In the Huawei SD-WAN Solution, which of the following routing protocols is used to advertise VPN routes between CPEs?
Flavors can be used to enhance SRv6 instructions to meet more diversified service requirements. Which of the following are flavors? (Select all that apply)
Which of the following can be used to transmit traffic to a VXLAN network and implement intra-subnet communication on the same VXLAN network?
In OSPFv3, which of the following types of LSAs can be flooded in the entire AS?
On a CloudCampus virtualized campus network, service data enters different VNs from physical networks through edge nodes, and the VN that the data will enter is determined by the VLANs to which users belong. Which of the following statements about dynamic VLAN authorization is incorrect?
In OSPFv3, which of the following LSAs can be flooded within an area?
When you configure a virtualized campus network on iMaster NCE-Campus and enable external networks to connect to the Internet, iMaster NCE-Campus will automatically deliver a specific route to direct traffic to the corresponding external network.
YANG is a data modeling language for the definition of data sent over network management protocols such as NETCONF. Which of the following are basic YANG data models? (Select all that Apply)
Which of the following functions can be provided by iMaster NCE-Campus when it functions as a relay agent for authentication?
An Ethernet Segment Identifier (ESI) is 10 bytes long and unique on the entire network.
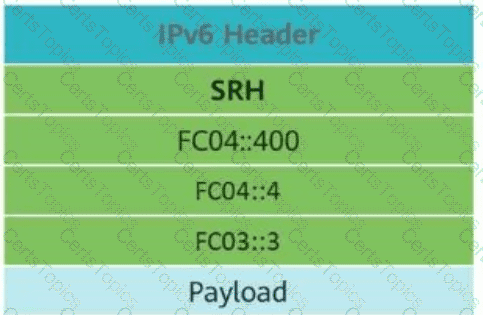
This figure shows anSRv6 (Segment Routing over IPv6)packet. If theDestination Addressfield in the IPv6 basic header isFC04::4, the value of theSL (Segment Left)field in the SRv6 header should be____.(Enter only digits.)
On traditional campus networks, network admission control (NAC), VLAN, and ACL technologies are used to control users' network access rights. This results in heavy network O&M workload. Which of the following improvements does the free mobility solution of iMaster NCE-Campus make to traditional campus networks in terms of policy management and control?
Which of the following technologies can be used to isolate users in the same VLAN?
In the CloudCampus public cloud scenario, if deployment through the Huawei registration query center is used, you do not need to configure DHCP Option 148 on the DHCP server of the campus network.
SR-MPLS uses the MPLS forwarding plane, and therefore requires MPLS to be enabled. Which of the following conditions must be met for MPLS to be automatically enabled on an interface? (Select all that apply)
The BGP ORF function can be used to control the maximum number of routes that can be sent by a BGP peer. To achieve this, which of the following tools is used to send such a route list to BGP peers?
In the admission design for large- and medium-sized campus networks, which of the following authentication modes can be used for PCs connected to IP phones?
If SRv6 needs to be deployed on a bearer WAN, which of the following technologies are required? (Select all that apply)
Which of the following statements is correct about the differences between NSR and NSF?
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
Which of the following commands needs to be run in the BGP view to enable a VPN instance to advertise IP routes to the BGP-EVPN address family?
When an NVE encapsulates a data frame into a VXLAN packet, information of which of the following protocols is encapsulated between the outer IP header and the VXLAN header?
On a VXLAN-based virtualized network, if the fabric networking mode is centralized gateway networking, the gateway is located on the _____ device. (Capitalize the first letter.)
Huawei Open Programmability System (OPS) provides openness and programmability capabilities for network devices and enables users to perform secondary development. To facilitate script completion, Huawei OPS provides the Python script template in which the OPSConnection class is created. The member function for creating device resources is def post(self, uri, req_data).
The free mobility function is deployed on the iMaster NCE-Campus on a campus network. Which of the following information should an administrator pay attention to?
IS-IS supports multi-instance and multi-process. Which of the following statements are correct about IS-IS multi-instance and multi-process?
Which of the following community attributes ensure that BGP routes are transmitted only within an AS?
On a CloudCampus virtualized campus network, virtual networks are defined based on services. Each virtual network corresponds to a service, and isolation needs to be manually configured between virtual networks.
An LSR supports various label retention modes. Which of the following statements regarding the liberal mode are correct?
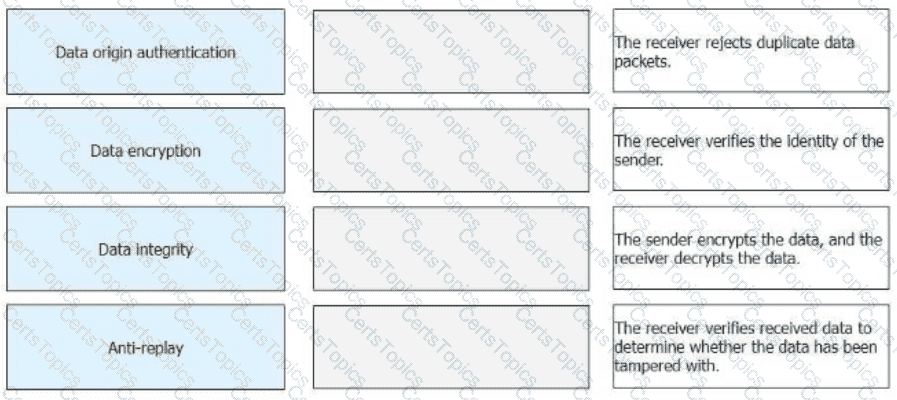
Drag theIPsec functionson the left to the corresponding function description on the right.
Network administrator A wants to use an IP prefix list to match specific routes. Which of the following routes can be matched by the IP prefix list shown in this figure?
ip ip-prefix TEST permit 10.0.0.0 24 less-equal 30
Congestion management technology can be used to discard data packets in the buffer queue to prevent the buffer queue from being exhausted.
What can be determined from the following figure?
Total Number of Routes: 2
*>i Network : 3002::3
NextHop : 3000:FDEA::3
MED : 0
Path/Orgn : i
*>i Network : 3002::4
NextHop : 3000:FDEA::3
MED : 0
PrefixLen : 128
LocPrf : 100
PrefVal : 0
Path/Orgn : 65001 i
MPLS supports Forwarding Equivalence Class (FEC). Which of the following cannot be used as a FEC allocation standard?
MPLS is located between the data link layer and network layer in the TCP/IP protocol stack and can provide services for all network layer protocols.
A network administrator runs the display telemetry destination command on a device to check information about a destination group that sampled data is sent to. The command output is as follows. Which of the following statements is incorrect?
[~CE-telemetry-sensor-group-Sensor1]display telemetry destination
Dest-name Dest-addr Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
The following information is displayed during OSPF troubleshooting. Based on this information, which of the following is the cause of the failure in establishing an OSPF adjacency relationship?
OSPF Process 1 with Router ID 10.0.12.2
OSPF error statistics
Interface: GigabitEthernet0/0/0 (10.0.12.2)
General packet errors:
0 : Bad version 0 : Bad checksum
0 : Bad area id 0 : Bad authentication type
0 : Bad authentication key 0 : Unknown neighbor
0 : Bad net segment 0 : Extern option mismatch
0 : Router id confusion
HELLO packet errors:
2 : Netmask mismatch 0 : Hello timer mismatch
0 : Dead timer mismatch 0 : Invalid Source Address
OSPF is deployed on a campus network to implement network interconnection. The LSDB of R2 is shown in the figure.
What can be determined from the LSDB?
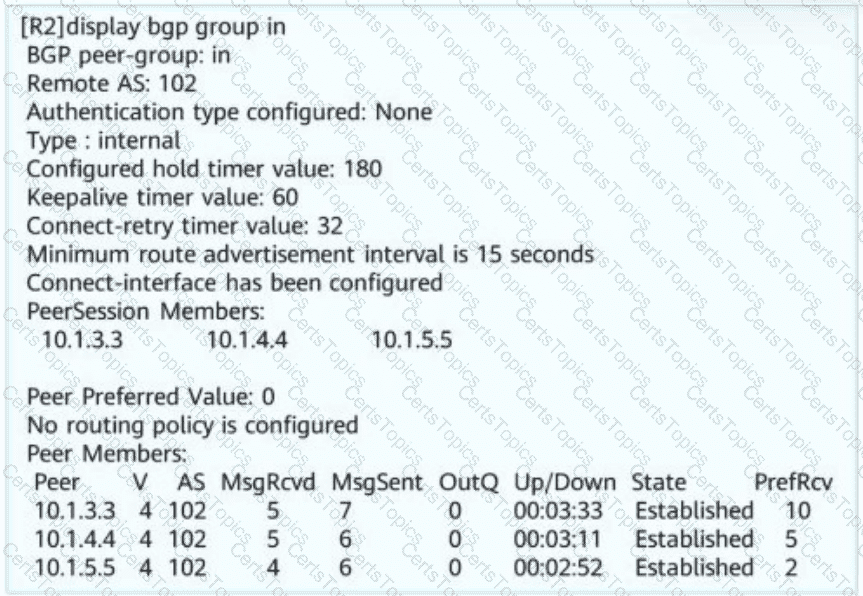
Network administrator A wants to view the BGP peer status of R2. The BGP peer status of R2 is shown in this figure. Obtain the following information: R2 resides in AS _____ (Enter only digits. Do not add punctuations or spaces.)
The channelized sub-interface and FlexE technologies both can be used to implement network slicing, but the application scenarios of the two technologies are slightly different. Which of the following statements about the two technologies are correct?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following command needs to be run on the VBDIF interface to enable the VTEP peer to generate BGP EVPN Type 2 routes based on ARP information of the local terminal?
By default, the domain ID of an OSPF process is the same as the process ID. You can run the domain-id command in the OSPF process view to change a domain ID.
Network Quality Analysis (NQA) is a real-time network performance detection and measurement technology. It monitors the performance of multiple protocols running on a network. Which of the following protocols can be monitored by NQA?
Huawei Open Programmability System (OPS) uses HTTP methods to access managed objects to manage network devices. Drag the HTTP methods to their corresponding functions.

Which of the following issues do DiffServ model-based QoS have?
Drag the OSPFv3 LSAs to map them to their corresponding transmission ranges.

Which of the following methods can be used to establish IPsec SAs? (Select All that Apply)
Which of the following are application optimization functions in the Huawei SD-WAN Solution?
Which of the following statements about the multicast address used by OSPFv3 are correct?
An engineer often remotely logs in to the device to check the device status. The engineer can use the Python Paramiko and telnetlib libraries to implement automatic remote login through Python scripts. The remote login implemented using telnetlib is more secure.
The ________ command can be run to completely isolate Layer 2 and Layer 3 of different interfaces in a VLAN. (Use lowercase letters to supplement the command, which cannot be abbreviated.)
Based on the configuration in the following figure, how many interfaces on R4 are advertised into IS-IS?
plaintext
CopyEdit
Interface information for ISIS(1)
Interface Id IPV4.State IPV6.State MTU Type DIS
GE0/0/0 001 Up Down 1497 L1/L2 No/No
GE0/0/1 002 Up Down 1497 L1/L2 No/No
Loop0 001 Up Down 1500 L1/L2 -
A carrier's home broadband service requires a maximum downstream bandwidth of 100 Mbit/s during off-peak hours and a guaranteed downstream bandwidth of 50 Mbit/s during peak hours. The home broadband service includes the home IP phone service and the home Internet access service. Which of the following configurations best meets the service requirement?
Which of the following statements about DHCP snooping isincorrect?
iMaster NCE-Campus restricts RESTful APIs. If a client sends aGET requestthat invokes a RESTful API to obtain site information from iMaster NCE-Campus, which of the following fields should be included in the request header?
How long is an IPv6 prefix assigned to a host when an IPv6 address is configured for the host in SLAAC mode?
You write the following Python code to invoke a RESTful API to obtain the token ID of iMaster NCE. Which of the following statements are correct?
import requests
response = requests.get(" ")
print(response.json())
Error returned:
requests.exceptions.SSLError: HTTPSConnectionPool(host='139.9.213.72', port=18002): Max retries exceeded with url: /controller/v2/tokens (Caused by SSLError(CertificateError('hostname '139.9.213.72' doesn't match 'devzone.huawei.com')))
Options:
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
Exhibit:
A loop occurs because Spanning Tree Protocol (STP) is not enabled on the network. Which of the following symptoms may occur?