A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
Which statement describes a host-based intrusion prevention system (HIPS)?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
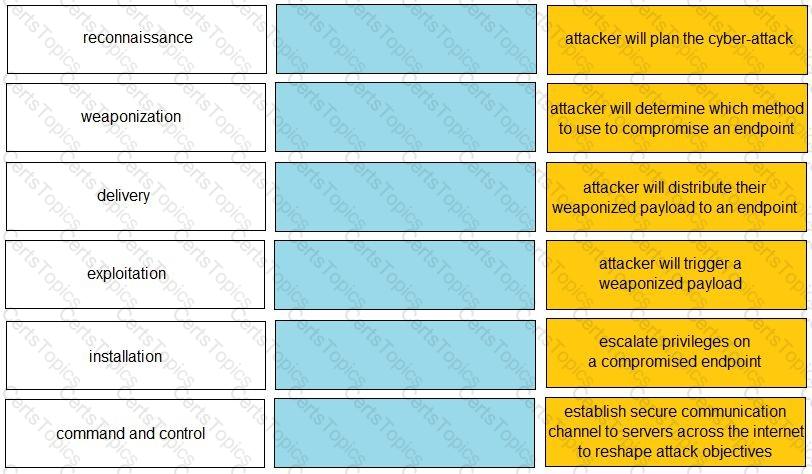
Given the graphic, match each stage of the cyber-attack lifecycle to its description.