An engineer has created a bash script to automate a complicated process. During script execution, this error occurs: permission denied. Which command must be added to execute this script?
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization’s service area. What are the next steps the engineer must take?
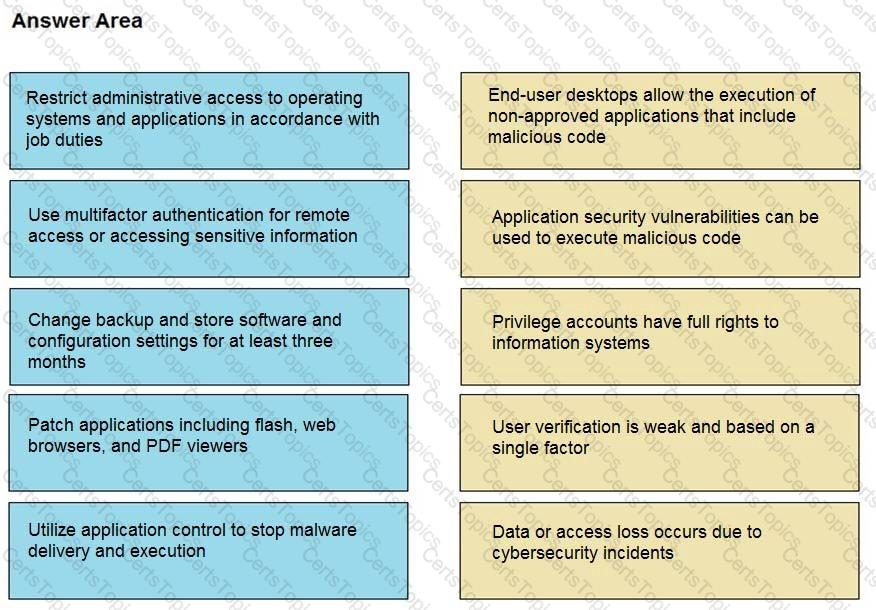
Drag and drop the mitigation steps from the left onto the vulnerabilities they mitigate on the right.
An engineer is investigating several cases of increased incoming spam emails and suspicious emails from the HR and service departments. While checking the event sources, the website monitoring tool showed several web scraping alerts overnight. Which type of compromise is indicated?
Refer to the exhibit.
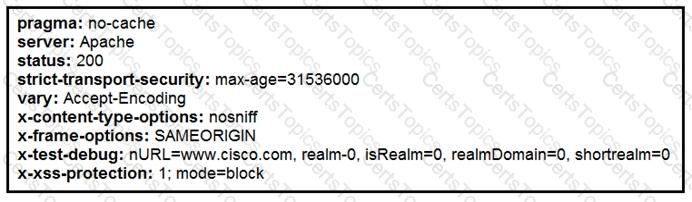
Where does it signify that a page will be stopped from loading when a scripting attack is detected?