Which of the Cloud-Delivered Security Services (CDSS) will detect zero-day malware by using inline cloud machine learning (ML) and sandboxing?
Which aspect of a SaaS application requires compliance with local organizational security policies?
Which feature of the VM-Series firewalls allows them to fully integrate into the DevOps workflows and CI/CD pipelines without slowing the pace of business?
Which of the following is a CI/CD platform?
A high-profile company executive receives an urgent email containing a malicious link. The sender appears to be from the IT department of the company, and the email requests an update of the executive's login credentials for a system update.
Which type of phishing attack does this represent?
Which statement describes a host-based intrusion prevention system (HIPS)?
Which endpoint product from Palo Alto Networks can help with SOC visibility?
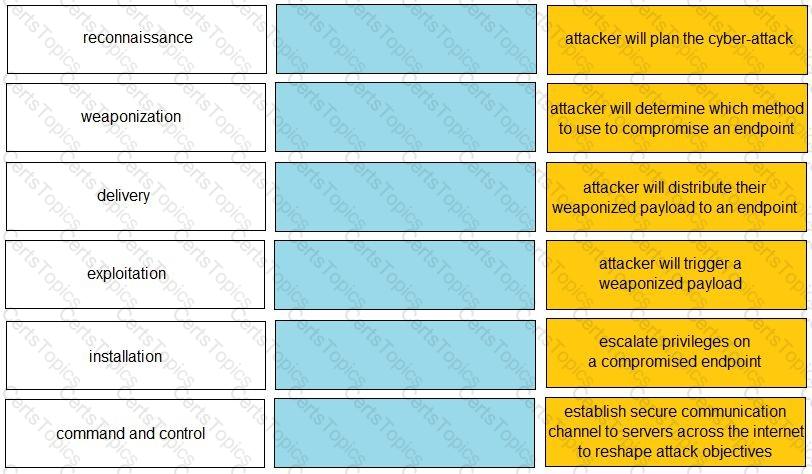
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
Which of the following is an AWS serverless service?
Which tool's analysis data gives security operations teams insight into their environment's risks from exposed services?
A firewall administrator needs to efficiently deploy corporate account configurations and VPN settings to targeted mobile devices within the network.
Which technology meets this requirement?
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
What protocol requires all routers in the same domain to maintain a map of the network?
Which NGFW feature is used to provide continuous identification, categorization, and control of known and previously unknown SaaS applications?
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
Which feature is part of an intrusion prevention system (IPS)?
What is an operation of an Attack Surface Management (ASM) platform?
What is a key advantage and key risk in using a public cloud environment?
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account.
Which type of attack is this?
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
A user is provided access over the internet to an application running on a cloud infrastructure. The servers, databases, and code of that application are hosted and maintained by the vendor.
Which NIST cloud service model is this?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which network firewall primarily filters traffic based on source and destination IP address?
Which endpoint protection security option can prevent malware from executing software?
What are three benefits of the cloud native security platform? (Choose three.)
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
What are two examples of an attacker using social engineering? (Choose two.)
Which item accurately describes a security weakness that is caused by implementing a “ports first” data security solution in a traditional data center?
Which technique uses file sharing or an instant messenger client such as Meebo running over Hypertext Transfer Protocol (HTTP)?
Which component of the AAA framework verifies user identities so they may access the network?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
Which technology grants enhanced visibility and threat prevention locally on a device?
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
How does Cortex XSOAR Threat Intelligence Management (TIM) provide relevant threat data to analysts?
How can local systems eliminate vulnerabilities?
What is an advantage of virtual firewalls over physical firewalls for internal segmentation when placed in a data center?
Which technology helps Security Operations Center (SOC) teams identify heap spray attacks on company-owned laptops?
Which tool automates remediation of a confirmed cybersecurity breach?
The seventy of an attack needs to be escalated.
What needs to be in place in order for the security operations team to properly inform various units within the enterprise of the issue?
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
Which type of attack involves sending data packets disguised as queries to a remote server, which then sends the data back to the attacker?
Which key component is used to configure a static route?
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads.
What deployment options do you have available? (Choose two.)
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
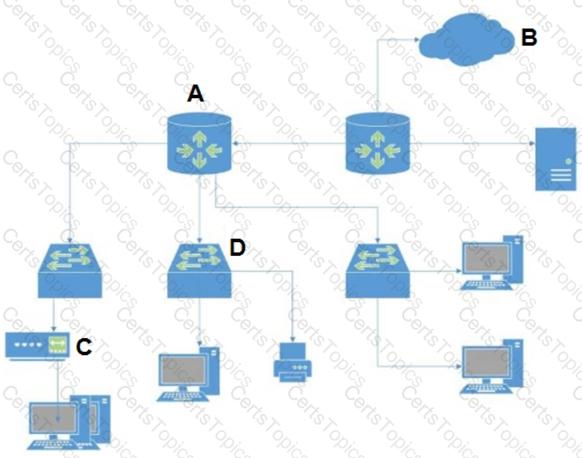
In the attached network diagram, which device is the switch?
Which type of portable architecture can package software with dependencies in an isolated unit?
Which option is an example of a North-South traffic flow?
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
Which next-generation firewall (NGFW) deployment option provides full application visibility into Kubernetes environments?
What does SOAR technology use to automate and coordinate workflows?
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
What type of attack redirects the traffic of a legitimate website to a fake website?
Which technique changes protocols at random during a session?
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
What is the purpose of host-based architectures?
Which statement is true about advanced persistent threats?
Which two network resources does a directory service database contain? (Choose two.)
Which type of Wi-Fi attack depends on the victim initiating the connection?
Which method is used to exploit vulnerabilities, services, and applications?
Which characteristic of serverless computing enables developers to quickly deploy application code?
What does Palo Alto Networks Cortex XDR do first when an endpoint is asked to run an executable?
Which element of the security operations process is concerned with using external functions to help achieve goals?
Which term describes establishment of on-premises software on a cloud-based server?
Which type of attack obscures its presence while attempting to spread to multiple hosts in a network?