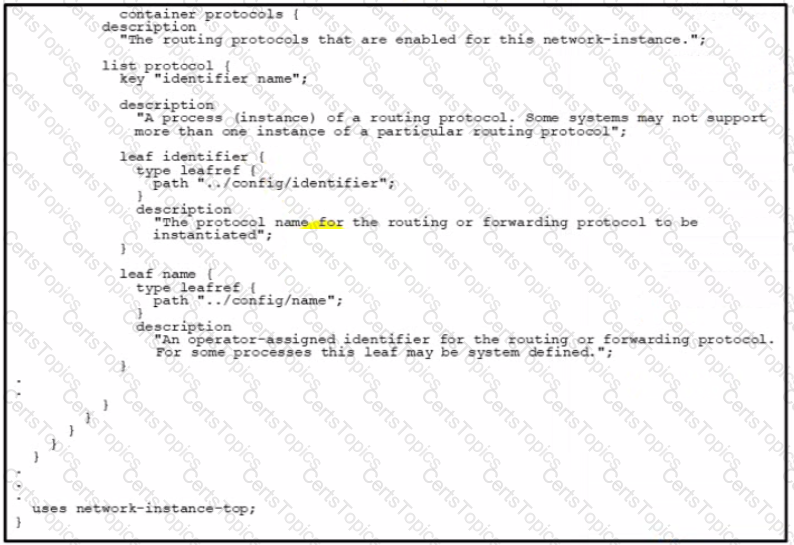
Refer to the exhibit above and click on the IETF Routing tab in the top left corner to help with this question. A developer is trying to update the routing instance by adding a new route to the routes list using the URL in the exhibit. What action must be taken to fix the error being received?
DRAG DROP

Refer to the exhibit. A system administrator has installed a Linux-based alarm system in their home that can execute a Bash shell script when an intruder is detected. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a chat-ops script that will notify of alarms via the Webex Teams REST API. Not all code snippets are used.
Which command is used 10 enable application hosting on a Cisco IOS XE device?
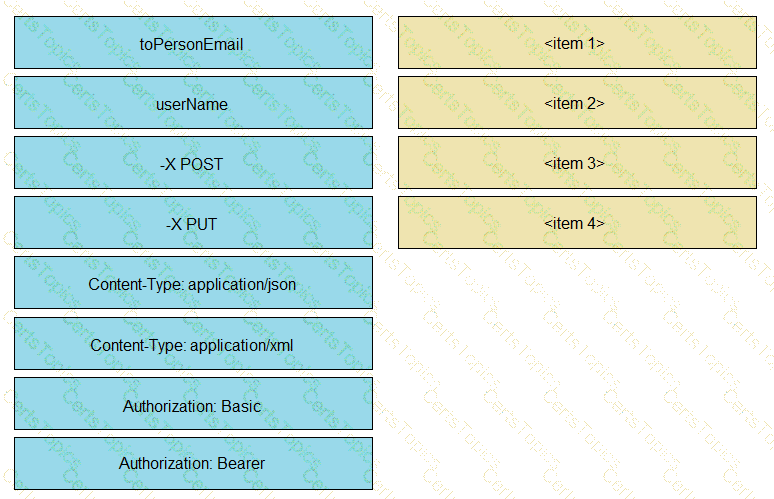
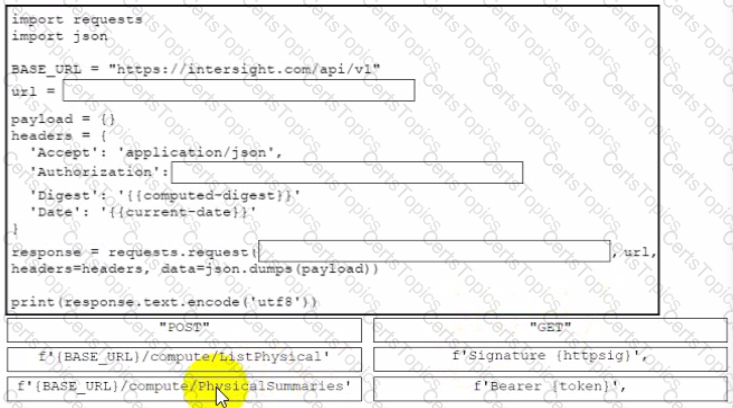
Drag and drop the code from the bottom onto the box where the code is missing to retrieve a summary of physical compute resources. The collected information about the compute resources will be presented in a dashboard to be developed for device monitoring purposes. Not all snippets are used.
An application has these characteristics
• provide one service or function
• distributed database
• API gateway
• central repository for code
• configuration database
• uses session management
Which two design approaches contribute to the scalability of the application? (Choose two.)
Drag and drop the steps from the left into the order on the right to create the workflow to retrieve the gateway information from a set of Cisco IOS devices. Not all options are used.
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to provision a new UCS server. Not all options are used.

Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
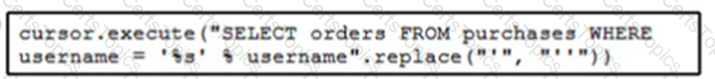
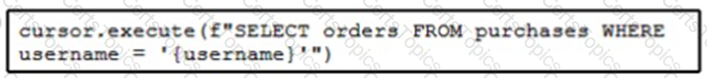
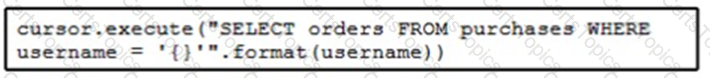
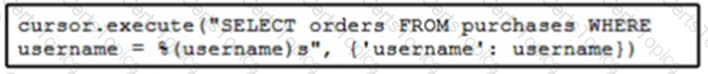
Refer to the exhibit. The code fetches the latest order from the purchases table for a specific user. An engineer needs to pass query parameters to the execute function to prevent an SQL injection attack. Which code snippet must be placed in the blank in the code to meet this requirement?
A)
B)
C)
D)
What is a characteristic of event-driven architecture?
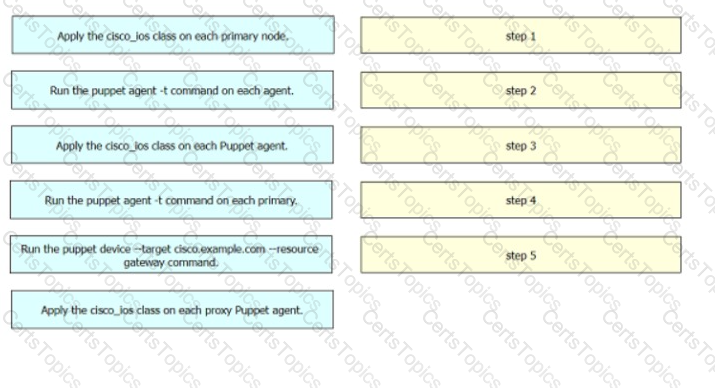
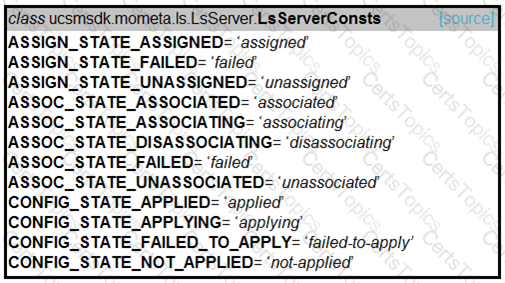
Which Puppet manifest needs to be used to configure an interface GigabitEthernet 0/1 on a Cisco IOS switch?
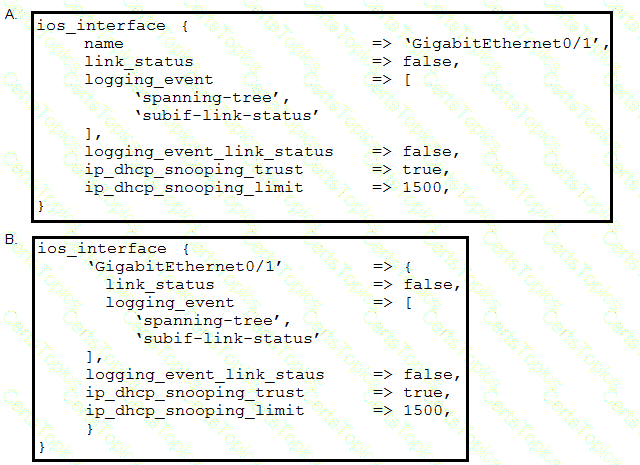
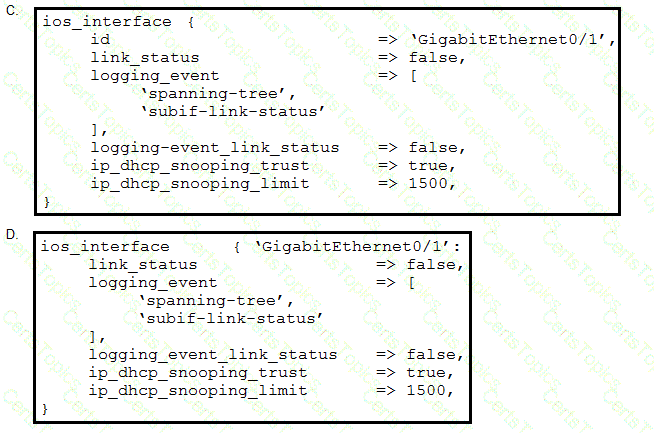
Refer to the exhibit.
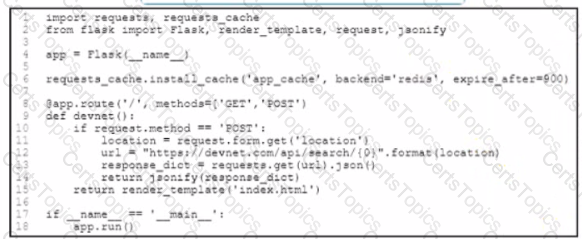
An application has been developed to serve the users in an enterprise After HTTP cache controls are implemented m the application users report that they receive state data when they refresh the page Without removing HTTP cache controls, which change ensures that the users get current data when refreshing the page'