Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
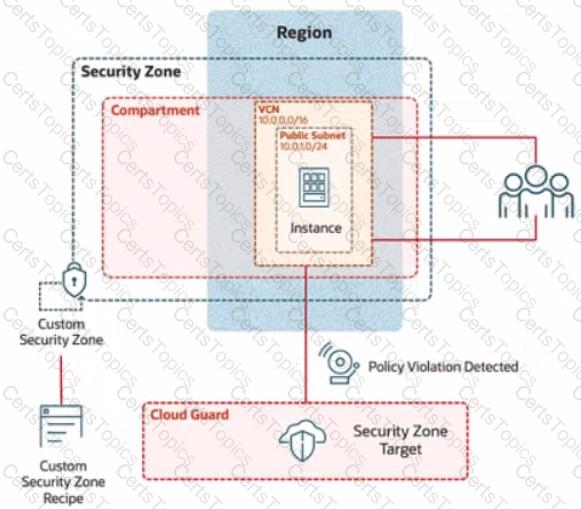
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task3: Create and configure a Virtual Cloud Network and Private Subnet
Createand configure virtual cloud Network (VCN) named IAD SP-PBT-VCN-01, with an internet Gateway and configure appropriate route rules to allow external connectivity.
Enter the OCID of the created VCN in the text box below.
"Your company is building a highly available and secure web application on OCI. Because of increasing malicious web-based attacks, the security team has mandated that web servers should not be exposed directly to the Internet.
How should you architect the solution while ensuring fault tolerance and security?
You're managing an Oracle Cloud Infrastructure (OCI) environment where a public website hosts downloadable assets stored in Object Storage buckets. These buckets need to be publicly accessible for website visitors, but Cloud Guard keeps flagging them as security risks.
How can Cloud Guard be configured to ignore problems specific to public buckets while still ensuring security checks are applied to other resources that require them?
You are a security architect at your organization and have noticed an increase in cyberattacks on your applications, including Cross-Site Scripting (XSS) and SQL Injection. To mitigate these threats, you decide to use OCI Web Application Firewall (WAF).
Which type of OCI WAF rule should you configure to protect against these attacks?