Refer to the exhibit, which contains partial output from an IKE real-time debug.
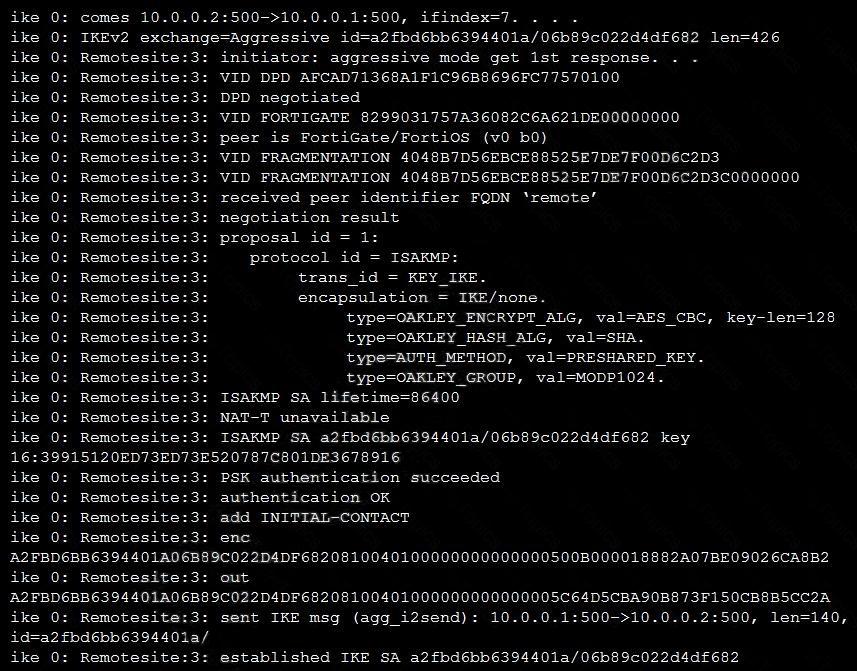
Which two statements about this debug output are correct? (Choose two.)
View the exhibit, which contains the output of a BGP debug command, and then answer the question below.
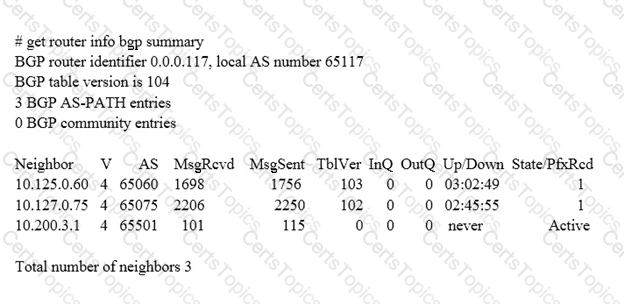
Which of the following statements about the exhibit are true? (Choose two.)
View the following FortiGate configuration.
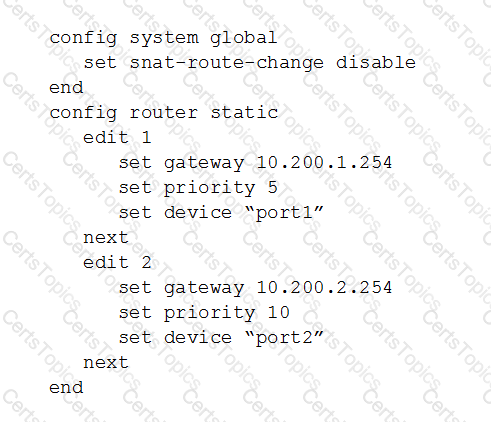
All traffic to the Internet currently egresses from port1. The exhibit shows partial session information for Internet traffic from a user on the internal network:
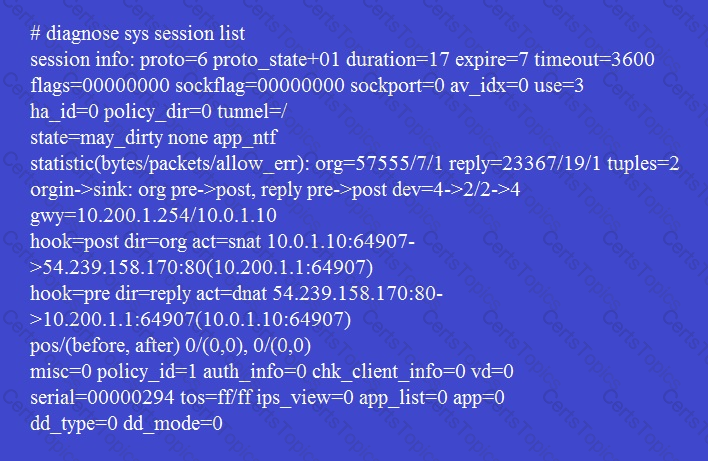
If the priority on route ID 1 were changed from 5 to 20, what would happen to traffic matching that user’s session?
What is the purpose of an internal segmentation firewall (ISFW)?