An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas. Which FortiMail feature specific to server mode can be used to accomplish this?
Exhibit.
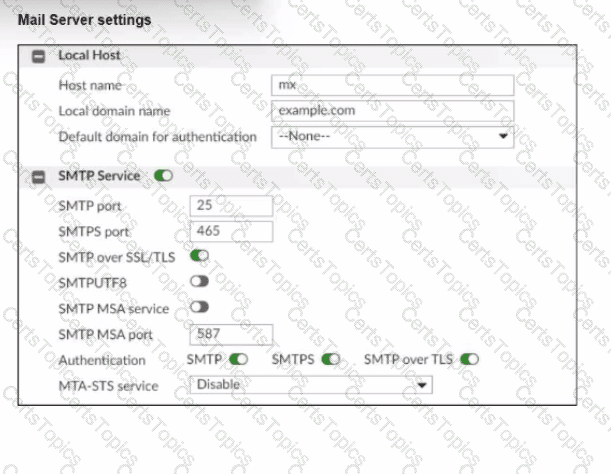
Refer to the exhibit, which shows the mail server settings of a FortiMail device. What are two ways this FortiMail device will handle connections? (Choose two.)
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs werenotgenerated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
Refer to the exhibit, which displays an encryption profile configuration.
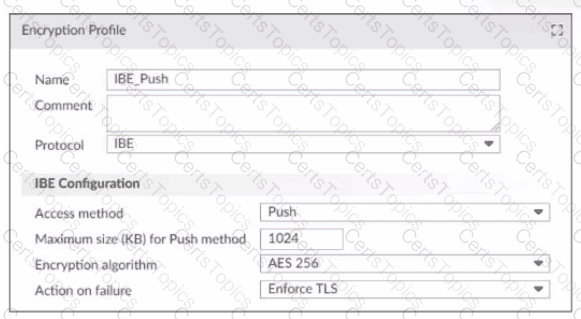
What happens if the attachment size of an IBE email exceeds 1024 KB?
Which SMTP command lists (he supported SMTP service extensions of the recipient MTA?
A FortiMail device is configured with the protected domain example. com.
It senders are not authenticated, which two envelope addresses will require an access receive rule? (Choose two.)
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
Refer to the exhibit, which shows the Authentication Reputation list on a FortiMail device running in gateway mode.
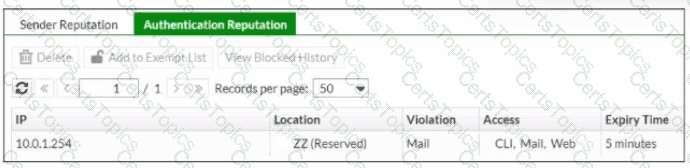
Why was the IP address blocked?
A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
Refer to the exhibit which displays a topology diagram.
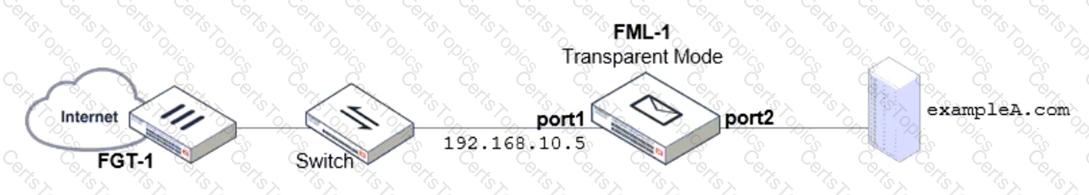
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
Refer to the exhibit, which shows an inbound recipient policy.
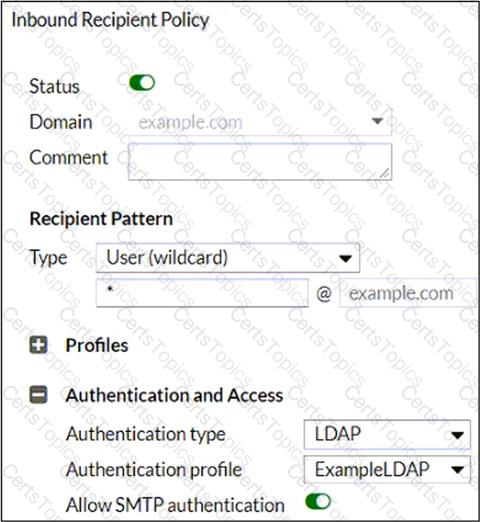
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibit, which shows the output of an email transmission using a telnet session.
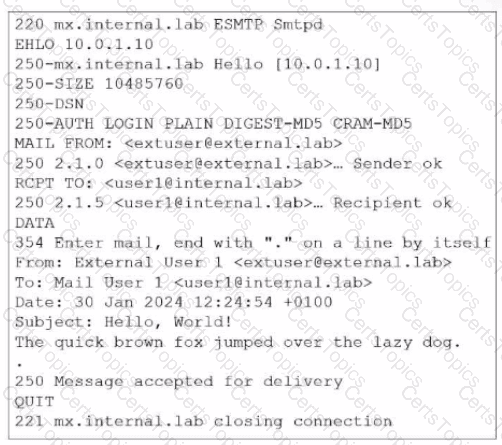
What are two correct observations about this SMTP session? (Choose two.)
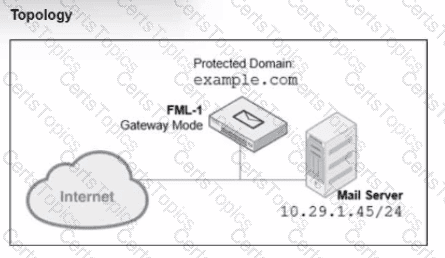
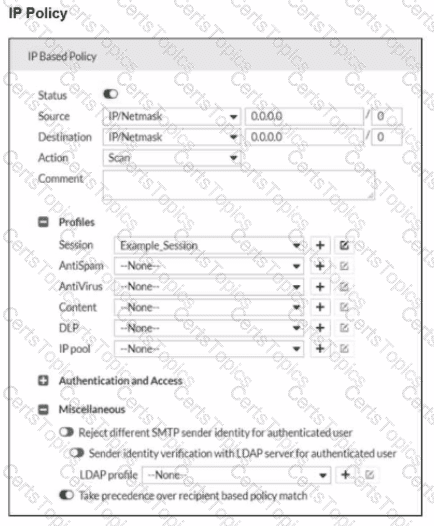
Refer to the exhibits, which show a topology diagram (Topology) and a configuration element (IP Policy).
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the mail server starts filling up with undeliverable email.
Which two changes must theadministrator make to fix this issue? (Choose two.)
Refer to the exhibit which shows a topology diagram of a FortiMail cluster deployment.
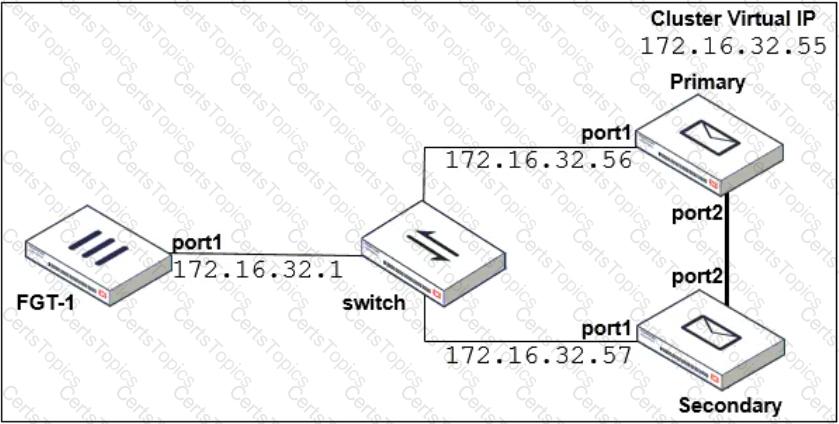
Which IP address must the DNS MX record for this organization resolve to?