During a recent internal purple team exercise, the following recommendation is given to the detection engineering team: Detect and prevent command line invocation of Python on Windows endpoints by non-technical business units. Which rule type should be implemented?
Analytics Behavioral Indicator of Compromise (ABIOC)
Behavioral Indicator of Compromise (BIOC)
Correlation
Indicator of Compromise (IOC)
The recommendation requires detecting and preventing the command line invocation of Python (e.g., python.exe or py.exe) on Windows endpoints, specifically for non-technical business units. This involves identifying a specific behavior (command line execution of Python) and enforcing a preventive action (e.g., blocking the process). In Cortex XDR,Behavioral Indicators of Compromise (BIOCs)are used to define and detect specific patterns of behavior on endpoints, such as command line activities, and can be paired with aRestriction profileto block the behavior.
Correct Answer Analysis (B):ABehavioral Indicator of Compromise (BIOC)rule should be implemented. The BIOC can be configured to detect the command line invocation of Python by defining conditions such as the process name (python.exe or py.exe) and the command line arguments. For example, a BIOC rule might look for process = python.exe with a command line pattern like cmd.exe /c python*. This BIOC can then be added to a Restriction profile to prevent the execution of Python by non-technical business units, which can be targeted by applying the profile to specific endpoint groups (e.g., those assigned to non-technical units).
Why not the other options?
A. Analytics Behavioral Indicator of Compromise (ABIOC): ABIOCs are analytics-driven rules generated by Cortex XDR’s machine learning and behavioralanalytics, not user-defined rules. They are not suitable for creating custom detection and prevention rules like the one needed here.
C. Correlation: Correlation rules are used to generate alerts by correlating events across multiple datasets (e.g., network and endpoint data), but they do not directly prevent behaviors like command line execution.
D. Indicator of Compromise (IOC): IOCs are used to detect specific artifacts (e.g., file hashes, IP addresses) associated with known threats, not to detect and prevent behavioral patterns like command line execution.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains BIOC rules: “Behavioral Indicators of Compromise (BIOCs) can detect specific endpoint behaviors, such as command line invocation of processes like Python, and prevent them when added to a Restriction profile” (paraphrased from the BIOC section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers detection engineering, stating that “BIOCs are used to detect and block specific behaviors, such as command line executions, on Windows endpoints” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing BIOC rule creation.
Multiple remote desktop users complain of in-house applications no longer working. The team uses macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images below, what is a reason for this behavior?
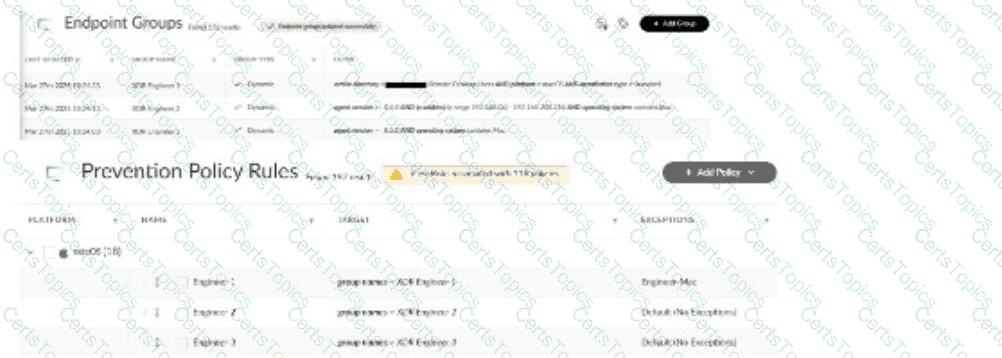
Endpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range
The Cloud Identity Engine is disconnected or removed
XDR agent version was downgraded from 8.7.0 to 8.4.0
Installation type changed from VDI to Kubernetes
The scenario involves macOS users with Cortex XDR agents (version 8.7.0) who can no longer run in-house applications that were previously allowed via disable prevention rules in the"Engineer-Mac" Exceptions Profile. This profile is applied to an endpoint group (e.g., "Mac-Engineers"). Theissue likely stems from a change in the endpoint group’s configuration or the endpoints’ attributes, affecting policy application.
Correct Answer Analysis (A):The reason for the behavior is that theendpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range. In Cortex XDR, endpoint groups can be defined using dynamic criteria, such as IP address ranges, to apply specific policies like the "Engineer-Mac" Exceptions Profile. If the group "Mac-Engineers" was defined to include endpoints in the 192.168.0.0 range, and the remote desktop users’ IP addresses changed to the 192.168.100.0 range (e.g., due to a network change or VPN reconfiguration), these endpoints would no longer belong to the "Mac-Engineers" group. As a result, the "Engineer-Mac" Exceptions Profile, which allowed the in-house applications, would no longer apply, causing the applications to be blocked by default prevention rules.
Why not the other options?
B. The Cloud Identity Engine is disconnected or removed: The Cloud Identity Engine provides user and group data for identity-based policies, but it is not directly related to Exceptions Profiles or application execution rules. Its disconnection would not affect the application of the "Engineer-Mac" profile.
C. XDR agent version was downgraded from 8.7.0 to 8.4.0: The question states the users are using version 8.7.0, and there’s no indication of a downgrade. Even if a downgrade occurred, it’s unlikely to affect the application of an Exceptions Profile unless specific features were removed, which is not indicated.
D. Installation type changed from VDI to Kubernetes: The installation type (e.g., VDI for virtual desktops or Kubernetes for containerized environments) is unrelated to macOS endpoints running remote desktop sessions. This change would not impact the application of the Exceptions Profile.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains endpoint group policies: “Dynamic endpoint groups based on IP address ranges apply policies like Exceptions Profiles; if an endpoint’s IP changes to a different range, it may no longer belong to the group, affecting policy enforcement” (paraphrased from the Endpoint Management section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers policy application, stating that “changes in IP address ranges can cause endpoints to fall out of a group, leading to unexpected policy behavior like blocking previously allowed applications” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration” as a key exam topic, encompassing endpoint group and policy management.
Log events from a previously deployed Windows XDR Collector agent are no longer being observed in the console after an OS upgrade. Which aspect of the log events is the probable cause of this behavior?
They are greater than 5MB
They are in Winlogbeat format
They are in Filebeat format
They are less than 1MB
TheXDR Collectoron a Windows endpoint collects logs (e.g., Windows Event Logs) and forwards them to the Cortex XDR console for analysis. An OS upgrade can impact the collector’s functionality, particularly if it affects log formats, sizes, or compatibility. If log events are no longer observed after the upgrade, the issue likely relates to a change in how logs are processed or transmitted. Cortex XDR imposes limits on log event sizes to ensure efficient ingestion and processing.
Correct Answer Analysis (A):The probable cause is thatthe log events are greater than 5MB. Cortex XDR has a size limit for individual log events, typically around 5MB, to prevent performance issues during ingestion. An OS upgrade may change the way logs are generated (e.g., increasing verbosity or adding metadata), causing events to exceed this limit. If log events are larger than 5MB, the XDR Collector will drop them, resulting in no logs being observed in the console.
Why not the other options?
B. They are in Winlogbeat format: Winlogbeat is a supported log shipper for collecting Windows Event Logs, and the XDR Collector is compatible with this format. The format itself is not the issue unless misconfigured, which is not indicated.
C. They are in Filebeat format: Filebeat is also supported by the XDR Collector for file-based logs. The format is not the likely cause unless the OS upgrade changed the log source, which is not specified.
D. They are less than 1MB: There is no minimum size limit for log events in Cortex XDR, so being less than 1MB would not cause logs to stop appearing.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains log ingestion limits: “Individual log events larger than 5MB are dropped by the XDR Collector to prevent ingestion issues, which may occur after changes like an OS upgrade” (paraphrased from the XDR Collector Troubleshooting section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers log collection issues, stating that “log events exceeding 5MB are not ingested, a common issue after OS upgrades thatincrease log size” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “maintenance and troubleshooting” as a key exam topic, encompassing log ingestion issues.
A new parsing rule is created, and during testing and verification, all the logs for which field data is to be parsed out are missing. All the other logs from this data source appear as expected. What may be the cause of this behavior?
The Broker VM is offline
The parsing rule corrupted the database
The filter stage is dropping the logs
The XDR Collector is dropping the logs
In Cortex XDR,parsing rulesare used to extract and normalize fields from raw log data during ingestion, ensuring that the data is structured for analysis and correlation. The parsing process includes stages such as filtering, parsing, and mapping. If logs for which field data is to be parsed out are missing, while other logs from the same data source are ingested as expected, the issue likely lies within the parsing rule itself, specifically in the filtering stage that determines which logs are processed.
Correct Answer Analysis (C):The filter stage is dropping the logsis the most likely cause. Parsing rules often include afilter stagethat determines which logs are processed based on specific conditions (e.g., log content, source, or type). If the filter stage of the new parsing rule is misconfigured (e.g., using an incorrect condition like log_type != expected_type or a regex that doesn’t match the logs), it may drop the logs intended for parsing, causing them to be excluded from the ingestion pipeline. Since other logs from the same data source are ingested correctly, the issue is specific to the parsing rule’s filter, not a broader ingestion problem.
Why not the other options?
A. The Broker VM is offline: If the Broker VM were offline, it would affect all log ingestion from the data source, not just the specific logs targeted by the parsing rule. The question states that other logs from the same data source are ingested as expected, so the Broker VM is likely operational.
B. The parsing rule corrupted the database: Parsing rules operate on incoming logs during ingestion and do not directly interact with or corrupt the Cortex XDR database. This is an unlikely cause, and database corruption would likely cause broader issues, not just missing specific logs.
D. The XDR Collector is dropping the logs: The XDR Collector forwards logs to Cortex XDR, and if it were dropping logs, it would likely affect all logs from the data source, not just those targeted by the parsing rule. Since other logs are ingested correctly, the issue is downstream in the parsing rule, not at the collector level.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains parsing rule behavior: “The filter stage in a parsing rule determines which logs are processed; misconfigured filters can drop logs, causing them to be excluded from ingestion” (paraphrased from the Data Ingestion section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers parsing rule troubleshooting, stating that “if specific logs are missing during parsing, check the filter stage for conditions that may be dropping the logs” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing parsing rule configuration and troubleshooting.
An administrator wants to employ reusable rules within custom parsing rules to apply consistent log field extraction across multiple data sources. Which section of the parsing rule should the administrator use to define those reusable rules in Cortex XDR?
RULE
INGEST
FILTER
CONST
In Cortex XDR, parsing rules are used to extract and normalize fields from log data ingested from various sources to ensure consistent analysis and correlation. To create reusable rules for consistent log field extraction across multiple data sources, administrators use theCONSTsection within the parsing rule configuration. TheCONSTsection allows the definition of reusable constants or rules that can be applied across different parsing rules, ensuring uniformity in how fields are extracted and processed.
TheCONSTsection is specifically designed to hold constant values or reusable expressions that can be referenced in other parts of the parsing rule, such as theRULEorINGESTsections. This is particularly useful when multiple data sources require similar field extraction logic, as it reduces redundancy and ensures consistency. For example, a constant regex pattern for extracting IP addresses can be defined in theCONSTsection and reused across multiple parsing rules.
Why not the other options?
RULE: TheRULEsection defines the specific logic for parsing and extracting fields from a log entry but is not inherently reusable across multiple rules unless referenced via constants defined inCONST.
INGEST: TheINGESTsection specifies how raw log data is ingested and preprocessed, not where reusable rules are defined.
FILTER: TheFILTERsection is used to include or exclude log entries based on conditions, not for defining reusable extraction rules.
Exact Extract or Reference:
While the exact wording of theCONSTsection’s purpose is not directly quoted in public-facing documentation (as some details are in proprietary training materials like EDU-260 or the Cortex XDR Admin Guide), theCortex XDR Documentation Portal(docs-cortex.paloaltonetworks.com) describes data ingestion and parsing workflows, emphasizing the use of constants for reusable configurations. TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers data onboarding and parsing, noting that “constants defined in the CONST section allow reusable parsing logic for consistent field extraction across sources” (paraphrased from course objectives). Additionally, thePalo Alto Networks Certified XDR Engineer datasheetlists “data source onboarding and integration configuration” as a key skill, which includes mastering parsing rules and their components likeCONST.
After deploying Cortex XDR agents to a large group of endpoints, some of the endpoints have a partially protected status. In which two places can insights into what is contributing to this status be located? (Choose two.)
Management Audit Logs
XQL query of the endpoints dataset
All Endpoints page
Asset Inventory
In Cortex XDR, apartially protected statusfor an endpoint indicates that some agent components or protection modules (e.g., malware protection, exploit prevention) are not fully operational, possibly due to compatibility issues, missing prerequisites, or configuration errors. To troubleshoot this status, engineers need to identify the specific components or issues affecting the endpoint, which can be done by examining detailed endpoint data and status information.
Correct Answer Analysis (B, C):
B. XQL query of the endpoints dataset: AnXQL (XDR Query Language)query against the endpoints dataset (e.g., dataset = endpoints | filter endpoint_status = "PARTIALLY_PROTECTED" | fields endpoint_name, protection_status_details) provides detailed insights into the reasons for the partially protected status. The endpoints dataset includes fields like protection_status_details, which specify which modules are not functioning and why.
C. All Endpoints page: TheAll Endpoints pagein the Cortex XDR console displays a list of all endpoints with their statuses, including those that are partially protected. Clicking into an endpoint’s details reveals specific information about the protection status, such as which modules are disabled or encountering issues, helping identify the cause of the status.
Why not the other options?
A. Management Audit Logs: Management Audit Logs track administrative actions (e.g., policy changes, agent installations), but they do not provide detailed insights into the endpoint’s protection status or the reasons for partial protection.
D. Asset Inventory: Asset Inventory provides an overview of assets (e.g., hardware, software) but does not specifically detail the protection status of Cortex XDR agents or the reasons for partial protection.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains troubleshooting partially protected endpoints:“Use the All Endpoints page to view detailed protection status, and run an XQL query against the endpoints dataset to identify specific issues contributing to a partially protected status” (paraphrased from the Endpoint Management section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers endpoint troubleshooting, stating that “the All Endpoints page and XQL queries of the endpoints dataset provide insights into partial protection issues” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “maintenance and troubleshooting” as a key exam topic, encompassing endpoint status investigation.
What will enable a custom prevention rule to block specific behavior?
A correlation rule added to an Agent Blocking profile
A custom behavioral indicator of compromise (BIOC) added to an Exploit profile
A custom behavioral indicator of compromise (BIOC) added to a Restriction profile
A correlation rule added to a Malware profile
In Cortex XDR,custom prevention rulesare used to block specific behaviors or activities on endpoints by leveragingBehavioral Indicators of Compromise (BIOCs). BIOCs define patterns of behavior (e.g., specific process executions, file modifications, or network activities) that, when detected, can trigger preventive actions, such as blocking a process or isolating an endpoint. These BIOCs are typically associated with aRestriction profile, which enforces blocking actions for matched behaviors.
Correct Answer Analysis (C):Acustom behavioral indicator of compromise (BIOC)added to aRestriction profileenables a custom prevention rule to block specific behavior. The BIOC defines the behavior to detect (e.g., a process accessing a sensitive file), and the Restriction profile specifies the preventive action (e.g., block the process). This configuration ensures that the identified behavior is blocked on endpoints where the profile is applied.
Why not the other options?
A. A correlation rule added to an Agent Blocking profile: Correlation rules are used to generate alerts by correlating events across datasets, not to block behaviors directly. There is no “Agent Blocking profile” in Cortex XDR; this is a misnomer.
B. A custom behavioral indicator of compromise (BIOC) added to an Exploit profile: Exploit profiles are used to detect and prevent exploit-based attacks (e.g., memory corruption), not general behavioral patterns defined by BIOCs. BIOCs are associated with Restriction profiles for blocking behaviors.
D. A correlation rule added to a Malware profile: Correlation rules do not directly block behaviors; they generate alerts. Malware profiles focus on file-based threats (e.g., executables analyzed by WildFire), not behavioral blocking via BIOCs.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains BIOC and Restriction profiles: “Custom BIOCs can be added to Restriction profiles to block specific behaviors on endpoints, enabling tailored prevention rules” (paraphrased from the BIOC and Restriction Profile sections). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers prevention rules, stating that “BIOCs in Restriction profiles enable blocking of specific endpoint behaviors” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing BIOC and prevention rule configuration.
When isolating Cortex XDR agent components to troubleshoot for compatibility, which command is used to turn off a component on a Windows machine?
"C:\Program Files\Palo Alto Networks\Traps\xdr.exe" stop
"C:\Program Files\Palo Alto Networks\Traps\cytool.exe" runtime stop
"C:\Program Files\Palo Alto Networks\Traps\xdr.exe" -s stop
"C:\Program Files\Palo Alto Networks\Traps\cytool.exe" occp
Cortex XDR agents on Windows include multiple components (e.g., for exploit protection, malware scanning, or behavioral analysis) that can be individually enabled or disabled for troubleshooting purposes, such as isolating compatibility issues. Thecytool.exeutility, located in the Cortex XDR installation directory (typically C:\Program Files\Palo Alto Networks\Traps\), is used to manage agent components and settings. The runtime stop command specifically disables a component without uninstalling the agent.
Correct Answer Analysis (B):The command"C:\Program Files\Palo Alto Networks\Traps\cytool.exe" runtime stopis used to turn off a specific Cortex XDR agent component on a Windows machine. For example, cytool.exe runtime stop protection would disable the protection component, allowing troubleshooting for compatibility issues while keeping other components active.
Why not the other options?
A. "C:\Program Files\Palo Alto Networks\Traps\xdr.exe" stop: The xdr.exe binary is not used for managing components; it is part of the agent’s corefunctionality. The correct utility is cytool.exe.
C. "C:\Program Files\Palo Alto Networks\Traps\xdr.exe" -s stop: Similarly, xdr.exe is not the correct tool, and -s stop is not a valid command syntax for component management.
D. "C:\Program Files\Palo Alto Networks\Traps\cytool.exe" occp: The occp command is not a valid cytool.exe option. The correct command for stopping a component is runtime stop.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains component management: “To disable a Cortex XDR agent component on Windows, use the command cytool.exe runtime stop
The most recent Cortex XDR agents are being installed at a newly acquired company. A list with endpoint types (i.e., OS, hardware, software) is provided to the engineer. What should be cross-referenced for the Linux systems listed regarding the OS types and OS versions supported?
Content Compatibility Matrix
Kernel Module Version Support
End-of-Life Summary
Agent Installer Certificate
When installing Cortex XDR agents on Linux systems, ensuring compatibility with the operating system (OS) type and version is critical, especially for the most recent agent versions. Linux systems require specific kernel module support because the Cortex XDR agent relies on kernel modules for core functionality, such as process monitoring, file system protection, and network filtering. TheKernel Module Version Supportdocumentation provides detailed information on which Linux distributions (e.g., Ubuntu, CentOS, RHEL) and kernel versions are supported by the Cortex XDR agent, ensuring the agent can operate effectively on the target systems.
Correct Answer Analysis (B):TheKernel Module Version Supportshould be cross-referenced for Linux systems to verify that the OS types (e.g., Ubuntu, CentOS) and specific kernel versions listed are supported by the Cortex XDR agent. This ensures that the agent’s kernel modules, which are essential for protection features, are compatible with the Linux endpoints at the newly acquired company.
Why not the other options?
A. Content Compatibility Matrix: A Content Compatibility Matrix typically details compatibility between content updates (e.g., Behavioral Threat Protection rules) and agent versions, not OS or kernel compatibility for Linux systems.
C. End-of-Life Summary: The End-of-Life Summary provides information on agent versions or OS versions that are no longer supported by Palo Alto Networks, but it is not the primary resource for checking current OS and kernel compatibility.
D. Agent Installer Certificate: The Agent Installer Certificate relates to the cryptographic verification of the agent installer package, not to OS or kernel compatibility.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Linux agent requirements: “For Linux systems, cross-reference the Kernel Module Version Support to ensure compatibility with supported OS types and kernel versions” (paraphrased from the Linux Agent Deployment section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers Linux agent installation, stating that “Kernel Module Version Support lists compatible Linux distributions and kernel versions for Cortex XDR agents” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “planning and installation” as a key exam topic, encompassing Linux agent compatibility checks.
An XDR engineer is creating a correlation rule to monitor login activity on specific systems. When the activity is identified, an alert is created. The alerts are being generated properly but are missing the username when viewed. How can the username information be included in the alerts?
Select “Initial Access” in the MITRE ATT&CK mapping to include the username
Update the query in the correlation rule to include the username field
Add a mapping for the username field in the alert fields mapping
Add a drill-down query to the alert which pulls the username field
In Cortex XDR,correlation rulesare used to detect specific patterns or behaviors (e.g., login activity) by analyzing ingested data and generating alerts when conditions are met. For an alert to include specific fields likeusername, the field must be explicitly mapped in thealert fields mappingconfiguration of the correlation rule. This mapping determines which fields from theunderlying dataset are included in the generated alert’s details.
In this scenario, the correlation rule is correctly generating alerts for login activity, but theusernamefield is missing. This indicates that the correlation rule’s query may be identifying the relevant events, but theusernamefield is not included in the alert’s output fields. To resolve this, the engineer must update thealert fields mappingin the correlation rule to explicitly include theusernamefield, ensuring it appears in the alert details when viewed.
Correct Answer Analysis (C):Adding a mapping for theusernamefield in thealert fields mappingensures that the field is extracted from the dataset and included in the alert’s metadata. This is done in the correlation rule configuration, where administrators can specify which fields to include in the alert output.
Why not the other options?
A. Select “Initial Access” in the MITRE ATT&CK mapping to include the username: Mapping to a MITRE ATT&CK technique like “Initial Access” defines the type of attack or behavior, not specific fields likeusername. This does not address the missing field issue.
B. Update the query in the correlation rule to include the username field: While the correlation rule’s query must reference theusernamefield to detect relevant events, including it in the query alone does not ensure it appears in the alert’s output. Thealert fields mappingis still required.
D. Add a drill-down query to the alert which pulls the username field: Drill-down queries are used for additional investigation after an alert is generated, not for including fields in the alert itself. This does not solve the issue of missingusernamein the alert details.
Exact Extract or Reference:
TheCortex XDR Documentation Portaldescribes correlation rule configuration: “To include specific fields in generated alerts, configure the alert fields mapping in the correlation rule to map dataset fields, such as username, to the alert output” (paraphrased from the Correlation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers detection engineering, stating that “alert fields mapping determines which data fields are included in alerts generated by correlation rules” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing correlation rule configuration.
An engineer wants to automate the handling of alerts in Cortex XDR and defines several automation rules with different actions to be triggered based on specific alert conditions. Some alerts do not trigger the automation rules as expected. Which statement explains why the automation rules might not apply to certain alerts?
They are executed in sequential order, so alerts may not trigger the correct actions if the rules are not configured properly
They only apply to new alerts grouped into incidents by the system and only alerts that generateincidents trigger automation actions
They can only be triggered by alerts with high severity; alerts with low or informational severity will not trigger the automation rules
They can be applied to any alert, but they only work if the alert is manually grouped into an incident by the analyst
In Cortex XDR,automation rules(also known as response actions or playbooks) are used to automate alert handling based on specific conditions, such as alert type, severity, or source. These rules are executed in a defined order, and the first rule that matches an alert’s conditions triggers its associated actions. If automation rules are not triggering as expected, the issue often lies in their configuration or execution order.
Correct Answer Analysis (A):Automation rules areexecuted in sequential order, and each alert is evaluated against the rules in the order they are defined. If the rules are not configured properly (e.g., overly broad conditions in an earlier rule or incorrect prioritization), an alert may match an earlier rule and trigger its actions instead of the intended rule, or it may not match any rule due to misconfigured conditions. This explains why some alerts do not trigger the expected automation rules.
Why not the other options?
B. They only apply to new alerts grouped into incidents by the system and only alerts that generate incidents trigger automation actions: Automation rules can apply to both standalone alerts and those grouped into incidents. They are not limited to incident-related alerts.
C. They can only be triggered by alerts with high severity; alerts with low or informational severity will not trigger the automation rules: Automation rules can be configured to trigger based on any severity level (high, medium, low, or informational), so this is not a restriction.
D. They can be applied to any alert, but they only work if the alert is manually grouped into an incident by the analyst: Automation rules do not require manual incident grouping; they can apply to any alert based on defined conditions, regardless of incident status.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains automation rules: “Automation rules are executed in sequential order, and the first rule matching an alert’s conditions triggers its actions. Misconfigured rules or incorrect ordering can prevent expected actions from being applied” (paraphrased from the Automation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers automation, stating that “sequential execution of automation rules requires careful configuration to ensure the correct actions are triggered” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “playbook creation and automation” as a key exam topic, encompassing automation rule configuration.
An XDR engineer is configuring an automation playbook to respond to high-severity malware alerts by automatically isolating the affected endpoint and notifying the security team via email. The playbook should only trigger for alerts generated by the Cortex XDR analytics engine, not custom BIOCs. Which two conditions should the engineer include in the playbook trigger to meet these requirements? (Choose two.)
Alert severity is High
Alert source is Cortex XDR Analytics
Alert category is Malware
Alert status is New
In Cortex XDR,automation playbooks(also referred to as response actions or automation rules) allow engineers to define automated responses to specific alerts based on trigger conditions. The playbook in this scenario needs to isolate endpoints and send email notifications for high-severity malware alerts generated by the Cortex XDR analytics engine, excluding custom BIOC alerts. To achieve this, the engineer must configure the playbook trigger with conditions that match the alert’s severity, category, and source.
Correct Answer Analysis (A, C):
A. Alert severity is High: The playbook should only trigger for high-severity alerts, as specified in the requirement. Setting the conditionAlert severity is Highensures that only alerts with a severity level of "High" activate the playbook, aligning with the engineer’s goal.
C. Alert category is Malware: The playbook targets malware alerts specifically. The conditionAlert category is Malwareensures that the playbook only responds to alerts categorized as malware, excluding other types of alerts (e.g., lateral movement, exploit).
Why not the other options?
B. Alert source is Cortex XDR Analytics: While this condition would ensure the playbook triggers only for alerts from the Cortex XDR analytics engine (and not custom BIOCs), the requirement to exclude BIOCs is already implicitly met because BIOC alerts are typically categorized differently (e.g., as custom alerts or specific BIOC categories). The alert category (Malware) and severity (High) conditions are sufficient to target analytics-driven malware alerts, and adding the source condition is not strictly necessary for the stated requirements. However, if the engineer wanted to be more explicit, this condition could be considered, but the question asks for the two most critical conditions, which are severity and category.
D. Alert status is New: The alert status (e.g., New, In Progress, Resolved) determines the investigation stage of the alert, but the requirement does not specify that the playbook should only trigger for new alerts. Alerts with a status of "InProgress" could still be high-severity malware alerts requiring isolation, so this condition is not necessary.
Additional Note on Alert Source: The requirement to exclude custom BIOCs and focus on Cortex XDR analytics alerts is addressed by theAlert category is Malwarecondition, as analytics-driven malware alerts (e.g., from WildFire or behavioral analytics) are categorized as "Malware," while BIOC alerts are often tagged differently (e.g., as custom rules). If the question emphasized the need to explicitly filter by source, option B would be relevant, but the primary conditions for the playbook are severity and category.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains automation playbook triggers: “Playbook triggers can be configured with conditions such as alert severity (e.g., High) and alert category (e.g., Malware) to automate responses like endpoint isolation and email notifications” (paraphrased from the Automation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers playbook creation, stating that “conditions like alert severity and category ensure playbooks target specific alert types, such as high-severity malware alerts from analytics” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “playbook creation and automation” as a key exam topic, encompassing trigger condition configuration.
Based on the image of a validated false positive alert below, which action is recommended for resolution?

Create an alert exclusion for OUTLOOK.EXE
Disable an action to the CGO Process DWWIN.EXE
Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module
Create an exception for OUTLOOK.EXE for ROP Mitigation Module
In Cortex XDR, a false positive alert involvingOUTLOOK.EXEtriggering aCGO (Codegen Operation)alert related toDWWIN.EXEsuggests that theROP (Return-Oriented Programming) Mitigation Module(part of Cortex XDR’s exploit prevention) has flagged legitimate behavior as suspicious. ROP mitigation detects attempts to manipulate program control flow, often used in exploits, but can generate false positives for trusted applications like OUTLOOK.EXE. To resolve this, the recommended action is to create an exception for the specific process and module causing the false positive, allowing the legitimate behavior to proceed without triggering alerts.
Correct Answer Analysis (D):Create an exception for OUTLOOK.EXE for ROP Mitigation Moduleis the recommended action. Since OUTLOOK.EXE is the process triggering the alert, creating an exception for OUTLOOK.EXE in the ROP Mitigation Module allows this legitimate behavior to occur without being flagged. This is done by adding OUTLOOK.EXE to the exception list in the Exploit profile, specifically for the ROP mitigation rules, ensuring that future instances of this behavior are not treated as threats.
Why not the other options?
A. Create an alert exclusion for OUTLOOK.EXE: While an alert exclusion can suppress alerts for OUTLOOK.EXE, it is a broader action that applies to all alert types, not just those from the ROP Mitigation Module. This could suppress other legitimate alerts for OUTLOOK.EXE, reducing visibility into potential threats. An exception in the ROP Mitigation Module is more targeted.
B. Disable an action to the CGO Process DWWIN.EXE: Disabling actions for DWWIN.EXE in the context of CGO is not a valid or recommended approach in Cortex XDR. DWWIN.EXE (Dr. Watson, a Windows error reporting tool) may be involved, but the primary process triggering the alert is OUTLOOK.EXE, and there is no “disable action” specifically for CGO processes in this context.
C. Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module: While DWWIN.EXE is mentioned in the alert, the primary process causing the false positive is OUTLOOK.EXE, as it’s the application initiating the behavior. Creating an exception for DWWIN.EXE would not address the root cause, as OUTLOOK.EXE needs the exception to prevent the ROP Mitigation Module from flagging its legitimate operations.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains false positive resolution: “To resolve false positives in the ROP Mitigation Module, create an exception for the specific process (e.g., OUTLOOK.EXE) in the Exploit profile to allow legitimate behavior without triggering alerts” (paraphrased from the Exploit Protection section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers exploit prevention tuning, stating that “exceptions for processes like OUTLOOK.EXE in the ROP Mitigation Module prevent false positives while maintaining protection” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing false positive resolution.
How long is data kept in the temporary hot storage cache after being queried from cold storage?
1 hour, re-queried to a maximum of 12 hours
24 hours, re-queried to a maximum of 7 days
24 hours, re-queried to a maximum of 14 days
1 hour, re-queried to a maximum of 24 hours
In Cortex XDR, data is stored in different tiers:hot storage(for recent, frequently accessed data),cold storage(for older, less frequently accessed data), and atemporary hot storage cachefor data retrieved from cold storage during queries. When data is queried from cold storage, it is moved to the temporary hot storage cache to enable faster access for subsequent queries. The question asks how long this data remains in the cache and the maximum duration for re-queries.
Correct Answer Analysis (B):Data retrieved from cold storage is kept in the temporary hot storage cache for24 hours. If the data is re-queried within this period, it remains accessible in the cache. The maximum duration for re-queries is7 days, after which the data may need to be retrieved from cold storage again, incurring additional processing time.
Why not the other options?
A. 1 hour, re-queried to a maximum of 12 hours: These durations are too short and do not align with Cortex XDR’s data retention policies for the hot storage cache.
C. 24 hours, re-queried to a maximum of 14 days: While the initial 24-hour cache duration is correct, the 14-day maximum for re-queries is too long and not supported by Cortex XDR’s documentation.
D. 1 hour, re-queried to a maximum of 24 hours: The 1-hour initial cache duration is incorrect, as Cortex XDR retains queried data for 24 hours.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains data storage: “Data queried from cold storage is cached in hot storage for 24 hours, with a maximum re-query period of 7 days” (paraphrased from the Data Management section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers data retention, stating that “queried cold storage data remains in the hot cache for 24 hours, accessible for up to 7 days with re-queries” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “maintenance and troubleshooting” as a key exam topic, encompassing data storage management.
A security audit determines that the Windows Cortex XDR host-based firewall is not blocking outbound RDP connections for certain remote workers. The audit report confirms the following:
All devices are running healthy Cortex XDR agents.
A single host-based firewall rule to block all outbound RDP is implemented.
The policy hosting the profile containing the rule applies to all Windows endpoints.
The logic within the firewall rule is adequate.
Further testing concludes RDP is successfully being blocked on all devices tested at company HQ.
Network location configuration in Agent Settings is enabled on all Windows endpoints.What is the likely reason the RDP connections are not being blocked?
The profile's default action for outbound traffic is set to Allow
The pertinent host-based firewall rule group is only applied to external rule groups
Report mode is set to Enabled in the report settings under the profile configuration
The pertinent host-based firewall rule group is only applied to internal rule groups
Cortex XDR’shost-based firewallfeature allows administrators to define rules to control network traffic on endpoints, such as blocking outbound Remote Desktop Protocol (RDP) connections (typically on TCP port 3389). The firewall rules are organized intorule groups, which can be applied based on the endpoint’snetwork location(e.g., internal or external). Thenetwork location configurationin Agent Settings determines whether an endpoint is considered internal (e.g., on the company network at HQ) or external (e.g., remote workers on a public network). The audit confirms that a rule to block outbound RDP exists, the rule logic is correct, and it works at HQ but not for remote workers.
Correct Answer Analysis (D):The likely reason RDP connections are not being blocked for remote workers is thatthe pertinent host-based firewall rule group is only applied to internal rule groups. Since network location configuration is enabled, Cortex XDR distinguishes between internal (e.g., HQ) and external (e.g., remote workers) networks. If the firewall rule group containing the RDP block rule is applied only tointernal rule groups, it will only take effect for endpoints at HQ (internal network), as confirmed by the audit. Remote workers, on an external network, would not be subject to this rule group, allowing their outbound RDP connections to proceed.
Why not the other options?
A. The profile's default action for outbound traffic is set to Allow: While a default action of Allow could permit traffic not matched by a rule, the audit confirms the RDP block rule’s logic is adequate and works at HQ. This suggests the rule is being applied correctly for internal endpoints, but not for external ones, pointing to a rule group scoping issue rather than the default action.
B. The pertinent host-based firewall rule group is only applied to external rule groups: If the rule group were applied only to external rule groups, remote workers (on external networks) would have RDP blocked, but the audit shows the opposite—RDP is blocked at HQ (internal) but not for remote workers.
C. Report mode is set to Enabled in the report settings under the profile configuration: If report mode were enabled, the firewall rule would only log RDP traffic without blocking it, but this would affect all endpoints (both HQ and remote workers). The audit shows RDP is blocked at HQ, so report mode is not enabled.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains host-based firewall configuration: “Firewall rule groups can be applied to internal or external network locations, as determined by the network location configuration in Agent Settings. Rules applied to internal rule groups will not affect endpoints on external networks” (paraphrased from the Host-Based Firewall section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers firewall rules, stating that “network location settings determine whether a rule group applies to internal or external endpoints, impacting rule enforcement” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration” as a key exam topic, encompassing host-based firewall settings.
Copyright © 2021-2026 CertsTopics. All Rights Reserved

