Employee information is stored in a database. Which of the following BEST describes where all of an
employee’s information is stored?
Which of the following best explains the reason for password expiration?
A technician overhears a systems administrator mention the term “IOPS”. To which of the following operating
system functions would the term BEST apply?
Which of the following wireless communication technologies requires devices to be within 6in (15.24cm) from each other?
A systems administrator wants to return results for a time range within a database. Which of the following
commands should the administrator use?
A software developer develops a software program and writes a document with step-by-step instructions on how to use the software. The developer wants to ensure no other person or company will publish this
document for public use. Which of the following should the developer use to BEST protect the document?
Which of the following data types would be best for storing data representing a phone number?
Which of the following shows how many results are possible when evaluating Boolean data types?
SQL databases use primary and foreign keys to enable which of the following?
A technician has established a plan of action. Which of the following should the technician do next?
A startup company has created a logo. The company wants to ensure no other entity can use the logo for any purpose. Which of the following should the company use to BEST protect the logo? (Select TWO).
Which of the following is most appropriate to list on a social media site about an employer?
Which of the following is an advantage of installing an application to the cloud?
During a meeting, managers spoke of several instances in which confidential information appeared on inappropriate websites. The company also discovered its firewall did not filter out certain traffic to prevent such issues. Which of the following most likely exposed the confidential information?
The broadcast signal from a recently installed wireless access point is not as strong as expected. Which of the following actions would BEST improve the signal strength?
Which of the following would be the most secure password reset process?
A regulation requires new applicants to provide a scan of their retinas in case of any future legal questions regarding who applied for the position. Which of the following concepts is this an example of?
Which of the following would be the easiest component to upgrade on a laptop that is experiencing slow performance?
Which of the following types of encryptions would BEST protect a laptop computer in the event of theft?
A music studio needs to store artist data as text, demos as MP3 files, and sheet music as PDF files in an organized and easily searchable format. Which of the following is best suited to meet this need?
Which of the following BEST describes the practice of providing user credentials when logging onto the
network?
A technician is having trouble connecting multiple users' laptops to the internet wirelessly. The users are on the west side of the building, which is hardwired. Which of the following should the technician do to resolve this issue quickly?
Which of the following would indicate the FASTEST processor speed?
Which of the following BEST describes a kilobyte?
A network technician needs to ensure data on a network drive is fully backed up. Which of the following backups should the technician implement?
Ann, a user, connects to the corporate WiFi and tries to browse the Internet. Ann finds that she can only get to local (intranet) pages. Which of the following actions would MOST likely fix the problem?
A database administrator needs to add a column to an existing table. Which of the following statements should the administrator use?
A user at a company visits a weather website often during the day. The user browses to the site in the afternoon and notices that the temperature listed is from the morning and is not the current temperature. The user closes the page and tries again with the same result. Which of the following is the MOST likely cause?
Which of the following is MOST likely used to represent international text data?
Which of the following language types most likely controls the way a web page looks?
Which of the following is a wireless communication that requires devices to be within 6in of each other to
transfer information?
A technician is concerned that sensitive data transmitted over the Internet can be intercepted and viewed during
a MITM attack. Which of the following should the technician enable to reduce the risk?
When developing a game, a developer creates a boss object that has the ability to jump. Which of the following
programming concepts does jump represent?
A product advertising kiosk at a mall is set up using a thin client without a hard drive and is running a web application managed and updated through an internet connection. Which of the following application delivery methods is most likely being used for the kiosk?
A Chief Executive Officer (CEO) wants to have the ability to log on to all applications upon arrival at the office. The CEO would like to have the ability to provide credentials only once. Which of the following is best for this requirement?
A company wants its employee to use an email client that downloads and removes messages from the email
server. Which of the following protocols must be configured in the email client to facilitate this?
A company has installed an application that only requires a workstation to function. Which of the following
architecture types is this application using?
Which of the following BEST describes a technology that allows multiple users to create and edit reports at the
same time?
A company wants an application to be accessed by concurrent users and store company information securely.
Which of the following would be the BEST option for storing the information?
Joe, a user, finds out his password for a social media site has been compromised. Joe tells a friend that his email and banking accounts are probably also compromised. Which of the following has Joe MOST likely performed?
Which of the following scripting languages is most likely to be used in a Linux command-line environment?
Which of the following filesystems is most commonly found on a computer running macOS?
Which of the following is a logical structure for storing files?
A user browses to a website. Before the page opens, the user receives a message that the site is not secure. Which of the following caused this message?
A user wants to prevent web history logging. Which of the following features will allow the user to achieve this goal?
Which of the following security concerns is a threat to confidentiality?
Which of the following is the best way to prevent malicious code from executing on a laptop based on attack signatures?
A small company has authorized an allowance for employees to purchase their own work computers. The administrator has noticed a sizable increase in network traffic following the arrival of the new computers. Which of the following is the most likely reason?
A UPS provides protection against:
A flatbed scanner that is connected to a laptop is used to convert photographic prints to digital images for reproduction on a color printer. Which of the following is considered the input device for this process?
A technician reading workstation security logs notices that an unidentified device is plugged into a USB port several hours a day but is never plugged in when the technician goes to check the machine. File audits reveal nothing unexpected. Which of the following devices is most likely causing this message?
A user is attempting to print a document to a wireless printer and receives an error stating the operation could not be completed. Which of the following should the user do to correct this issue?
Which of the following is the main purpose for a MAC address to identify?
Which of the following database types would be best in which to place financial data?
Which of the following programming concepts uses properties and attributes?
Which of the following is a reason why complex passwords are required?
Which of the following types of memory can retain its content after a system reboot?
Given the following pseudocode:
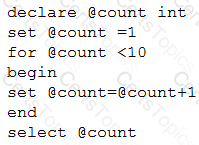
Which of the following is the output of the code?
A user wants to use a laptop outside the house and still remain connected to the Internet. Which of the
following would be the BEST choice to accomplish this task?
On which of the following distinct numbers of digits is the hexadecimal numbering system based?
Which of the following allows wireless devices to communicate to a wired network?
Which of the following data types should a developer use when creating a variable to hold a postal code?
Which of the following software types is best suited for storing large amounts of data in a way that allows for concurrent, indexed access?
An IT manager wants to prevent end users from booting alternative operating systems on workstations. Which of the following security-related best practices would be used to accomplish this?
Which of the following language types would a web developer MOST likely use to create a website?
Which of the following business continuity concepts is the best example of fault tolerance?
Which of the following intellectual property concepts BEST represents a legally protected slogan of a
business?
Which of the following describes something in a database that refers to the unique identifier in the parent
table?
Which of the following describes the concept of a database record?
Which of the following storage types uses platters to store data?
A customer wants to buy a new laptop with a 2.5Gbps processor. Which of the following best describes the device the salesperson should suggest?
An IP address is 32 bits long. If converted to bytes, it would be:
Which of the following is the slowest processing speed?
Which of the following utilities has the ability to remove drivers and scan for hardware changes?
A user has purchased a high-end graphics card that contains a GPU. Which of the following processes is being performed by the GPU on the graphics card?
Which of the following internal computing components is typically tasked with handling complex mathematical calculations required for realistic in-game physics?
A global variable called “age” will be created in a program and incremented through the use of a function.
Which of the following data types should be defined with the age variable?
Which of the following actions is the FINAL step in the standard troubleshooting methodology?
A systems administrator is setting up a new server using RAID technology. If one hard drive in the array fails,
the data is stored on another drive, preventing data loss. Which of the following business continuity concepts
does this explain?
An attacker is using subversive tactics to gain the trust of a target in order to obtain entry to a location or access to confidential information. Which of the following best describes this scenario?
A programmer needs an element that will automatically store customer orders consecutively by order number every time a new order is placed. Which of the following elements should be used?
A technician is called to replace a display for a workstation. Which of the following would MOST likely be used to connect the display to the workstation?
An application is hosted on a local network. Which of the following descriptions is correct?
Which of the following operating systems is best used in creating and managing virtual machines?
A programmer needs to specify how to store a test score entered using a web form. Which of the following would be best to use?
Which of the following is an example of utilizing a personalized code for continuous personal access to a software product?
A programmer needs to store output in a place that can be accessed as quickly as possible. The data does not need to remain persistent. Which of the following is the BEST option for storing the data?
A database administrator finds that a table is not needed in a relational database. Which of the following
commands is used to completely remove the table and its data?
Which of the following BEST describes the purpose of a vector in programming?
Which of the following is an example of information a company would ask employees to handle in a sensitive manner?
A systems administrator wants to run a script at a certain time every day. Which of the following is the BEST
way to achieve this?
Which of the following is most likely to disclose the data collection practices of an application?
Which of the following can a company use to protect its logo?
A user is trying to set up a new wireless access point. Which of the following should the user do first?
An online retailer experienced an outage. An investigation revealed that the server received more requests than it could handle, and customers could not log in as a result. Which of the following best describes this scenario?
Which of the following is an advantage of using locally saved files?
After creating a database, which of the following would a developer most likely use to put data in the database?
Which of the following connection types provides the fastest internet speed?
Which of the following would most likely be used to verify a user is following an AUP?
In which of the following situations should there be come expectation of privacy?
Which of the following operating systems is most likely to be used to provide the GUI for a workplace employee?
Which of the following is secure?
Which of the following would work BEST stored as a flat file rather than stored in a database?