You need to enable and configure Microsoft Defender for Endpoint to meet the security requirements. What should you do?
You need to configure threat detection for Active Directory. The solution must meet the security requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
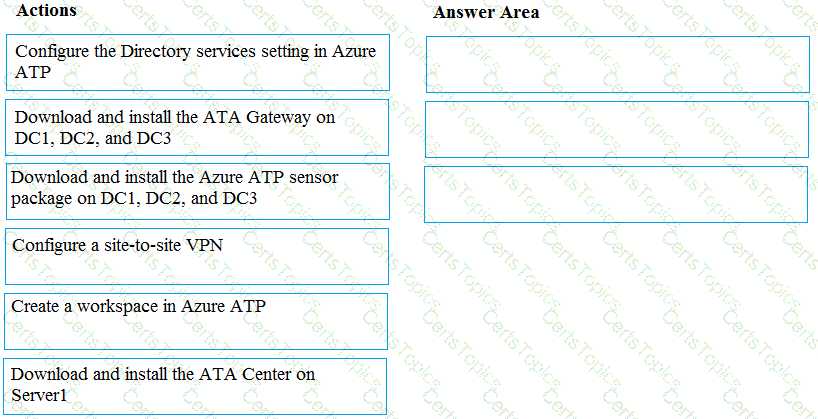
How should you configure Azure AD Connect? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
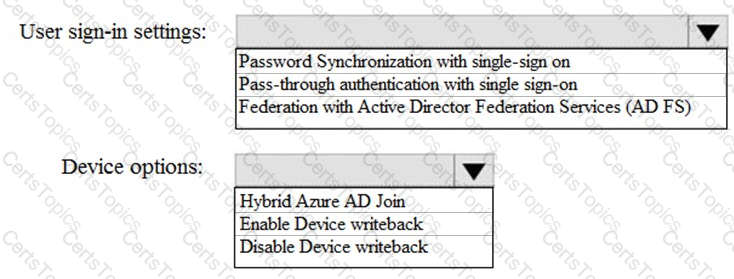
How should you configure Group3? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
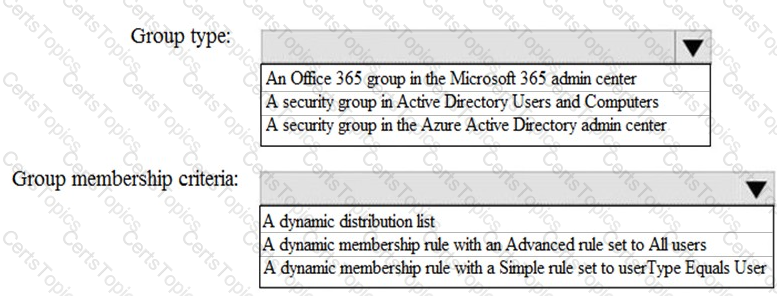
You need to create Group3.
What are two possible ways to create the group?
Which IP address space should you include in the MFA configuration?
You need to implement Windows Defender ATP to meet the security requirements. What should you do?
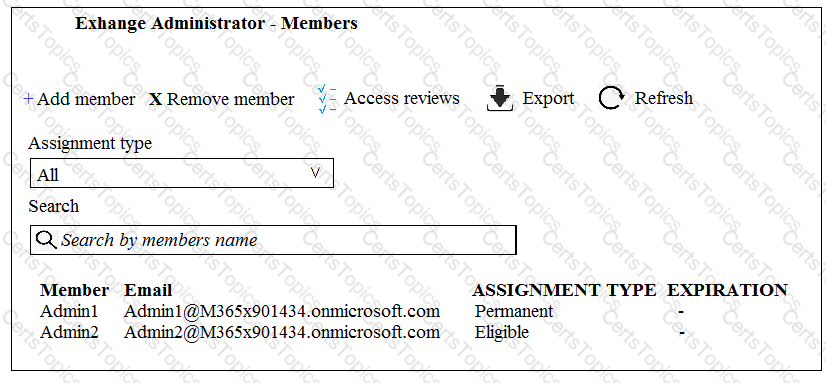
You need to recommend a solution to protect the sign-ins of Admin1 and Admin2.
What should you include in the recommendation?
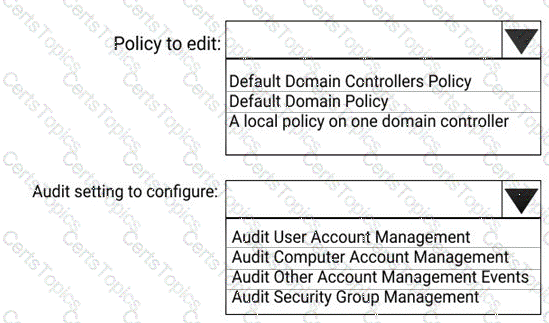
You need to recommend a solution for the user administrators that meets the security requirements for auditing.
Which blade should you recommend using from the Azure Active Directory admin center?
NO: 7
You need to resolve the issue that targets the automated email messages to the IT team.
Which tool should you run first?
You need to recommend a solution that meets the technical and security requirements for sharing data with the partners.
What should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
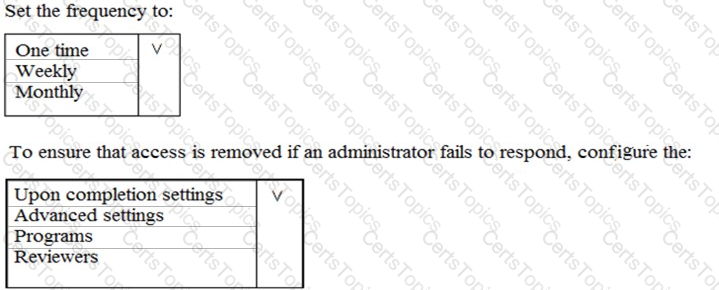
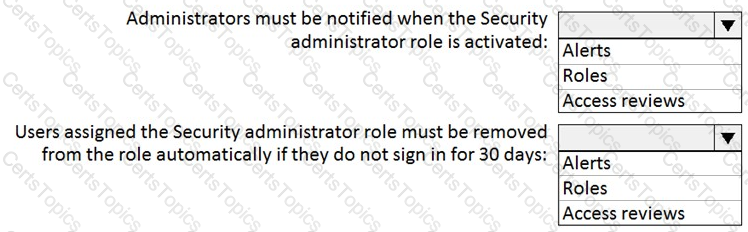
You plan to configure an access review to meet the security requirements for the workload administrators. You create an access review policy and specify the scope and a group.
Which other settings should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
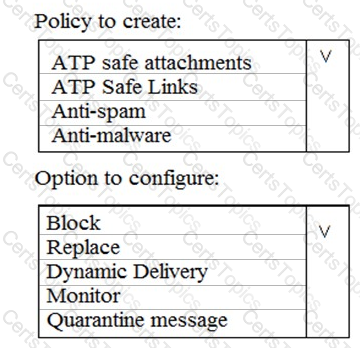
You need to recommend an email malware solution that meets the security requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You install Azure ATP sensors on domain controllers.
You add a member to the Domain Admins group. You view the timeline in Azure ATP and discover that information regarding the membership change is missing.
You need to meet the security requirements for Azure ATP reporting.
What should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
An administrator configures Azure AD Privileged Identity Management as shown in the following exhibit.
What should you do to meet the security requirements?
You have a Microsoft 365 subscription for a company named Contoso, Ltd. All data is in Microsoft 365.
Contoso works with a partner company named Litware, Inc. Litware has a Microsoft 365 subscription.
You need to allow users at Contoso to share files from Microsoft OneDrive to specific users at Litware.
Which two actions should you perform from the OneDrive admin center? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
You need to recommend an Azure AD Privileged Identity Management (PIM) solution that meets the following requirements:
Which Azure AD PIM setting should you recommend configuring for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
A security manager receives an email message every time a data loss prevention (DLP) policy match occurs.
You need to limit alert notifications to actionable DLP events.
What should you do?
You have several Conditional Access policies that block noncompliant devices from connecting to services.
You need to identify which devices are blocked by which policies.
What should you use?
You configure Microsoft Azure Active Directory (Azure AD) Connect as shown in the following exhibit.
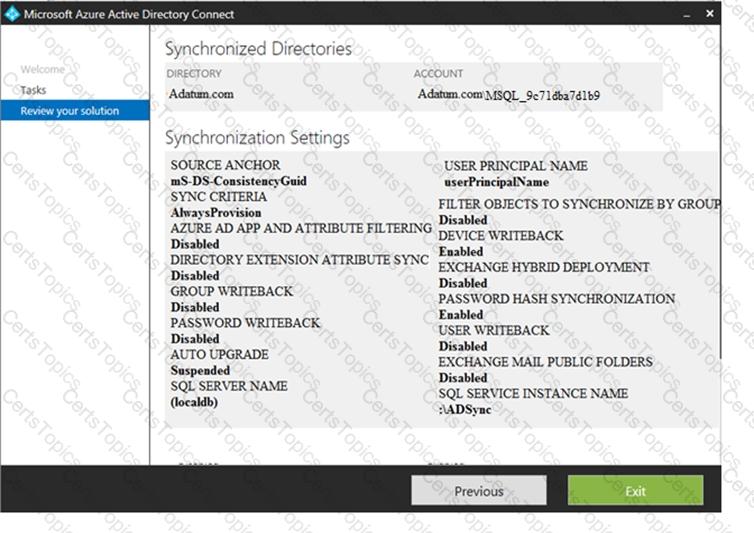
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
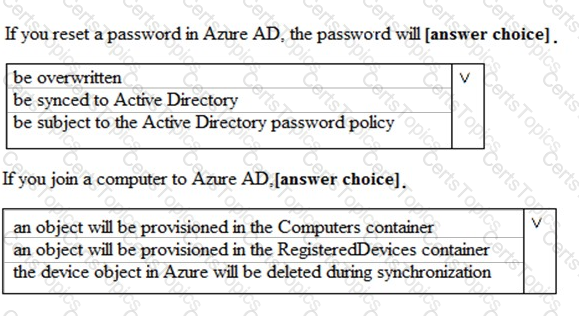
You company has a Microsoft 36S E5 subscription and a hybrid Azure active Directory named contoso.com.
Contoso.com includes the following users:
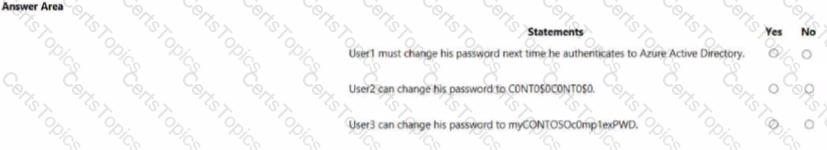
You configure Password protection for Contoso.com as shown in the following exhibit.

You view Compliance Manager as shown in the following exhibit.
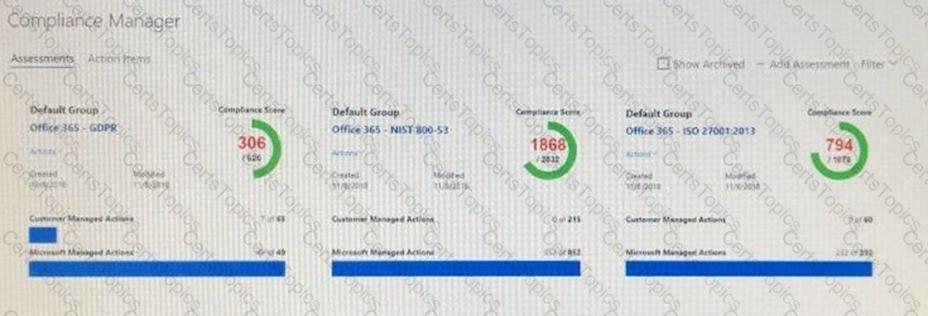
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
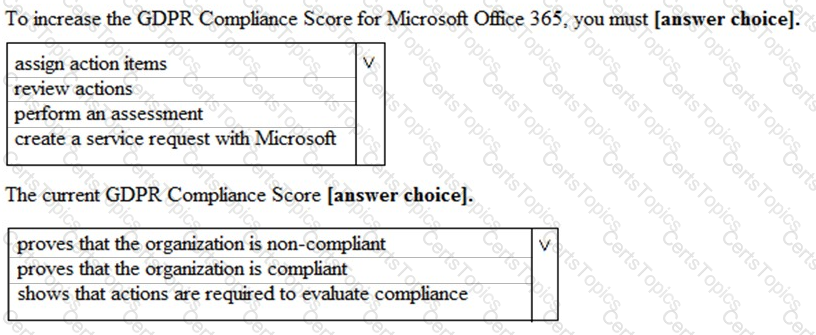
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
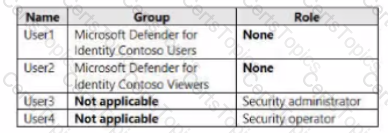
You discover that several security alerts are visible from the Microsoft Defender for Identity portal.
You need to identify which users in contoso.com can close the security alerts.
Which users should you identify?
You have a Microsoft 365 alert named Alert?
as shown in the following exhibit.
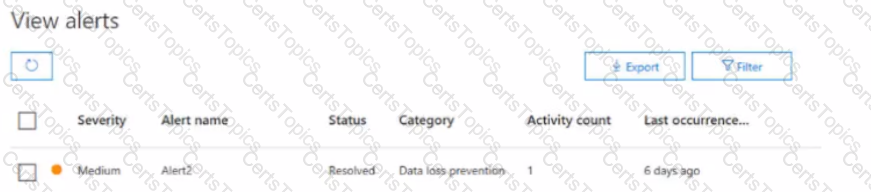
You need to manage the status of Alert2. To which status can you change Alert2?
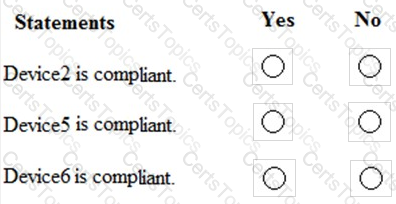
You are evaluating which devices are compliant in Intune.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
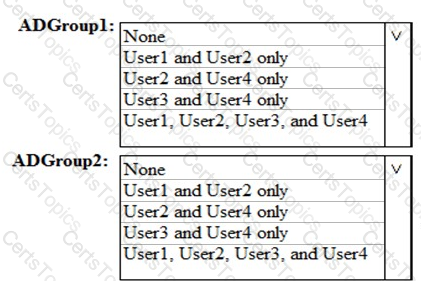
Which users are members of ADGroup1 and ADGroup2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
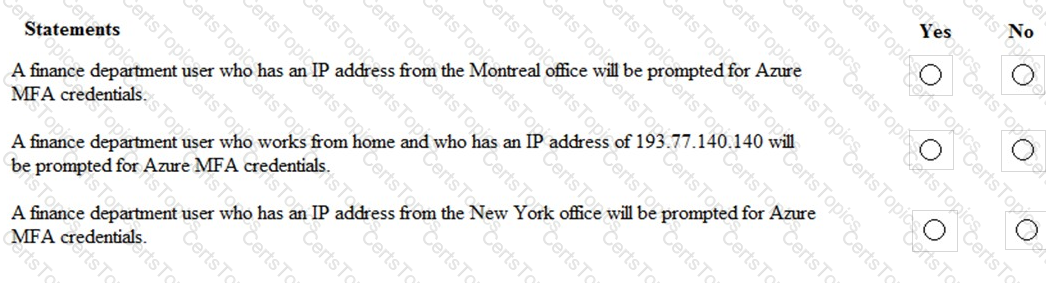
You are evaluating which finance department users will be prompted for Azure MFA credentials.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What should User6 use to meet the technical requirements?
Which user passwords will User2 be prevented from resetting?
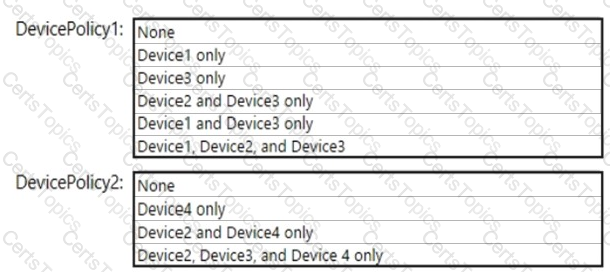
Which policies apply to which devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Which role should you assign to User1?
You need to meet the technical requirements for User9. What should you do?