Fortinet Related Exams
FCP_FML_AD-7.4 Exam







Refer to the exhibit, which shows an inbound recipient policy.
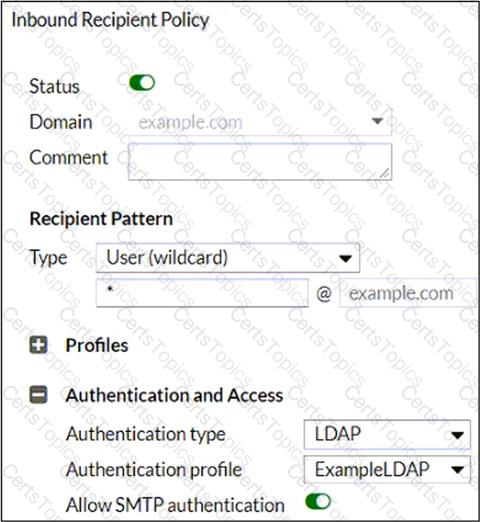
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibit, which shows the output of an email transmission using a telnet session.
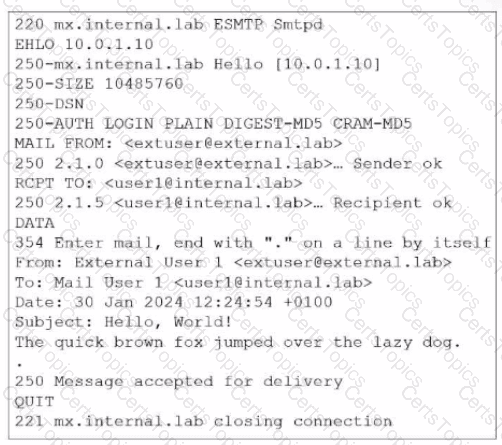
What are two correct observations about this SMTP session? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
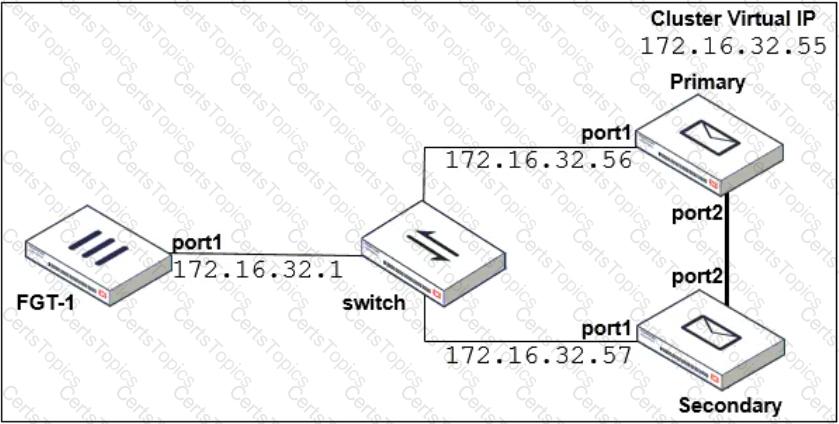
Which IP address must the DNS MX record for this organization resolve to?