To view Files Written to Removable Media within a specified timeframe on a host within the Host Search page, expand and refer to the _______dashboard panel.
In the MITRE ATT&CK Framework (version 11 - the newest version released in April 2022), which of the following pair of tactics is not in the Enterprise: Windows matrix?
Which of the following is the proper method to quantify search results, enabling a hunter to quickly sort and identify outliers?
You are reviewing a list of domains recently banned by your organization's acceptable use policy. In particular, you are looking for the number of hosts that have visited each domain. Which tool should you use in Falcon?
Which of the following best describes the purpose of the Mac Sensor report?
Which tool allows a threat hunter to populate and colorize all known adversary techniques in a single view?
Which of the following is an example of actor actions during the RECONNAISSANCE phase of the Cyber Kill Chain?
Which structured analytic technique contrasts different hypotheses to determine which is the best leading (prioritized) hypothesis?
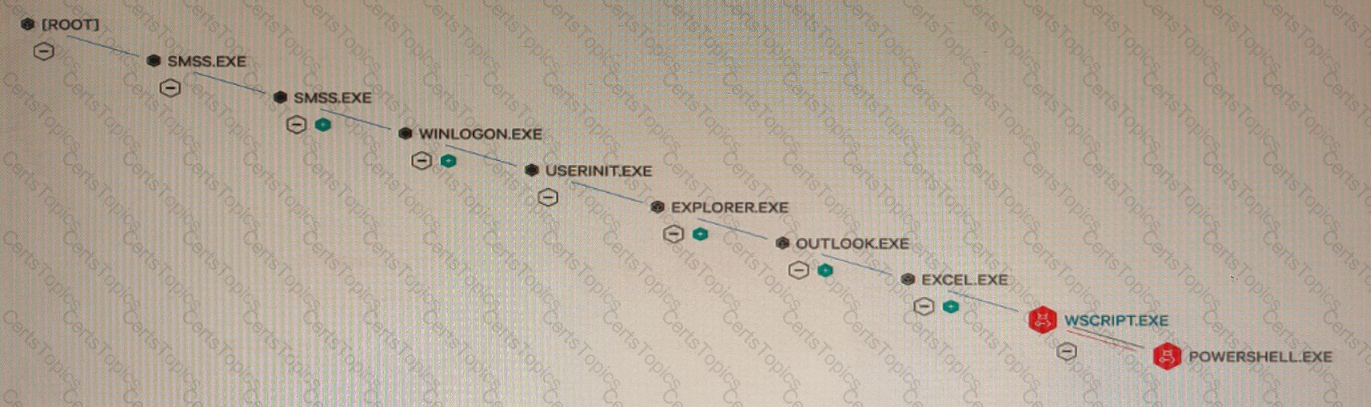
What type of attack would this process tree indicate?