The listener configuration contains these lines related to Valid Node Checking for Registration (VNCR);

Which two statements are true?
Examine these commands and responses:
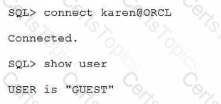
User Karen is an enterprise user.
Which two commands are used to allow this login?
A policy predicate function Is associated with an enabled Virtual Private Database (VPD) policy for a table.
Which two arguments are passed to the function?
You are Implementing a security policy that makes use of the USERENV namespace.
Which USERRENV value does not change for the duration of a session?
What does the Application Data Modeling module of the Oracle Data Masking and Subsetting Pack search for?
The sqinet.oia file on the client contains this parameter setting:
SQLNET.ENCRYPTION_CLIEKT = REQUESTED
What value for the parameter sQLNET.ENCRYPTION _server In the sqlnet.ora file on the server will disable Encryption and Data Negotiation?
Which two tasks should you perform initially to Implement native network encryption without disrupting client applications?
You Issue this statement as user SYS:
audit, context namespace kilimanjaro attributes a, b;
Which is true?
Examine this query:
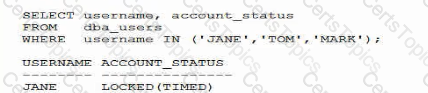
Why is this account in this status?
Database Vault is configured and enabled in the database. You create a rule set to enforce security on the hr. employees table.
Examine these requirements:
1. Users working In hr department are allowed to view all rows In HR.EMPLOYEES.
2. hr managers are allowed to view, update, and delete data in In HR.EMPLOYEES.
3. Audit records are to be collected for every evaluation of the rule set.
Which two options are true when creating the rule set?
You export and Import a table's data using Data Pump connected as a user who Is assigned DBA role with default privileges.
There is a data redaction policy on the table.
Which two statements are true about the redaction policy?
Which statement is true about Network ACLs?
You must mask data consistently In three database copies such that data relations across the databases remain In place.
Which Data Masking Format allows this?