Your organization has moved to AWS and has manually deployed infrastructure using the console. Recently, a decision has been made to standardize on Terraform for all deployments moving forward.
What can you do to ensure that all existing is managed by Terraform moving forward without interruption to existing services?
When creating a dynamic secret in Vault, Vault returns what value that can be used to renew or revoke the lease?
When writing the Terraform code, HashiCorp recommends that you use how many spaces between each nesting level?
You want to encrypt a credit card number using the transit secrets engine. You enter the following command and receive an error. What can you do to ensure that the credit card number is properly encrypted and the ciphertext is returned?
1. $ vault write -format=json transit/encrypt/creditcards plaintext="1234 5678 9101 1121"
2. Error writing data to transit/encrypt/orders: Error making API request.
3.
4. URL: PUT
5. Code: 400. Errors:
6.
7. * illegal base64 data at input byte 4
After encrypting data using the transit secrets engine, you've received the following output. Which of the following is true based upon the output?
1. Key Value
2. --- -----
3. ciphertext vault:v2:45f9zW6cglbrzCjI0yCyC6DBYtSBSxnMgUn9B5aHcGEit71xefPEmmjMbrk3
In regards to using a K/V v2 secrets engine, select the three correct statements below: (select three)
Which of the following Vault policies will allow a Vault client to read a secret stored at secrets/applications/app01/api_key?
When administering Vault on a day-to-day basis, why is logging in with the root token, as shown below, a bad idea? (select two).

You are deploying Vault in a local data center, but want to be sure you have a secondary cluster in the event the primary cluster goes offline. In the secondary data center, you have applications that are running, as they are architected to run active/active. Which type of replication would be best in this scenario?
What happens to child tokens when a parent token is revoked?
As opposed to service tokens, batch tokens are ideal for what type of action?
What is the best and easiest way for Terraform to read and write secrets from HashiCorp Vault?
Which is not a capability that can be used when writing a Vault policy?
What does the command terraform fmt do?
Choose the correct answer which fixes the syntax of the following Terraform code:
What system endpoint can you query to determine which node is the leader of a cluster?
If a client is currently assigned the following policy, what additional policy can be added to ensure they cannot access the data stored at secret/apps/confidential but still, read all other secrets?
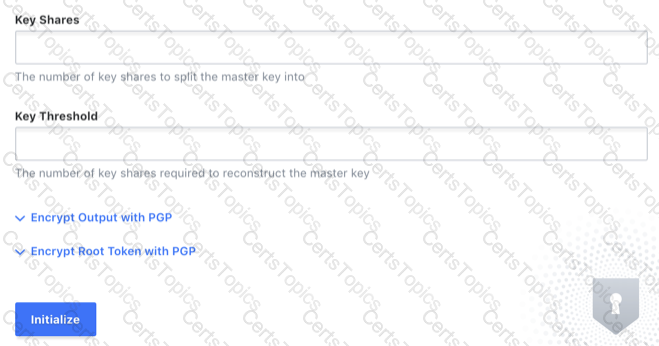
You've hit the URL for the Vault UI, but you're presented with this screen. Why doesn't Vault present you with a way to log in?
What is a downside to using a Terraform provider, such as the Vault provider, to interact with sensitive data, such as reading secrets from Vault?
By default, the max TTL for a token is how many days?
While Terraform is generally written using the HashiCorp Configuration Language (HCL), what another syntax can Terraform be expressed in?
By default, where does Terraform store its state file?
Which of the following actions are performed during a terraform init? (select three)
In a Consul cluster, participating nodes can be only one of two types. Select the valid types. (select two)
Select all Operating Systems that Terraform is available for. (select five)
You've deployed Vault in your production environment and are curious to understand metrics on your Vault cluster, such as the number of writes to the backend, the status of WALs, and the seal status. What feature would you configure in order to view these metrics?
What Terraform command can be used to inspect the current state file?
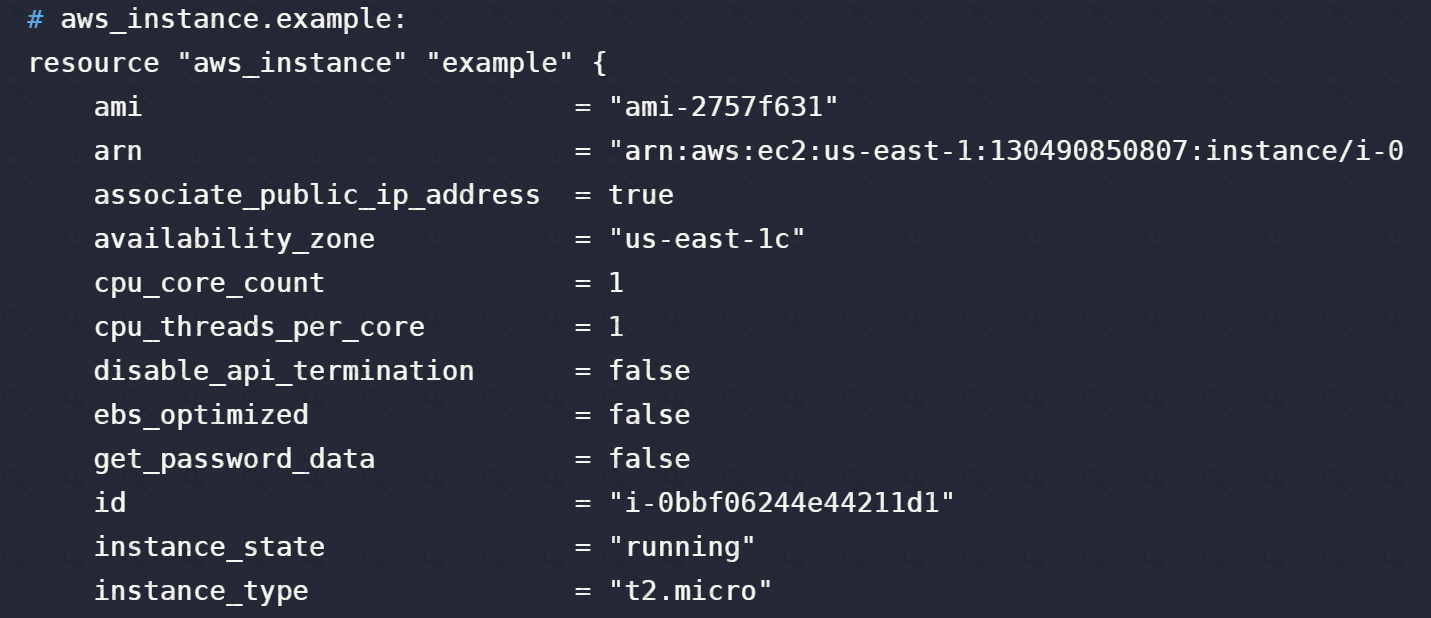
Complete the following sentence:
The terraform state command can be used to ____
Select the operating systems which are supported for a clustered Terraform Enterprise: (select four)
Select the feature below that best completes the sentence:
The following list represents the different types of __________ available in Terraform.
1. max
2. min
3. join
4. replace
5. list
6. length
7. range