Which Informix utility is used to print information about runtime statistics for all threads in the server?
When you take a level 2 backup, what data is backed up?
Which two statements are true about Enterprise Replication of TimeSeries data types? (Choose two.)
Which step must be performed to enable Secure Socket Layer (SSL) connections to Informix?
What is the primary benefit of a Storage Pool?
Which of the following is NOT possible during a non-root Informix Server installation?
The IBM Mobile Database is a mobile-optimized version of which IBM product?
What security role is required for you to create trusted-context objects?
Which statement is valid about Data consolidation using send-only replicates?
Consider the following statements: DBSPACETEMP=tempdbs1, tempdbs2, tempdbs3; CREATE DATABASE mydb WITH LOG IN datadbs1; CREATE TEMP TABLE temp1 (col1 int); Which statement is true?
Which Enterprise Replication command CANNOT be used on replicates that include TimeSeries columns?
Which two technologies use the ENCRYPT_MAC configuration parameter to control the level of message authentication code (MAC) generation? (Choose two.)
Which statement is true regarding the selective row-level auditing feature in Informix?
To potentially return unused extent pages to the chunk free list, an Informix administrator would execute which storage optimization operation?
The DBA wants to define a replicate as follows:
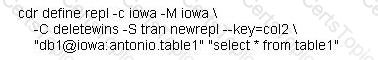
Which condition must be true for the command to execute successfully?
An Informix server is configured with multiple CPU VPs and poll threads and is experiencing NSF lock errors. What action should be taken to reduce the network shared file lock contention?
Which configuration parameter should be set to enable asynchronous page requests when the database server detects that a query is waiting on I/O?
The Rolling Window clause of the ALTER FRAGMENT MODIFY INTERVAL statement CANNOT define a purging policy on a table that has which two attributes? (Choose two.)
Where must the HA_FOC_ORDER configuration parameter be set?