A cloud administrator needs to control the connections between a group of web servers and database servers as part of the financial application security review. Which of the following would be the BEST way to achieve this objective?
A company with a worldwide presence wants to improve the user experience for its website. Which of the following can a systems administrator implement to improve download speeds and latency for the end users?
A security audit related to confidentiality controls found the following transactions occurring in the system:
GET &user=277
Which of the following solutions will solve the audit finding?
A company is using an laaS environment. Which of the following licensing models would BEST suit the organization from a financial perspective to implement scaling?
A company is deploying a public cloud solution for an existing application using lift and shift. The requirements for the applications are scalability and external access. Which of the following should the company implement? (Select TWO).
A company has two primary offices, one in the United States and one in Europe. The company uses a public laaS service that has a global data center presence to host its marketing materials. The marketing team, which is primarily based in Europe, has reported latency issues when retrieving these materials. Which of the following is the BEST option to reduce the latency issues?
A piece of software applies licensing fees on a socket-based model. Which of the following is the MOST important consideration when attempting to calculate the licensing costs for this software?
A cloud administrator needs to establish a secure connection between two different locations. Which of the following is the BEST option to implement the secure connection?
A systems administrator wants to restrict access to a set of sensitive files to a specific group of users. Which of the following will achieve the objective?
While investigating network traffic, a cloud administrator discovers the monthly billing has increased substantially. Upon further review, it appears the servers have been compromised, and sensitive files have been exfiltrated. Which of the following can be implemented to maintain data confidentiality?
Audit and system logs are being forwarded to a syslog solution. An administrator observes that two application servers have not generated any logs for a period of three days, while others continue to send logs normally. Which of the following BEST explains what is occurring?
A systems administrator is troubleshooting issues with network slowness. Traffic analysis shows that uplink bandwidth on the core switch is often sustained at 125Mbps due to a
combination of production traffic from other sources. Which of the following would BEST resolve the issue?
A company has two identical environments (X and Y) running its core business application. As part of an upgrade, the X environment is patched/upgraded and tested while the Y environment is still serving the consumer workloads. Upon successful testing of the X environment, all workload is sent to this environment, and the Y environment is then upgraded before both environments start to manage the workloads. Which of the following upgrade methods is being used?
A startup online gaming company is designing the optimal graphical user experience for multiplayer scenarios. However, online players have reported latency issues. Which of the following should the company configure as a remediation?
A company has hired a security firm to perform a vulnerability assessment of its environment. In the first phase, an engineer needs to scan the network services exposed by the hosts. Which of the following will help achieve this with the LEAST privileges?
During a security incident, an laaS compute instance is detected to send traffic to a host related to cryptocurrency mining. The security analyst handling the incident determines the scope of the incident is limited to that particular instance. Which of the following should the security analyst do NEXT?
A cloud engineer has deployed a virtual storage appliance into a public cloud environment. The storage appliance has a NAT to a public IP address. An administrator later notices there are some strange files on the storage appliance and a large spike in network traffic on the machine. Which of the following is the MOST likely cause?
A systems administrator is deploying a new virtualized environment. The setup is a three-server cluster with 12 VMs running on each server. While executing a vertical-scaling test of the vCPU on the VMs, the administrator gets an error. Which of the following issues is MOST likely occurring?
A company is migrating workloads from on premises to the cloud and would like to establish a connection between the entire data center and the cloud environment. Which of the following VPN configurations would accomplish this task?
An administrator needs to back up all the data from each VM daily while also saving space. Which of the following backup types will BEST fit this scenario?
After initial stress testing showed that a platform performed well with the specification of a single 32 vCPU node, which of the following will provide the desired service with the LOWEST cost and downtime?
A cloud administrator has deployed several VM instances that are running the same applications on VDI nodes. Users are reporting that a role instance is looping between STARTED, INITIALIZING, BUSY, and stop. Upon investigation, the cloud administrator can see the status changing every few minutes. Which of the following should be done to resolve the issue?
A storage administrator is reviewing the storage consumption of a SAN appliance that is running a VDI environment. Which of the following features should the administrator implement to BEST reduce the storage consumption of the SAN?
A cloud administrator is troubleshooting a highly available web application running within three containers behind a Layer 7 load balancer with a WAF inspecting all traffic. The application frequently asks the users to log in again even when the session timeout has not been reached. Which of the following should the cloud administrator configure to solve this issue?
An organization recently deployed a private cloud on a cluster of systems that delivers compute, network, and storage resources in a single hardware, managed by an intelligent software. Which of the following BEST describes this type of deployment?
A systems administrator needs to modify the replication factors of an automated application container from 3 to 5. Which of the following file types should the systems administrator modify on the master controller?
A local bank has all of its infrastructure in the cloud. An update was applied to the main database server at 5:00 a.m. on Monday morning, and the database was then corrupted and unusable. It had to be restored from backup. The last backup was taken the night before at 10:00 p.m. The database was then restored successfully, but seven hours' worth of data was lost, which is deemed unacceptable. Which of the following needs to be updated in the DR plan?
A systems administrator needs to deploy a solution to automate new application releases that come from the development team. The administrator is responsible for provisioning resources at the infrastructure layer without modifying any configurations in the application code. Which of the following would BEST accomplish this task?
A technician deployed a VM with NL-SAS storage to host a critical application. Two weeks later, users have begun to report high application latency. Which of the following is the BEST action to correct the latency issue?
A systems administrator is diagnosing performance issues on a web application. The web application sends thousands of extremely complex SQL queries to a database server, which has trouble retrieving the information in time. The administrator checks the database server and notes the following resource utilization:
CPU: 64%
RAM: 97%
Network throughput: 384,100Kbps.
Disk throughput: 382,700Kbps
The administrator also looks at the storage for the database server and notices it is consistently near its OPS limit. Which of the following will BEST resolve these performance issues?
A company is using a method of tests and upgrades in which a small set of end users are exposed to new services before the majority of other users. Which of the following deployment methods is being used?
A DevOps administrator is building a new application slack in a private cloud. This application will store sensitive information and be accessible from the internet. Which of the following would be MOST useful in maintaining confidentiality?
A systems administrator must ensure confidential company information is not leaked to competitors. Which of the following services will BEST accomplish this goal?
A cloud administrator configured a local cloud-resource pool lo offer 64GB of memory, 64 cores, and 640GB of storage. Thirty-two machines with identical resource allocations are started. but one machine is unable to handle requests. Which of the following is the MOST likely cause?
A company is concerned about the security of its data repository that contains customer PII. A systems administrator is asked to deploy a security control that will prevent the exfiltration of such data. Which of the following should the systems administrator implement?
A cloud administrator has deployed a new VM. The VM cannot access the Internet or the VMs on any other subnet. The administrator runs a network command and sees the following output:
The new VM can access another VM at 172.16.31.39. The administrator has verified the IP address is correct. Which of the following is the MOST likely cause of the connectivity issue?
A cloud architect is reviewing four deployment options for a new application that will be hosted by a public cloud provider. The application must meet an SLA that allows for no more than five hours of downtime annually. The cloud architect is reviewing the SLAs for the services each option will use:
Based on the information above, which of the following minimally complies with the SLA requirements?
Users of a public website that is hosted on a cloud platform are receiving a message indicating the connection is not secure when landing on the website. The administrator has found that only a single protocol is opened to the service and accessed through the URL Which of the following would MOST likely resolve the issue?
To save on licensing costs, the on-premises, IaaS-hosted databases need to be migrated to a public DBaaS solution. Which of the following would be the BEST technique?
A systems administrator adds servers to a round-robin, load-balanced pool, and then starts receiving reports of the website being intermittently unavailable. Which of the following is the MOST likely cause of the issue?
A software development manager is looking for a solution that will allow a team of developers to work in isolated environments that can be spun up and torn down quickly.
Which of the following is the MOST appropriate solution?
An administrator is securing a private cloud environment and wants to ensure only approved systems can connect to switches. Which of the following would be MOST useful to accomplish this task?
An administrator recently provisioned a file server in the cloud. Based on financial considerations, the administrator has a limited amount of disk space. Which of the following will help control the amount of space that is being used?
A technician needs to deploy two virtual machines in preparation for the configuration of a financial application next week. Which of the following cloud deployment models should the technician use?
A cloud solutions architect needs to determine the best strategy to deploy an application environment in production, given the following requirements:
No downtime
Instant switch to a new version using traffic control for all users
Which of the following deployment strategies would be the BEST solution?
A systems administrator is working in a globally distributed cloud environment. After a file server VM was moved to another region, all users began reporting slowness when saving files. Which of the following is the FIRST thing the administrator should check while troubleshooting?
Which of the following definitions of serverless computing BEST explains how it is different from using VMs?
An organization suffered a critical failure of its primary datacenter and made the decision to switch to the DR site. After one week of using the DR site, the primary datacenter is now ready to resume operations.
Which of the following is the MOST efficient way to bring the block storage in the primary datacenter up to date with the DR site?
An engineer is responsible for configuring a new firewall solution that will be deployed in a new public cloud environment. All traffic must pass through the firewall. The SLA for the firewall is 99.999%. Which of the following should be deployed?
A systems administrator has finished installing monthly updates to servers in a cloud environment. The administrator notices certain portions of the playbooks are no longer functioning. Executing the playbook commands manually on a server does not work as well. There are no other reports of issues.
Which of the following is the MOST likely cause of this issue?
A system administrator is migrating a bare-metal server to the cloud. Which of the following types of migration should the systems administrator perform to accomplish this task?
A cloud administrator is managing an organization's infrastructure in a public cloud. All servers are currently located in a single virtual network with a single firewall that all traffic must pass through. Per security requirements, production, QA, and development servers should not be able to communicate directly with each other. Which of the following should an administrator perform to comply with the security requirement?
A development team recently completed testing changes to a company's web-based CMS in the sandbox environment. The cloud administrator deployed these CMS application changes to the staging environment as part of the next phase in the release life cycle. The deployment was successful, but after deploying the CMS application, the web page displays an error message stating the application is unavailable. After reviewing the application logs, the administrator sees an error message that the CMS is unable to connect to the database. Which of the following is the BEST action for the cloud administrator to perform to resolve the issue?
A user reports a poor-quality remote VDI session. Which of the following should the help desk technician do FIRST to troubleshoot the issue?
A company has an in-house-developed application. The administrator wants to utilize cloud services for additional peak usage workloads. The application has a very unique stack of dependencies.
Which of the following cloud service subscription types would BEST meet these requirements?
An update is being deployed to a web application, and a systems administrator notices the cloud SQL database has stopped running. The VM is responding to pings, and there were not any configuration changes scheduled for the VM. Which of the following should the administrator check NEXT?
A resource pool in a cloud tenant has 90 GB of memory and 120 cores. The cloud administrator needs to maintain a 30% buffer for resources for optimal performance of the hypervisor. Which of the following would all ow for the maximum number of two-core machines with equal memory?
A technician just received the lessons learned from some recent data that was lost due to an on-premises file-server crash. The action point is to change the backup strategy to minimize manual intervention. Which of the following is the BEST approach for the technician to implement?
A company recently experienced a power outage that lasted 30 minutes. During this time, a whole rack of servers was inaccessible, even though the servers did not lose power.
Which of the following should be investigated FIRST?
After a hardware upgrade on a private cloud system, the systems administrator notices a considerable drop in network performance. Which of the following is MOST likely the cause?
A system administrator has provisioned a new web server. Which of the following, in combination, form the best practice to secure the server's OS? (Choose three.)
A systems administrator is trying to reduce storage consumption. Which of the following file types would benefit the MOST from compression?
A cloud administrator would like to deploy a cloud solution to its provider using automation techniques. Which of the following must be used? (Choose two.)
A disaster situation has occurred, and the entire team needs to be informed about the situation. Which of the following documents will help the administrator find the details of the relevant team members for escalation?
A cloud administrator is building a new VM for machine-learning training. The developer requesting the VM has stated that the machine will need a full GPU dedicated to it.
Which of the following configuration options would BEST meet this requirement?
A cloud administrator wants to have a central repository for all the logs in the company’s private cloud. Which of the following should be implemented to BEST meet this requirement?
A Chief Information Security Officer (CISO) is evaluating the company’s security management program. The CISO needs to locate all the assets with identified deviations and mitigation measures. Which of the following would help the CISO with these requirements?
A cloud administrator is assigned to establish a connection between the on-premises data center and the new CSP infrastructure. The connection between the two locations must be secure at all times and provide service for all users inside the organization. Low latency is also required to improve performance during data transfer operations. Which of the following would BEST meet these requirements?
An organization hosts an ERP database in on-premises infrastructure. A recommendation has been made to migrate the ERP solution to reduce operational overhead in the maintenance of the data center. Which of the following should be considered when migrating this on-premises database to DBaaS?
• Database application version compatibility
• Database IOPS values
• Database storage utilization
• Physical database server CPU cache value
• Physical database server DAS type
• Physical database server network I/O
• Database total user count
• Database total number of tables
• Database total number of storage procedures
• Physical database server memory configuration
• Physical database server CPU frequency
A cloud security analyst needs to ensure the web servers in the public subnet allow only secure communications and must remediate any possible issue. The stateful configuration for the public web servers is as follows:
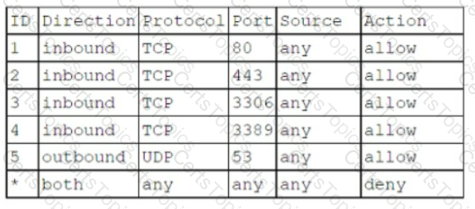
Which Of the following actions Should the analyst take to accomplish the Objective?
A cloud administrator needs to implement a new system within the current CSR The system requires a storage service to allocate a large number of digital files and images. The storage service must keep files for distributed access and serve images directly to the user's browser. Which of the following solutions would best meet these requirements?
A corporation is evaluating an offer from a CSP to take advantage of volume discounts on a shared platform. The finance department is concerned about cost allocation transparency, as the current structure splits projects into dedicated billing accounts. Which of the following can be used to address this concern?
A systems administrator has been notified of possible illegal activities taking place on the network and has been directed to ensure any relevant emails are preserved for court use.
Which of the following is this MOST likely an example of?
A systems administrator wants to be notified every time an application's configuration files are updated. Which of the following should the administrator implement to achieve the objective?
A Cloud administrator needs to reduce storage costs. Which of the following would BEST help the administrator reach that goal?
A cloud engineer is troubleshooting a performance issue for a high-traffic, cloud-based application that provides static content to its geographically distributed users. The engineer needs to:
Improve the performance of an application.
Implement a static content caching mechanism.
Protect against DDoS attacks.
Maintain low cost.
Which of the following strategies would best accomplish this task?
A security analyst is investigating a recurring alert. The alert is reporting an insecure firewall configuration state after every cloud application deployment. The process of identifying the issue, requesting a fix, and waiting for the developers to manually patch the environment is being repeated multiple times. In an effort to identify the root issue, the following logs were collected:
Deploying template app prod. •yaml
Instance DB successfully created
DB keys successfully stored on vault
Instance WebApp successfully created
Access rules successfully applied
Access—keys successfully created
Which of the following options will provide a permanent fix for the issue?
A company's web servers are scheduled for patching and quarterly updates. A cloud administrator must prevent the monitoring systems from logging outage alerts and negatively impacting company SLA targets. Which of the following is the best action for the administrator to take?
A cloud administrator needs to deploy a security virtual appliance in a private cloud environment, but this appliance will not be part of the standard catalog of items for other users to request. Which of the following is the BEST way to accomplish this task?
Developers report that the time needed in the current build process to deploy a VM, install an OS, and configure an application is too long. The developers want a more optimized solution that allows portability of the application across environments and can be deployed more quickly and efficiently. Which of the following should be used to optimize the environment?
A company is using a hybrid cloud environment. The private cloud is hosting the business applications, and the cloud services are being used to replicate for availability purposes.
The cloud services are also being used to accommodate the additional resource requirements to provide continued services. Which of the following scalability models is the company utilizing?
A cloud security engineer needs to design an IDS/IPS solution for a web application in a single virtual private network. The engineer is considering implementing IPS protection for traffic coming from the internet. Which of the following should the engineer consider to meet this requirement?
Which of the following lists includes examples of predeveloped AI/ML solutions?
An organization is deploying development, quality assurance, and production environments with equal numbers of IP addresses to the cloud. The IP address range provided is 10.168.0.0/24, and it needs to be terminated on a firewall. Which of the following IP subnets and firewall IPS should be used for one of the environments?
A company plans to publish a new application and must conform with security standards. Which of the following types of testing are most important for the systems administrator to run to assure the security and compliance of the application before publishing? (Select two).
One of the web applications in a public subnet is vulnerable to a newly discovered zero-day vulnerability. Which of the following actions can a security engineer perform to reduce the risk of exploitation and application downtime?
A systems administrator automates a series of tasks in a playbook and receives the following error during testing:
"Unable to find any of pip2, pip to use. pip needs to be installed."
The administrator verifies that pip is installed correctly. Which of the following actions will most likely resolve this issue?
An IT administrator is implementing security controls on an OS. Which of the following will provide the best protection against a brute-force attack? (Select two).
A systems administrator is configuring a cloud solution for a vulnerability assessment to test the company's resources that are hosted in a public cloud. The solution must test the company's resources from an external user's perspective. Which of the following should the systems administrator configure?
A cloud engineer is configuring automated backups for a database. The engineer wants to ensure that backups can be restored quickly and consistently to meet the SLA. Which of the following backup methods would be the most appropriate?
A cloud architect is receiving complaints from VDI users overseas about slowness, even though the remote office has Gigabit internet. Which of the following will most likely solve the issue?
A cloud administrator must ensure all servers are in compliance with the company's security policy Which of the following should the administrator check FIRST?
A cloud engineer is troubleshooting RSA key-based authentication from a local computer to a cloud-based server, which is running SSH service on a default port. The following file
permissions are set on the authorized keys file:
-rw-rw-rw-1 ubuntu ubuntu 391 Mar S 01:36 authorized _ keys
Which Of the following security practices are the required actions the engineer Should take to gain access to the server? (Select TWO).
A cloud administrator is looking at the company's cloud services bill for the previous month. The administrator notices on the billing dashboard that certain resources are not being billed to any particular department. Which of the following actions will help correct this billing issue?
A DevOps engineer needs to make application deployments more efficient. The current process to deploy and scale the application is very manual, with hours spent configuring servers from scratch each time. The application has many platform-based dependencies but is highly portable and can run on multiple platforms. Which of the following is most likely to reduce deployment time and improve efficiencies?
A business is looking at extending the platform for an internally developed application using microservices from various cloud vendors. The cloud architect is responsible for reviewing the proposed solution design, which covers critical requirements for the business to fulfill its requirements. Which of the following is the most likely requirement the cloud architect needs to fulfill?
A systems administrator is diagnosing performance issues on a web application. The web application sends thousands of extremely complex SQL queries to a database server, which has trouble retrieving the information in time. The administrator checks the database server and notes the following resource utilization:
CPU: 64%
RAM: 97%
Network throughput: 384/1000 Kbps
Disk throughput: 382,700 Kbps
The administrator also notices that the storage for the database server is consistently near its IOPS limit. Which of the following will best resolve these performance issues?
A systems administrator needs to implement a way for users to verify software integrity. Which of the following tools would BEST meet the administrator's needs?
A DevOps team needs to provide a solution that offers isolation, portability, and scalability Which of the following would BEST meet these requirements?
A cloud administrator is having difficulty correlating logs for multiple servers. Upon inspection, the administrator finds that the time-zone settings are mismatched throughout the deployment. Which of the following solutions can help maintain time synchronization between all the resources?
A cloud engineer receives an alert that a newly provisioned server is running a non-supported Linux version. The automation scripts are performing as expected on the server. Which of the following should the engineer check first?
A company is concerned it will run out of VLANs on its private cloud platform in the next couple months, and the product currently offered to customers requires the company to allocate three dedicated, segmented tiers. Which of the following can the company implement to continue adding new customers and to maintain the required level of isolation from other tenants?
A systems administrator is creating a playbook to run tasks against a server on a set schedule.
Which of the following authentication techniques should the systems administrator use within the playbook?
In an existing IaaS instance, it is required to deploy a single application that has different versions.
Which of the following should be recommended to meet this requirement?
A company developed a product using a cloud provider’s PaaS platform and many of the platform-based components within the application environment.
Which of the following would the company MOST likely be concerned about when utilizing a multicloud strategy or migrating to another cloud provider?
A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance has been slow since the images were upgraded from Windows 7 to Windows 10.
This VDI environment is used to run simple tasks, such as Microsoft Office. The administrator investigates the virtual machines and finds the following settings:
4 vCPU
16GB RAM
10Gb networking
256MB frame buffer
Which of the following MOST likely needs to be upgraded?
A cloud administrator has built a new private cloud environment and needs to monitor all computer, storage, and network components of the environment.
Which of the following protocols would be MOST useful for this task?
A systems administrator is reviewing two CPU models for a cloud deployment. Both CPUs have the same number of cores/threads and run at the same clock speed.
Which of the following will BEST identify the CPU with more computational power?
Company A has acquired Company B and is in the process of integrating their cloud resources. Company B needs access to Company A’s cloud resources while retaining its IAM solution.
Which of the following should be implemented?
A web server has been deployed in a public IaaS provider and has been assigned the public IP address of 72.135.10.100. Users are now reporting that when they browse to the website, they receive a message indicating the service is unavailable. The cloud administrator logs into the server, runs a netstat command,
and notices the following relevant output:

Which of the following actions should the cloud administrator take to resolve the issue?
A systems administrator recently upgraded the processors in a web application host. Upon the next login, the administrator sees a new alert regarding the license being out of compliance.
Which of the following licensing models is the application MOST likely using?
An organization is implementing a new requirement to facilitate users with faster downloads of corporate application content. At the same time, the organization is also expanding cloud regions.
Which of the following would be suitable to optimize the network for this requirement?
Which of the following strategies will mitigate the risk of a zero-day vulnerability MOST efficiently?
A storage array that is used exclusively for datastores is being decommissioned, and a new array has been installed. Now the private cloud administrator needs to migrate the data.
Which of the following migration methods would be the BEST to use?
A global web-hosting company is concerned about the availability of its platform during an upcoming event. Web traffic is forecasted to increase substantially during the next week. The site contains mainly static content.
Which of the following solutions will assist with the increased workload?
Which of the following is relevant to capacity planning in a SaaS environment?
A systems administrator notices that a piece of networking equipment is about to reach its end of support.
Which of the following actions should the administrator recommend?
A systems administrator disabled TLS 1.0 and 1.1, as well as RC4, 3DES, and AES-128 ciphers for TLS 1.2, on a web server. A client now reports being unable to access the web server, but the administrator verifies that the server is online, the web service is running, and other users can reach the server as well.
Which of the following should the administrator recommend the user do FIRST?
An organization is hosting a cloud-based web server infrastructure that provides web-hosting solutions. Sudden continuous bursts of traffic have caused the web servers to saturate CPU and network utilizations.
Which of the following should be implemented to prevent such disruptive traffic from reaching the web servers?
An IaaS provider has numerous devices and services that are commissioned and decommissioned automatically on an ongoing basis. The cloud administrator needs to implement a solution that will help reduce administrative overhead.
Which of the following will accomplish this task?
A technician is working with an American company that is using cloud services to provide video-based training for its customers. Recently, due to a surge in demand, customers in Europe are experiencing latency.
Which of the following services should the technician deploy to eliminate the latency issue?
A systems administrator has migrated an internal application to a public cloud. The new web server is running under a TLS connection and has the same TLS certificate as the internal application that is deployed. However, the IT department reports that only internal users who are using new versions of the OSs are able to load the application home page.
Which of the following is the MOST likely cause of the issue?
A systems administrator needs to convert ten physical servers to virtual.
Which of the following would be the MOST efficient conversion method for the administrator to use?
A cloud administrator is reviewing the authentication and authorization mechanism implemented within the cloud environment. Upon review, the administrator discovers the sales group is part of the finance group, and the sales team members can access the financial application. Single sign-on is also implemented, which makes access much easier.
Which of the following access control rules should be changed?
A systems administrator is configuring a storage array.
Which of the following should the administrator configure to set up mirroring on this array?
A systems administrator is deploying a GPU-accelerated VDI solution. Upon requests from several users, the administrator installs an older version of the OS on their virtual workstations. The majority of the VMs run the latest LTS version of the OS.
Which of the following types of drivers will MOST likely ensure compatibility will all virtual workstations?
A DevOps administrator is automating an existing software development workflow. The administrator wants to ensure that prior to any new code going into production, tests confirm the new code does not negatively impact existing automation activities.
Which of the following testing techniques would be BEST to use?
A cloud administrator is reviewing a new application implementation document. The administrator needs to make sure all the known bugs and fixes are applied, and unwanted ports and services are disabled.
Which of the following techniques would BEST help the administrator assess these business requirements?
An organization’s web server farm, which is hosted in the cloud with DNS load balancing, is experiencing a spike in network traffic. This has caused an outage of the organization’s web server infrastructure.
Which of the following should be implemented to prevent this in the future as a mitigation method?
An organization has two businesses that are developing different software products. They are using a single cloud provider with multiple IaaS instances. The organization identifies that the tracking of costs for each
business are inaccurate.
Which of the following is the BEST method for resolving this issue?
A systems administrator is provisioning VMs in a cloud environment and has been told to select an OS build with the furthest end-of-life date.
Which of the following OS builds would be BEST for the systems administrator to use?
A media company has made the decision to migrate a physical, internal file server to the cloud and use a web- based interface to access and manage the files. The users must be able to use their current corporate logins.
Which of the following is the MOST efficient way to achieve this goal?
A systems administrator is informed that a database server containing PHI and PII is unencrypted. The environment does not support VM encryption, nor does it have a key management system. The server needs to be able to be rebooted for patching without manual intervention.
Which of the following will BEST resolve this issue?
A cloud administrator needs to implement a mechanism to monitor the expense of the company’s cloud resources.
Which of the following is the BEST option to execute this task with minimal effort?
An IaaS application has a two-hour RTO and a four-hour RPO. The application takes one hour to back up its data or restore from a local backup file. A systems administrator is tasked with configuring the backup policy.
Which of the following should the administrator configure to achieve the application requirements with the LEAST cost?