A technician is connecting DSL for a new customer. After installing and connecting the on-premises equipment, the technician verifies DSL synchronization. When connecting to a workstation, however, the link LEDs on the workstation and modem do not light up. Which of the following should the technician perform during troubleshooting?
A network technician is investigating an issue with handheld devices in a warehouse. Devices have not been connecting to the nearest APs, but they have been connecting to an AP on the far side of the warehouse. Which of the following is the MOST likely cause of this issue?
Which of the following security devices would be BEST to use to provide mechanical access control to the MDF/IDF?
A SaaS provider has decided to leave an unpatched VM available via a public DMZ port. With which of the following concepts is this technique MOST closely associated?
A company requires a disaster recovery site to have equipment ready to go in the event of a disaster at its main datacenter. The company does not have the budget to mirror all the live data to the disaster recovery site. Which of the following concepts should the company select?
A city has hired a new employee who needs to be able to work when traveling at home and at the municipal sourcing of a neighboring city that snares services. The employee is issued a laptop, and a technician needs to train the employee on the appropriate solutions for secure access to the network from all the possible locations On which of the following solutions would the technician MOST likely train the employee?
A network administrator is talking to different vendors about acquiring technology to support a new project for a large company. Which of the following documents will MOST likely need to be signed before information about the project is shared?
A network administrator needs to implement an HDMI over IP solution. Which of the following will the network administrator MOST likely use to ensure smooth video delivery?
A network technician is investigating an issue with a desktop that is not connecting to the network. The desktop was connecting successfully the previous day, and no changes were made to the environment. The technician locates the switchport where the device is connected and observes the LED status light on the switchport is not lit even though the desktop is turned on Other devices that arc plugged into the switch are connecting to the network successfully Which of the following is MOST likely the cause of the desktop not connecting?
Which of the following is MOST commonly used to address CVEs on network equipment and/or operating systems?
Which of the following policies is MOST commonly used for guest captive portals?
An organization with one core and five distribution switches is transitioning from a star to a full-mesh topology Which of the following is the number of additional network connections needed?
Which of the following is used to provide networking capability for VMs at Layer 2 of the OSI model?
A customer wants to segregate the traffic between guests on a hypervisor. Which of the following does a technician need to configure to meet the requirement?
A network administrator decided to use SLAAC in an extensive IPv6 deployment to alleviate IP address management. The devices were properly connected into the LAN but autoconfiguration of the IP address did not occur as expected. Which of the following should the network administrator verify?
Given the following output:
Which of the following attacks is this MOST likely an example of?
A network administrator is configuring a database server and would like to ensure the database engine is listening on a certain port. Which of the following commands should the administrator use to accomplish this goal?
Two remote offices need to be connected securely over an untrustworthy MAN. Each office needs to access network shares at the other site. Which of the following will BEST provide this functionality?
Which of the following attacks encrypts user data and requires a proper backup implementation to recover?
A network engineer is designing a new secure wireless network. The engineer has been given the following requirements:
1 Must not use plaintext passwords
2 Must be certificate based
3. Must be vendor neutral
Which of the following methods should the engineer select?
Which of the following is a system that is installed directly on a server's hardware and abstracts the hardware from any guest machines?
A local firm has hired a consulting company to clean up its IT infrastructure. The consulting company notices remote printing is accomplished by port forwarding via publicly accessible IPs through the firm's firewall Which of the following would be the MOST appropriate way to enable secure remote printing?
A technician is troubleshooting a previously encountered issue. Which of the following should the technician reference to find what solution was implemented to resolve the issue?
A network administrator has been directed to present the network alerts from the past week to the company's executive staff. Which of the following will provide the BEST collection and presentation of this data?
A network administrator is reviewing interface errors on a switch. Which of the following indicates that a switchport is receiving packets in excess of the configured MTU?
A network administrator is downloading a large patch that will be uploaded to several enterprise switches simultaneously during the day's upgrade cycle. Which of the following should the administrator do to help ensure the upgrade process will be less likely to cause problems with the switches?
A wireless network was installed in a warehouse for employees to scan crates with a wireless handheld scanner. The wireless network was placed in the corner of the building near the ceiling for maximum coverage However users in the offices adjacent lo the warehouse have noticed a large amount of signal overlap from the new network Additionally warehouse employees report difficulty connecting to the wireless network from the other side of the building; however they have no issues when Ihey are near the antenna Which of the following is MOST likely the cause?
Which of the following would be used to expedite MX record updates to authoritative NSs?
A network technician is reviewing an upcoming project's requirements to implement laaS. Which of the following should the technician consider?
A company that uses VoIP telephones is experiencing intermittent issues with one-way audio and dropped conversations The manufacturer says the system will work if ping times are less than 50ms. The company has recorded the following ping times:

Which of the following is MOST likely causing the issue?
A technician is implementing a new wireless network to serve guests at a local office. The network needs to provide Internet access but disallow associated stations from communicating with each other. Which of the following would BEST accomplish this requirement?
A technician is deploying a low-density wireless network and is contending with multiple types of building materials. Which of the following wireless frequencies would allow for the LEAST signal attenuation?
A Chief Information Officer (CIO) wants to improve the availability of a company's SQL database Which of the following technologies should be utilized to achieve maximum availability?
A company is being acquired by a large corporation. As part of the acquisition process, the company's address should now redirect clients to the corporate organization page. Which of the following DNS records needs to be created?
An IT technician suspects a break in one of the uplinks that provides connectivity to the core switch. Which of the following command-line tools should the technician use to determine where the incident is occurring?
A systems administrator is running a VoIP network and is experiencing jitter and high latency. Which of the following would BEST help the administrator determine the cause of these issues?
A corporation has a critical system that would cause unrecoverable damage to the brand if it was taken offline. Which of the following disaster recovery solutions should the corporation implement?
A network field technician is installing and configuring a secure wireless network. The technician performs a site survey. Which of the following documents would MOST likely be created as a result of the site survey?
An IDS was installed behind the edge firewall after a network was breached. The network was then breached again even though the IDS logged the attack. Which of the following should be used in place of these devices to prevent future attacks?
There are two managed legacy switches running that cannot be replaced or upgraded. These switches do not support cryptographic functions, but they are password protected. Which of the following should a network administrator configure to BEST prevent unauthorized access?
A user is having difficulty with video conferencing and is looking for assistance. Which of the following would BEST improve performance?
A network technician is configuring a new firewall for a company with the necessary access requirements to be allowed through the firewall. Which of the following would normally be applied as the LAST rule in the firewall?
A network technician needs to correlate security events to analyze a suspected intrusion. Which of the following should the technician use?
An ARP request is broadcasted and sends the following request.
''Who is 192.168.1.200? Tell 192.168.1.55''
At which of the following layers of the OSI model does this request operate?
A firewall administrator is implementing a rule that directs HTTP traffic to an internal server listening on a non-standard socket Which of the following types of rules is the administrator implementing?
A network administrator wants to analyze attacks directed toward the company's network. Which of the following must the network administrator implement to assist in this goal?
A lab environment hosts Internet-facing web servers and other experimental machines, which technicians use for various tasks A technician installs software on one of the web servers to allow communication to the company's file server, but it is unable to connect to it Other machines in the building are able to retrieve files from the file server. Which of the following is the MOST likely reason the web server cannot retrieve the files, and what should be done to resolve the problem?
A network administrator wants to improve the security of the management console on the company's switches and ensure configuration changes made can be correlated to the administrator who conformed them Which of the following should the network administrator implement?
A business is using the local cable company to provide Internet access. Which of the following types of cabling will the cable company MOST likely use from the demarcation point back to the central office?
Which of the following uses the destination IP address to forward packets?
A technician wants to install a WAP in the center of a room that provides service in a radius surrounding a radio. Which of the following antenna types should the AP utilize?
Which of the following technologies allows traffic to be sent through two different ISPs to increase performance?
Which of the following services can provide data storage, hardware options, and scalability to a third-party company that cannot afford new devices?
A user reports a weak signal when walking 20ft (61 m) away from the WAP in one direction, but a strong signal when walking 20ft in the opposite direction The technician has reviewed the configuration and confirmed the channel type is correct There is no jitter or latency on the connection Which of the following would be the MOST likely cause of the issue?
A technician is troubleshooting a workstation's network connectivity and wants to confirm which switchport corresponds to the wall jack the PC is using Which of the following concepts would BEST help the technician?
A network technician was troubleshooting an issue for a user who was being directed to cloned websites that were stealing credentials. The URLs were correct for the websites but an incorrect IP address was revealed when the technician used ping on the user's PC After checking the is setting, the technician found the DNS server address was incorrect Which of the following describes the issue?
A network requirement calls for segmenting departments into different networks. The campus network is set up with users of each department in multiple buildings. Which of the following should be configured to keep the design simple and efficient?
A network technician has multimode fiber optic cable available in an existing IDF. Which of the following Ethernet standards should the technician use to connect the network switch to the existing fiber?
Which of the following protocols will a security appliance that is correlating network events from multiple devices MOST likely rely on to receive event messages?
An organization wants to implement a method of centrally managing logins to network services. Which of the following protocols should the organization use to allow for authentication, authorization and auditing?
A client moving into a new office wants the IP network set up to accommodate 412 network-connected devices that are all on the same subnet. The subnet needs to be as small as possible. Which of the following subnet masks should be used to achieve the required result?
A network technician is observing the behavior of an unmanaged switch when a new device is added to the network and transmits data. Which of the following BEST describes how the switch processes this information?
A network administrator is setting up several loT devices on a new VLAN and wants to accomplish the following
1. Reduce manual configuration on each system
2. Assign a specific IP address to each system
3. Allow devices to move to different switchports on the same VLAN
Which of the following should the network administrator do to accomplish these requirements?
A network administrator is required to ensure that auditors have read-only access to the system logs, while systems administrators have read and write access to the system logs, and operators have no access to the system logs. The network administrator has configured security groups for each of these functional categories. Which of the following security capabilities will allow the network administrator to maintain these permissions with the LEAST administrative effort?
Which of the following protocol types describes secure communication on port 443?
During the security audit of a financial firm the Chief Executive Officer (CEO) questions why there are three employees who perform very distinct functions on the server. There is an administrator for creating users another for assigning the users lo groups and a third who is the only administrator to perform file rights assignment Which of the following mitigation techniques is being applied'
A user recently made changes to a PC that caused it to be unable to access websites by both FQDN and IP Local resources, such as the file server remain accessible. Which of the following settings did the user MOST likely misconfigure?
The following instructions were published about the proper network configuration for a videoconferencing device:
"Configure a valid static RFC1918 address for your network. Check the option to use a connection over NAT."
Which of the following is a valid IP address configuration for the device?
A network technician is installing an analog desk phone for a new receptionist After running a new phone line, the technician now needs to cnmp on a new connector. Which of the following connectors would MOST likely be used in this case?
Which of the following OSI model layers is where conversations between applications are established, coordinated, and terminated?
A company wants to implement a large number of WAPs throughout its building and allow users to be able to move around the building without dropping their connections Which of the following pieces of equipment would be able to handle this requirement?
A small, family-run business uses a single SOHO router to provide Internet and WiFi to its employees At the start of a new week, employees come in and find their usual WiFi network is no longer available, and there is a new wireless network to which they cannot connect. Given that information, which of the following should have been done to avoid this situation'
A network technician is investigating an IP phone that does not register in the VoIP system Although it received an IP address, it did not receive the necessary DHCP options The information that is needed for the registration is distributes by the OHCP scope All other IP phones are working properly. Which of the following does the technician need to verify?
Which of the following is MOST appropriate for enforcing bandwidth limits when the performance of an application is not affected by the use of buffering but is heavily impacted by packet drops?
A network administrator is preparing answers for an annual risk assessment that is required for compliance purposes. Which of the following would be an example of an internal threat?
Which of the following attacks can be effectively protected against by using techniques to check if a connection was made by a human user? (Select two).
A device is connected to a managed Layer 3 network switch. The MAC address of the device is known, but the static IP address assigned to the device is not. Which of the following features of a Layer 3 network switch should be used to determine the IPv4 address of the device?
A network administrator needs to monitor traffic on a specific port on a switch. Which of the following should the administrator configure to accomplish the task?
Which of the following should be implemented to allow remote users to access network resources while only redirecting necessary traffic?
A company wants to mitigate unauthorized physical connectivity after implementing a hybrid work schedule. Which of the following will the company most likely configure?
A security engineer wants to provide a secure, dedicated, alternate access method into an IT network infrastructure to administer connected devices and IT assets. Which of the following is the engineer most likely to implement?
A network administrator received reports that a 40Gb connection is saturated. The only server the administrator can use for data collection in that location has a 10Gb connection to the network. Which of the following is the best method to use on the server to determine the source of the saturation?
A company ranis out a largo event space and includes wireless internet access for each tenant. Tenants reserve a two-hour window from the company each week, which includes a tenant-specific SSID However, all users share the company's network hardware.
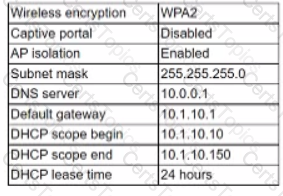
The network support team is receiving complaints from tenants that some users are unable to connect to the wireless network Upon investigation, the support teams discovers a pattern indicating that after a tenant with a particularly large attendance ends its sessions, tenants throughout the day are unable to connect.
The following settings are common lo all network configurations:
Which of the following actions would MOST likely reduce this Issue? (Select TWO).
A local company is planning to upgrade is current wireless network solution to achieve better performance and improve employees' experience. The solution will require a 5GHz radio band to support all current company devices. Which of the following should be considered as an option for the upgrade?
A customer is hosting an internal database server. None of the users are able to connect to the server, even though it appears to be working properly. Which of the following is the best way to verify traffic to and from the server?
A company has multiple offices around the world. The computer rooms in some office locations are too warm Dedicated sensors are in each room, but the process of checking each sensor takes a long time. Which of the following options can the company put In place to automate temperature readings with internal resources?
After the A record of a public website was updated, some visitors were unable to access the website. Which of the following should be adjusted to address the issue?
An IT director is setting up new disaster and HA policies for a company. Limited downtime is critical to operations. To meet corporate requirements, the director set up two different datacenters across the country that will stay current on data and applications. In the event of an outage, the company can immediately switch from one datacenter to another. Which of the following does this BEST describe?
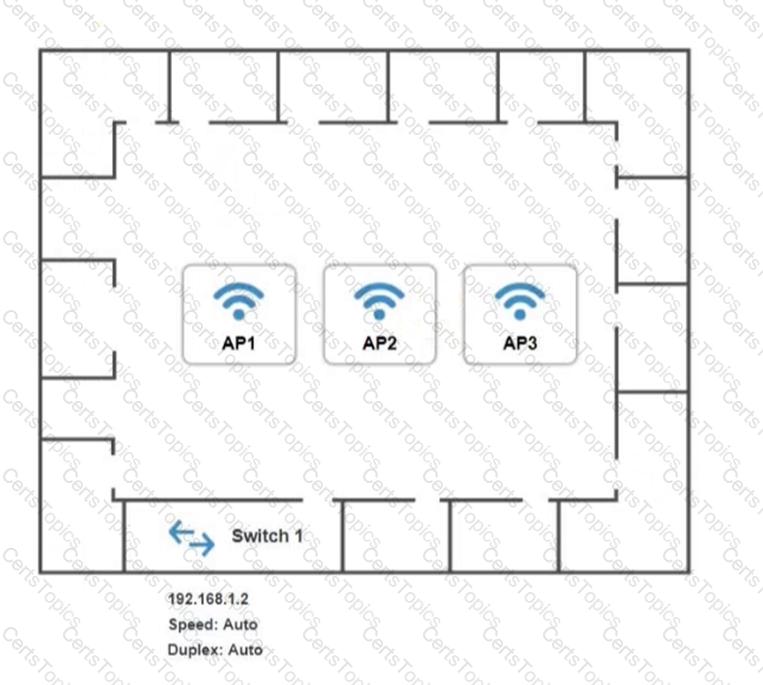
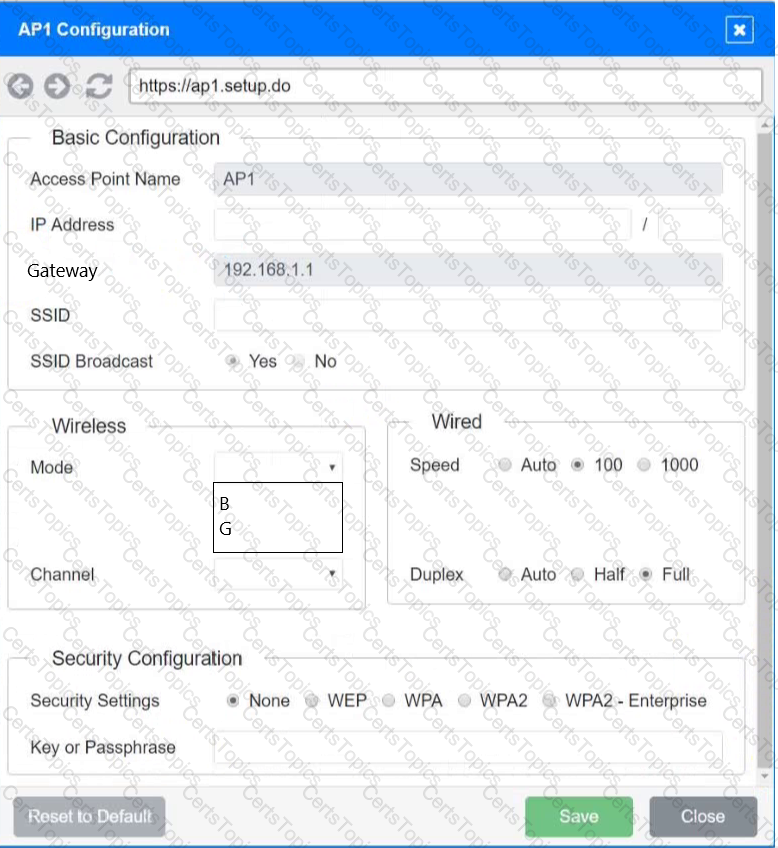
SIMULATION
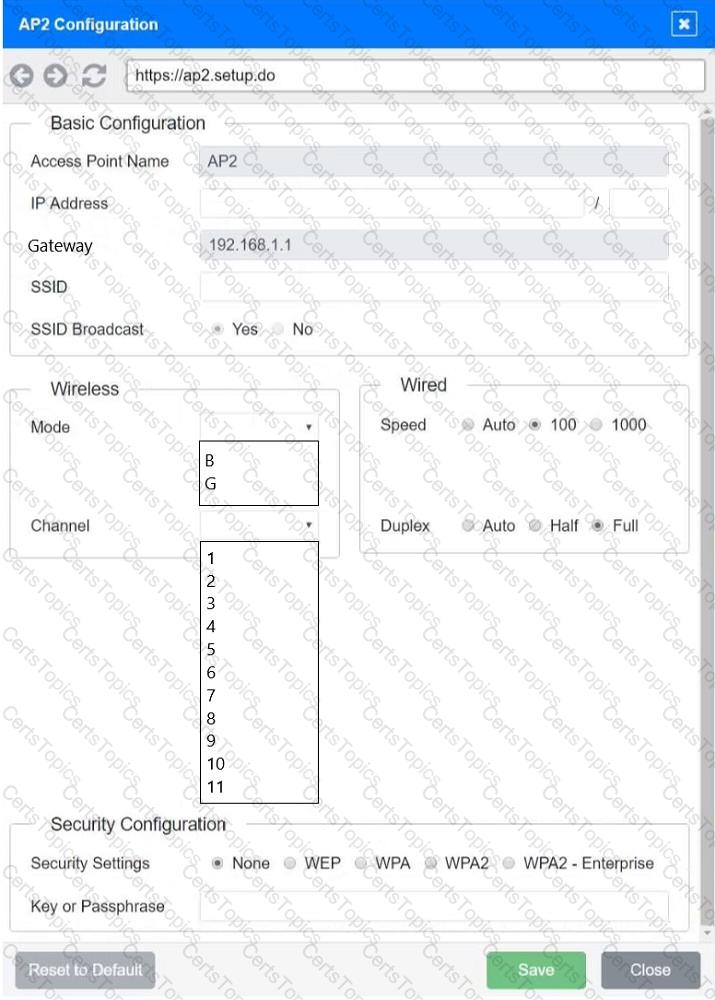
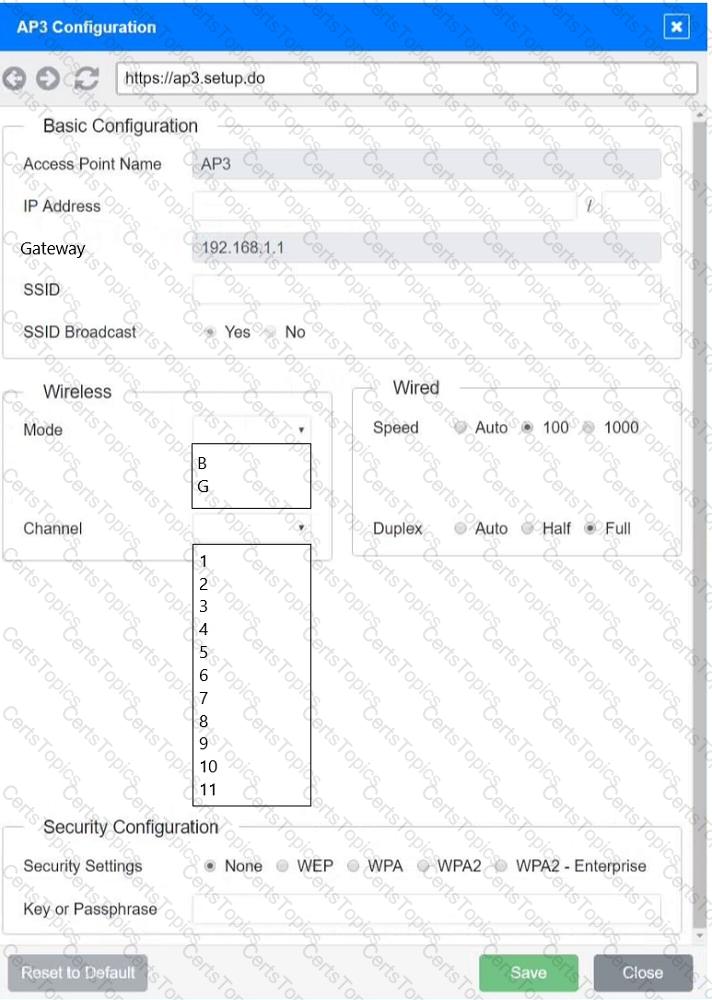
You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters:
The SSIDs need to be configured as CorpNet with a key of S3cr3t!
The wireless signals should not interfere with each other
The subnet the Access Points and switch are on should only support 30 devices maximum
The Access Points should be configured to only support TKIP clients at a maximum speed
INSTRUCTONS
Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network administrator discovers that users in an adjacent building are connecting to the company’s guest wireless network to download inappropriate material. Which of the following can the administrator do to MOST easily mitigate this issue?
A technician wants to deploy a new wireless network that comprises 30 WAPs installed throughout a three-story office building. All the APs will broadcast the same SSID for client access. Which of the following BEST describes this deployment?
A technician is configuring a network switch to be used in a publicly accessible location. Which of the following should the technician configure on the switch to prevent unintended connections?
Which of the following routing protocols is used to exchange route information between public autonomous systems?
Which of the following is the physical topology for an Ethernet LAN?
Which of the following is used to prioritize Internet usage per application and per user on the network?
Which of the following factors should be considered when evaluating a firewall to protect a datacenter’s east-west traffic?
Wireless users are reporting intermittent internet connectivity. Connectivity is restored when the users disconnect and reconnect, utilizing the web authentication process each time. The network administrator can see the devices connected to the APs at all times. Which of the following steps will MOST likely determine the cause of the issue?
A technician is troubleshooting a wireless connectivity issue in a small office located in a high-rise building. Several APs are mounted in this office. The users report that the network connections frequently disconnect and reconnect throughout the day. Which of the following is the MOST likely cause of this issue?
Which of the following service models would MOST likely be used to replace on-premises servers with a cloud solution?
A website administrator is concerned the company’s static website could be defaced by hacktivists or used as a pivot point to attack internal systems. Which of the following should a network security administrator recommend to assist with detecting these activities?
The following configuration is applied to a DHCP server connected to a VPN concentrator:

There are 300 non-concurrent sales representatives who log in for one hour a day to upload reports, and 252 of these representatives are able to connect to the VPN without any Issues. The remaining sales representatives cannot connect to the VPN over the course of the day. Which of the following can be done to resolve the issue without utilizing additional resources?
Which of the following ports is commonly used by VoIP phones?
A network engineer performs the following tasks to increase server bandwidth:
Connects two network cables from the server to a switch stack
Configure LACP on the switchports
Verifies the correct configurations on the switch interfaces
Which of the following needs to be configured on the server?
A network administrator needs to query the NSs for a remote application. Which of the following commands would BEST help the administrator accomplish this task?
Within the realm of network security, Zero Trust:
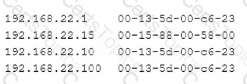
Given the following information:
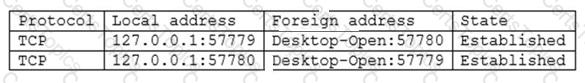
Which of the following command-line tools would generate this output?
An engineer is configuring redundant network links between switches. Which of the following should the engineer enable to prevent network stability issues?
A technician is connecting multiple switches to create a large network for a new office. The switches are unmanaged Layer 2 switches with multiple connections between each pair. The network is experiencing an extreme amount of latency. Which of the following is MOST likely occurring?
At which of the following OSI model layers would a technician find an IP header?
Several WIFI users are reporting the inability to connect to the network. WLAN users on the guest network are able to access all network resources without any performance issues. The following table summarizes the findings after a site survey of the area in question:
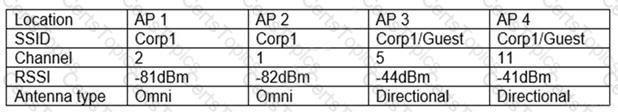
Which of the following should a wireless technician do NEXT to troubleshoot this issue?
Which of the following would be BEST to use to detect a MAC spoofing attack?
A technician is writing documentation regarding a company’s server farm. The technician needs to confirm the server name for all Linux servers. Which of the following commands should the technician run?
Which of the following can be used to centrally manage credentials for various types of administrative privileges on configured network devices?
A workstation is configured with the following network details:

Software on the workstation needs to send a query to the local subnet broadcast address. To which of the following addresses should the software be configured to send the query?
A new cabling certification is being requested every time a network technician rebuilds one end of a Cat 6 (vendor-certified) cable to create a crossover connection that is used to connect switches. Which of the following would address this issue by allowing the use of the original cable?
The network administrator is informed that a user’s email password is frequently hacked by brute-force programs. Which of the following policies should the network administrator implements to BEST mitigate this issue? (Choose two.)
A store owner would like to have secure wireless access available for both business equipment and patron use. Which of the following features should be configured to allow different wireless access through the same equipment?
Which of the following connector types would have the MOST flexibility?
A network administrator is configuring a load balancer for two systems. Which of the following must the administrator configure to ensure connectivity during a failover?
A company built a new building at its headquarters location. The new building is connected to the company’s LAN via fiber-optic cable. Multiple users in the new building are unable to access the company’s intranet site via their web browser, but they are able to access internet sites. Which of the following describes how the network administrator can resolve this issue?
A network engineer configured new firewalls with the correct configuration to be deployed to each remote branch. Unneeded services were disabled, and all firewall rules were applied successfully. Which of the following should the network engineer perform NEXT to ensure all the firewalls are hardened successfully?
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic
Building A
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide devices to support 5 additional different office users
Add an additional mobile user
Replace the Telnet server with a more secure solution
Screened subnet
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
Provide a server to handle external 80/443 traffic
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag & Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following technologies provides a failover mechanism for the default gateway?
A systems administrator needs to improve WiFi performance in a densely populated office tower and use the latest standard. There is a mix of devices that use 2.4 GHz and 5 GHz. Which of the following should the systems administrator select to meet this requirement?
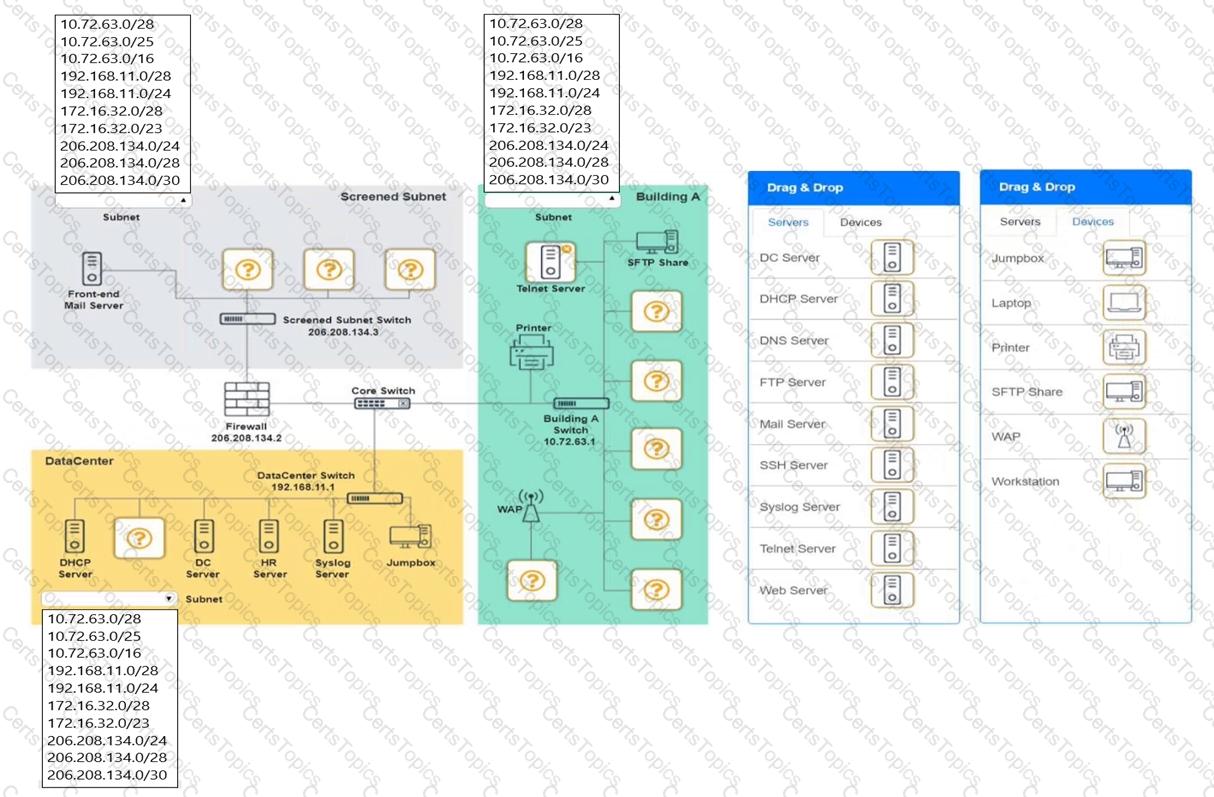
A branch of a company recently switched to a new ISP. The network engineer was given a new IP range to assign. The ISP assigned 196.26.4.0/26, and the branch gateway router now has the following configurations on the interface that peers to the ISP:
The network engineer observes that all users have lost Internet connectivity. Which of the following describes the issue?
Which of the following types of devices can provide content filtering and threat protection, and manage multiple IPSec site-to-site connections?
Which of the following is the LARGEST MTU for a standard Ethernet frame?
Which of the following BEST describes a network appliance that warns of unapproved devices that are accessing the network?
A user tries to ping 192.168.1.100 from the command prompt on the 192.168.2.101 network but gets the following response: U.U.U.U. Which of the following needs to be configured for these networks to reach each other?
Which of the following systems would MOST likely be found in a screened subnet?
A network technician is reviewing the interface counters on a router interface. The technician is attempting to confirm a cable issue. Given the following information:
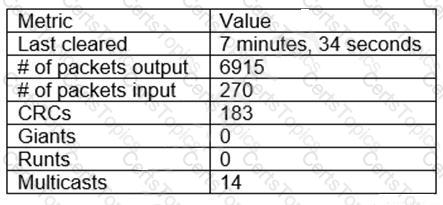
Which of the following metrics confirms there is a cabling issue?
A technician needs to configure a Linux computer for network monitoring. The technician has the following information:
Linux computer details:

Switch mirror port details:

After connecting the Linux computer to the mirror port on the switch, which of the following commands should the technician run on the Linux computer?
Client devices cannot enter a network, and the network administrator determines the DHCP scope is exhausted. The administrator wants to avoid creating a new DHCP pool. Which of the following can the administrator perform to resolve the issue?
A network administrator is installing a wireless network at a client’s office. Which of the following IEEE 802.11 standards would be BEST to use for multiple simultaneous client access?
A technician is installing a high-density wireless network and wants to use an available frequency that supports the maximum number of channels to reduce interference. Which of the following standard 802.11 frequency ranges should the technician look for while reviewing WAP specifications?
A network engineer is investigating reports of poor network performance. Upon reviewing a device configuration, the engineer finds that duplex settings are mismatched on both ends. Which of the following would be the MOST likely result of this finding?
Which of the following is used to track and document various types of known vulnerabilities?
Which of the following provides redundancy on a file server to ensure the server is still connected to a LAN even in the event of a port failure on a switch?
Which of the following would MOST likely be used to review previous upgrades to a system?
Which of the following TCP ports is used by the Windows OS for file sharing?
Which of the following transceiver types can support up to 40Gbps?
Which of the following is MOST likely to generate significant East-West traffic in a datacenter?
Which of the following devices would be used to manage a corporate WLAN?
A technician is installing a new fiber connection to a network device in a datacenter. The connection from the device to the switch also traverses a patch panel connection. The chain of connections is in the following order:
Device
LC/LC patch cable
Patch panel
Cross-connect fiber cable
Patch panel
LC/LC patch cable
Switch
The connection is not working. The technician has changed both patch cables with known working patch cables. The device had been tested and was working properly before being installed. Which of the following is the MOST likely cause of the issue?
A network is experiencing a number of CRC errors during normal network communication. At which of the following layers of the OSI model will the administrator MOST likely start to troubleshoot?
According to troubleshooting methodology, which of the following should the technician do NEXT after determining the most likely probable cause of an issue?
The management team needs to ensure unnecessary modifications to the corporate network are not permitted and version control is maintained. Which of the following documents would BEST support this?
A network engineer is investigating reports of poor network performance. Upon reviewing a report, the engineer finds that jitter at the office is greater than 10ms on the only WAN connection available. Which of the following would be MOST affected by this statistic?
An engineer notices some late collisions on a half-duplex link. The engineer verifies that the devices on both ends of the connection are configured for half duplex. Which of the following is the MOST likely cause of this issue?
A technician is searching for a device that is connected to the network and has the device’s physical network address. Which of the following should the technician review on the switch to locate the device’s network port?
A network administrator is implementing OSPF on all of a company’s network devices. Which of the following will MOST likely replace all the company’s hubs?
A technician is installing multiple UPS units in a major retail store. The technician is required to keep track of all changes to new and old equipment. Which of the following will allow the technician to record these changes?
A client recently added 100 users who are using VMs. All users have since reported slow or unresponsive desktops. Reports show minimal network congestion, zero packet loss, and acceptable packet delay. Which of the following metrics will MOST accurately show the underlying performance issues? (Choose two.)
A technician is assisting a user who cannot connect to a network resource. The technician first checks for a link light. According to troubleshooting methodology, this is an example of:
Branch users are experiencing issues with videoconferencing. Which of the following will the company MOST likely configure to improve performance for these applications?
A network technician is installing new software on a Windows-based server in a different geographical location. Which of the following would be BEST for the technician to use to perform this task?
A technician is installing a cable modem in a SOHO. Which of the following cable types will the technician MOST likely use to connect a modem to the ISP?
A network device is configured to send critical events to a syslog server; however, the following alerts are not being received:
Severity 5 LINK-UPDOWN: Interface 1/1, changed state to down
Severity 5 LINK-UPDOWN: Interface 1/3, changed state to down
Which of the following describes the reason why the events are not being received?
A fiber link connecting two campus networks is broken. Which of the following tools should an engineer use to detect the exact break point of the fiber link?
An administrator is writing a script to periodically log the IPv6 and MAC addresses of all the devices on a network segment. Which of the following switch features will MOST likely be used to assist with this task?
A technician receives feedback that some users are experiencing high amounts of jitter while using the wireless network. While troubleshooting the network, the technician uses the ping command with the IP address of the default gateway and verifies large variations in latency. The technician thinks the issue may be interference from other networks and non-802.11 devices. Which of the following tools should the technician use to troubleshoot the issue?
An IT organization needs to optimize speeds for global content distribution and wants to reduce latency in high-density user locations. Which of the following technologies BEST meets the organization’s requirements?
A network administrator is designing a new datacenter in a different region that will need to communicate to the old datacenter with a secure connection. Which of the following access methods would provide the BEST security for this new datacenter?
A technician is troubleshooting a network switch that seems to stop responding to requests intermittently whenever the logging level is set for debugging. Which of the following metrics should the technician check to begin troubleshooting the issue?
A technician is deploying a new switch model and would like to add it to the existing network monitoring software. The technician wants to know what metrics can be gathered from a given switch. Which of the following should the technician utilize for the switch?
A network administrator redesigned the positioning of the APs to create adjacent areas of wireless coverage. After project validation, some users still report poor connectivity when their devices maintain an association to a distanced AP. Which of the following should the network administrator check FIRST?
A network technician is manually configuring the network settings for a new device and is told the network block is 192.168.0.0/20. Which of the following subnets should the technician use?
A network administrator walks into a datacenter and notices an unknown person is following closely. The administrator stops and directs the person to the security desk. Which of the following attacks did the network administrator prevent?
Which of the following would need to be configured to ensure a device with a specific MAC address is always assigned the same IP address from DHCP?
A user reports being unable to access network resources after making some changes in the office. Which of the following should a network technician do FIRST?
A company hired a technician to find all the devices connected within a network. Which of the following software tools would BEST assist the technician in completing this task?
A network technician needs to ensure outside users are unable to telnet into any of the servers at the datacenter. Which of the following ports should be blocked when checking firewall configuration?