When trying to subscribe to an MQTT broker on the internet, the MQTT client is on a private subnet and must be NATed to reach the public broker.
What is the expected outcome when this configuration is in place?
What is a major difference of MQTT in terms of design compared to AMQP?
An IoT engineer is responsible for security at an organization. Humans and machines need to be allowed to access services like database or compute on AWS. The engineer decides to implement dynamic secrets.
Which method helps to get this implementation accurate from a security point of view?
Mosquitto was installed correctly on the Cisco IR829 router as a Cisco IOx application. When the sensor is connected to the broker on the Cisco IR829 router with the default port, the connection is refused (Error Code 5).
Which action should be done to resolve the issue?
Which two security approaches help build a strong authentication scheme? (Choose two.)
Refer to the exhibit.
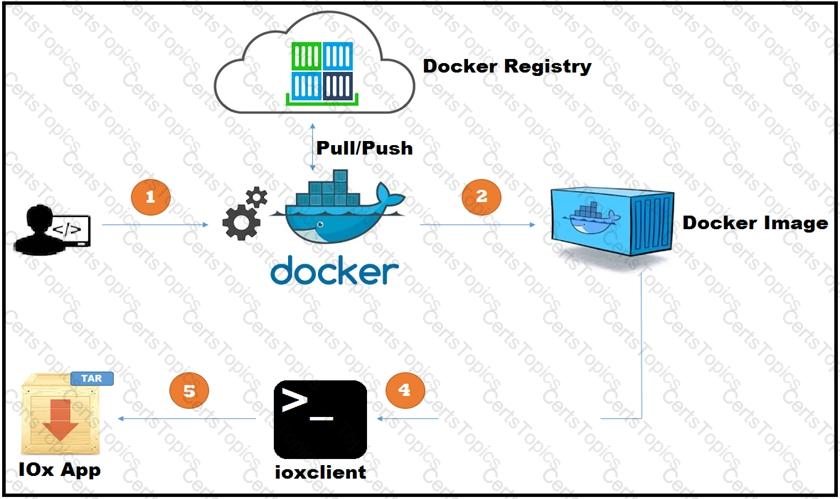
A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
Which data visualization technique should be used to represent an important single metric on a dashboard?
Which element ensures that PKI is used to establish the identity of IoT devices?
Which statement explains the correct position of a PLC within the CPwE architecture?