Which of the following terms below BEST describes the measure of confidence that the security features, practices, procedures, and architecture of an information system accurately mediates and enforces security policy?
An organization’s system engineer arranged a meeting with the system owner and a few major stakeholders to finalize the feasibility analysis for a new application.
Which of the following topics will MOST likely be on the agenda?
A security engineer has determined the need to implement preventative controls into their Wireless Local Area Network (WLAN) for added protection. Which preventative control provides the MOST security?
An organization wants to implement Zero Trust (ZT). The Information Technology (IT) department is already using Multi-Factor Authentication (MFA) and Identity and Access Management (IAM). Which of the following would be the BEST solution for the organization to implement in order to have a ZT network?
While conducting an information asset audit, it was determined that several devices were running unpatched Operating Systems (0S). Further review Indicated the OS was no longer supported by the vendor. Which of the following BEST indicates the appropriate asset lifecycle stage of the devices?
Which of the following tools shows process changes and random variation over time?
To gain entry into a building, individuals are required to use a palm scan. This is an example of which type of control?
One advantage of adopting a supply network perspective Is that it:
What is the MAIN reason security is considered as part of the system design phase instead of deferring to later phases?
Which software development methodology is an iterative customer-value-centric approach which helps teams deliver value to their customers faster and with fewer problems?
A product manager wishes to store sensitive development data using a cloud storage vendor while maintaining exclusive control over passwords and encryption credentials. What is the BEST method for meeting these requirements?
A newer automotive supplier has not fully developed its information technology (IT) systems. The supplier has Just received a contract from a large automotive manufacturer which requires the supplier to use electronic data interchange (EDI) transactions for receiving orders, sending advance ship notices (ASNs), and receiving invoice payments. What strategy can the supplier adopt to immediately meet the EDI requirements?
Which of the common vulnerabilities below can be mitigated by using indexes rather than actual portions of file names?
Management should support investments in new process technologies that:
A vendor has been awarded a contract to supply key business software. The vendor has declined all requests to have its security controls audited by customers. The organization insists the product must go live within 30 days. However, the security team is reluctant to allow the project to go live. What is the organization's BEST next step?
In the sales and operations planning (S&OP) process, the demand management function provides:
Reducing distribution network inventory days of supply will have which of the following Impacts?
The cost accountant has discovered a consistent overage in actual run time for one operation. This information should be sent first to the:
Which burden of proof has been applied when a workplace investigation has a 51 percent or greater certainty that allegations are true?
A statistical safety stock calculation would be appropriate for:
Payment Card Industry Data Security Standard (PCI DSS) allows for scanning a statistical sample of the environment without scanning the full environment. Scanning a statistical sample has many advantages and disadvantages.
Which of the following is the MOST accurate set of advantages and disadvantages?
A security consultant is working with an organization to help evaluate a proposal received from a new managed security service provider. There are questions about the confidentiality and effectiveness of the provider's system over a period of time. Which of the following System And Organization Controls (SOC) report types should the consultant request from the provider?
A third-party vendor is procured to conduct a non-financial audit. Which report evaluates the effectiveness of the controls?
An organization’s computer incident responses team PRIMARY responds to which type of control?
An organization is preparing to deploy Multi-Factor Authentication (MFA) to its workforce. The primary concerns of the organization are cost and security. The organization realizes that their entire workforce has computers and smartphones. Which of the following is BEST suited to address the organization's concerns?
What order BEST reflects the steps when adding threat modeling practices to a Software Development Life Cycle (SDLC)?
Which of the following represents the BEST metric when measuring the effectiveness of a security awareness program?
Asymmetric cryptography uses which type of key to encrypt data?
During a security incident investigation, a security analyst discovered an unauthorized module was compiled into an application package as part of the application assembly phase. This incident occurred immediately prior to being digitally signed and deployed using a deployment pipeline.
Which of the following security controls would BEST prevent this type of incident in the future?
Remote sensors have been deployed at a utility site to reduce overall response times for maintenance staff supporting critical infrastructure. Wireless communications are used to communicate with the remote sensors, as it is the most cost-effective method and minimizes risk to public health and safety. The utility organization has deployed a Host-Based Intrusion Prevention System (HIPS) to monitor and protect the sensors. Which statement BEST describes the risk that is mitigated by utilizing this security tool?
A consultant has been engaged to support the team in analyzing why the development of a new software product has slipped schedule by a year. The consultant discovered an increase of the functionality requirements due to the failure of the asset tracking program. Which of the following BEST describes which system lifecycle element is impacted?
Which of the following is a methodology for threat modeling in application?
A large volume of outbound Transmission Control Protocol (TCP) connections from the same source Internet Protocol (IP) address was observed at a satellite office firewall. Which of the following is the MOST likely explanation?
An organization is looking to integrate security concepts into the code development process early in development to detect issues before the software is launched. Which advantage does the organization gain from using Static Application Security Testing (SAST) techniques versus dynamic application security testing techniques?
In times of monetary inflation, which of the following methods of inventory valuation results in the greatest cost of sales for the early years of a particular product?
Which of the following Internet Protocol Security (IPSec) components provides the MOST confidentiality for the information that is being transmitted?
Which of the following can allow an attacker to bypass authentication?
Which of the following is the MOST important consideration in a full-scale disaster recovery test?
An organization donates used computer equipment to a non-profit group. A system administrator used a degausser on both the magnetic and Solid State Drives (SSD) before delivery. A volunteer at the non-profit group discovered some of the drives still contained readable data and alerted the system administrator. What is the BEST solution to ensure that computer equipment does not contain data before release?
An example of a flexibility metric for an organization Is:
Which of the following systems would be the most cost-efficient for inventory management of a low value item?
An organization currently has a network with 55,000 unique Internet Protocol (IP) addresses in their private Internet Protocol version 4 (IPv4) network range and has acquired another organization and must integrate their 25,000 endpoints with the existing, flat network topology. If subnetting is not implemented, which network class is implied for the organization’s resulting private network segment?
Which of the following is a system architecture in a data protection strategy?
Once an organization has identified and properly classified their information and data assets, policies and procedures are created to establish requirements for the handling, protection, retention, and disposal of those assets. Which solution is the BEST method to enforce data usage policies, discover sensitive data, monitor the use of sensitive data, and ensure regulatory compliance and intellectual property protection?
An advertising agency is working on a campaign for a prospective client. Competitors are working on a similar campaign and are interested in knowing what the firm has designed. What should the advertising agency do to BEST ensure intellectual property does not leave the organization?
A web developer was recently asked to create an organization portal that allows users to retrieve contacts from a popular social media platform using Hypertext Transfer Protocol Secure (HTTPS). Which of the following is BEST suited for authorizing the resource owner to the social media platform?
What document MOST likely states an organization’s values?
If all other factors remain the same, when finished goods inventory investment is increased, service levels typically will:
The most relevant measure of customer service performance Is:
After a recent threat modeling workshop, the organization has requested that the Chief Information Security Officer (CISO) implement zero trust (ZT) policies. What was the MOST likely threat identified in the workshop?
Which protocol is the BEST option to provide authentication, confidentiality, and data integrity between two applications?
An organization co-locates three divisions and merges them into one network infrastructure. Prior to the merge, the network manager issued devices to employees for remote login. What security concept should be observed to provide security when a device joins the network or when a client makes an Application Programming Interface (API) call?
Which of the following factors typically would distort a sales forecast that is based solely on shipment history?
An OpenID Connect (OIDC) authorization server received two requests from a client. The server identifies the request as replay attack and rejects the request. Which of the following BEST describes these requests?
An organization has decided to advance from qualitative risk assessment to quantitative risk analysis. The information security risk analyst has been tasked with replacing the organization’s qualitative likelihood scale of low, medium, and high with a quantitative approach. Which is the BEST approach for replacing the qualitative input values?
The primary consideration In maintenance, repair, and operating (MRO) supply systems typically is:
Which of the following actions provides the BEST evidence for forensic analysis of powered-off device?
An organization recently created a new accounting department, and that department is critical in the event of a disaster for the operations to continue. Which steps should the organization take to create a Business Continuity Plan (BCP)?
What is the MOST appropriate action to take when media classification needs to be downgraded to a less sensitive classification?
Which of the following capacity planning methods uses the master production schedule (MPS) as its primary input?
A financial institution is implementing an Information Technology (IT) asset management system. Which of the following capabilities is the MOST important to include?
A cybersecurity analyst is responsible for identifying potential security threats and vulnerabilities in the organization's software systems. Which action BEST demonstrates the understanding and application of threat modeling concepts and methodologies?
An information security professional is tasked with configuring full disk encryption on new hardware equipped with a Trusted Platform Module (TPM). How does TPM further enhance the security posture of full disk encryption if configured properly?
Which of the following is MOST important for an international retail company to consider when handling and retaining information about its customers?
A security team leader needs to communicate the value of the security program. As the security team leader determines the return on security investments, what is the MOST important aspect to incorporate?
Which of the following methods would be appropriate for forecasting the demand for a product family when there is a significant trend and seasonality in the demand history?
Which of the following planes directs the flow of data within a Software-Defined Networking (SDN) architecture?
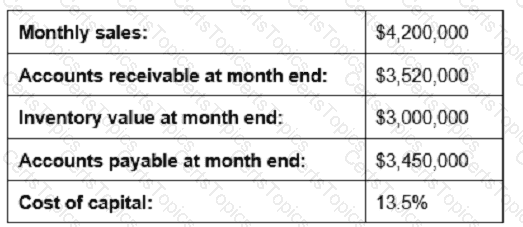
Given the information below, reducing which measure by 10% would contribute most to shortening the cash-to-cash cycle time?
Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
Which of the following BEST describes an individual modifying something the individual is not supposed to?
The question below is based on the following standard and actual data of a production order
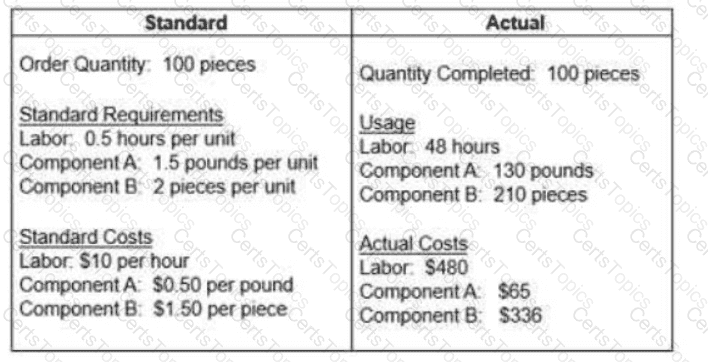
Which of the following statements about variances is true?
Which of the following BEST describes the responsibility of an information System Security Officer?
Employees at an organization use web based services provided by an affiliate. Which of the following risks is unique to this situation?
Improvements in an Input/output control (I/O control) system will most likely lead to:
Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
Given the following data, calculate the appropriate takt time:
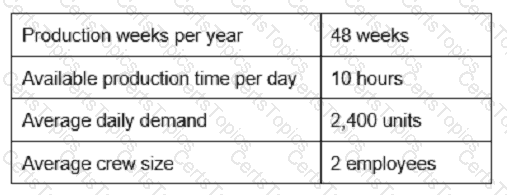
In a rapidly changing business environment, a primary advantage of an effective customer relationship management (CRM) program is:
Which of the following environments is most suitable for the use of kanban systems?
An organization experienced multiple compromises of endpoints, leading to breaches of systems and data. In updating its strategy to defend against these threats, which of the following BEST considers the organization’s needs?
An information system containing Protected Health Information (PHI) will be accessed by doctors, nurses, and others working in a hospital. The same application will be used by staff in the pharmacy department only for dispensing prescribed medication. Additionally, patients can log in to view medical history. The system owner needs to propose an access control model that considers environment, situation, compliance, and security policies while dynamically granting the required level of access. Which access control model is the MOST suitable?
An organization is considering options to outsource their Information Technology (IT) operations. Although they do not sell anything on the Internet, they have a strong requirement in uptime of their application. After evaluating the offerings received by the Cloud Service Provider (CSP), the IT manager decided it was mandatory to develop processes to continue operations without access to community or public cloud-based applications. Which of the following arguments MOST likely led the IT manager to make this decision?
An organization is transitioning from a traditional server-centric infrastructure to a cloud-based Infrastructure. Shortly after the transition, a major breach occurs to the organization's databases. In an Infrastructure As A Service (IaaS) model, who would be held responsible for the breach?
A security consultant is recommending the implementation of a security-focused Configuration Management (CM) process in an organization. What would be the BEST benefit the security consultant would include in the recommendation?
In choosing suppliers, a company wishes to maintain maximum leverage to reduce costs. Which of the following supply chain strategies would provide this opportunity?
Access Control Lists (ACL), protection bits, and file passwords are typical examples of which of the following access control methods?
An organization is preparing for a natural disaster, and management is creating a Disaster Recovery Plan (DRP). What is the BEST input for prioritizing the restoration of vital Information Technology (IT) services?
An information security professional is enhancing the organization's existing information security awareness program through educational posters. Which of the following is the MOST effective location for poster placement?
The question below is based on the following information:
Beginning inventory = 43Week 1Week 2Week 3
Forecast202020
Customer orders221710
Projected on-hand
Master production schedule (MPS)80
Available-to-promise (ATP)
What is the largest customer order that could be accepted for delivery at the end of week 3 without making changes to the master production schedule (MPS)?
Bad actors with little expense can easily make calls. Which social engineer strategy is a telecommunications ONLY risk concept?
What is the main negative effect of changing the due dates of open orders?
Which of the following concepts MOST accurately refers to an organization's ability to fully understand the health of the data in its system at every stage of the lifecycle?
Following the setting of an organization’s risk appetite by senior management, a risk manager needs to prioritize all identified risks for treatment. Each risk has been scored based on its Annualized Loss Expectancy (ALE). Management has asked for an immediate risk mitigation plan focusing on top risks. Which is the MOST effective approach for the risk manager to quickly present a proposal to management?
After a recent cybersecurity incident, a manufacturing organization is interested in further hardening its Identity and Access Management (IAM) solution. Knowing that the organization limits the use of personal devices in the facility, which could BEST be implemented to enhance the manufacturing organization's IAM solution?
Which of the following is a core subset of The Open Group Architecture Framework (TOGAF) enterprise architecture model?
An organization is planning to streamline its Identity and Access Management (IAM) processes and platform. The executive team mandated a compact platform to efficiently manage identities for internal and third-party services access. What is the BEST platform choice?
At which Open Systems Interconnection (OSI) layer does User Datagram Protocol (UDP) function?
An executive wants to ensure that risk related to information operations is managed in accordance with the enterprise's risk management thresholds. What is the BEST way to ensure this consistently occurs?
Which of the following describes the 3 MAIN roles of the identity-delegation model?
Up-to-date Information about production order status is required to do which of the following tasks?
The development team wants new commercial software to Integrate into the current systems. What steps can the security office take to ensure the software has no vulnerabilities?
A customer of a financial Institution denies that a transaction occurred. Which of the following is used to provide evidence evidence that the customer performed the transaction?
What MUST be completed before developing physical security controls?
A security engineer is implementing a Supervisory Control and Data Acquisition (SCADA) system.
What is the BEST action the engineer can take to ensure secure operations?
If fixed costs are §200,000 and 20,000 units are produced, a unit's fixed cost is §10. This is an example of:
What is the BEST way to plan for power disruptions when implementing a Disaster Recovery Plan (DRP)?
Which of the following provides for continuous improvement of the change control process?
What should an organization do to prepare for Disaster Recovery (DR) efforts?
When the discrete available-to-promise (ATP) method is used, the master production receipt quantity is committed to:
In restoring the entire corporate email system after a major outage and data loss, an email administrator reads a few email message exchanges between the human resources manager and a candidate for an open position. Which of the following BEST describes the behavior of the email administrator, and why?
A part is sold as a service part, and It is also used as a component In another part. Which of the following statements about the planning for this part is true?
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
A manufacturing facility uses common wireless technologies to communicate. The head of security is concerned about eavesdropping by attackers outside the perimeter fence. The distance between the facility and fence is at least 300 feet (100 m). Which of the following wireless technologies is MOST likely to be available to an attacker outside the fence?
An organization has a legacy application used in production. Security updates are no longer provided, which makes the legacy application vulnerable. The legacy application stores Social Security numbers and credit card numbers. Which actions will BEST reduce the risk?
An infrastructure team is setting up a wireless network for employees at a new location of the organization that is located near a very busy city transport hub. Which should be the MOST important antenna consideration with regard to securing the wireless network for the infrastructure team?
An order winner during the growth stage of a product's life cycle is:
An external audit is conducted on an organization's cloud Information Technology (IT) infrastructure. This organization has been using cloud IT services for several years, but its use is not regulated in any way by the organization and security audits have never been conducted in the past. Which task will be the MOST challenging to conduct an effective security audit?
What is the MOST beneficial principle of threat modeling?
A security practitioner notices that workforce members retain access to information systems after transferring to new roles within the organization, which could lead to unauthorized changes to the information systems.
This is a direct violation of which common security model?
When starting an external benchmarking study, a firm must first:
Objective security metrics tend to be easier to gather, easier to interpret, and easier to include in reports to management.
What is the BEST objective metric for the effectiveness of a security awareness training?
How would a master production schedule (MPS) be used In an assemble-to-order (ATO) manufacturing environment?
Which security audit phase is MOST important to ensure correct controls are applied to classified data in a production environment?
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
Which of the following BEST describes how an Application Programming Interface (API) gateway fits into an application architecture?
If organizational leadership determines that its required continuous monitoring plan is too costly for the organization, what action should be taken by leadership and the Authorizing Official (AO)?
What is the BEST reason to include a Hardware Security Module (HSM) in the key management system when securing cloud storage?
An audit of antivirus server reports shows a number of workstations do not have current signatures installed. The organization security standard requires all systems to have current antivirus signatures. What distinct part of the audit finding did the auditor fail to include?
What is the MOST effective way to begin a risk assessment?
Which of the following planning modules considers the shortest-range planning goals?
An organization has a requirement that all documents must be auditable and that the original is never modified once created. When designing the system, what security model MUST be implemented in order to meet this requirement?
Exhibit:
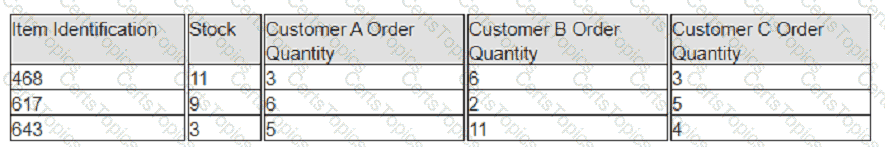
A company has prioritized customers A, B, and C, filling orders in that sequence. What are the impacts to customer service levels for customers B and C?
The trade-off of increasing safety stock to improve customer fill rate would be a decrease in:
What General Data Protection Regulation (GDPR) principle says that data should be collected lawfully and with the person’s consent?
Which of the following prioritization rules will have the greatest impact In reducing the number of orders In queue?
A disadvantage of a capacity-lagging strategy may be:
A company is having trouble with raw material deliveries and has decided to develop a supplier certification program. The certification process most appropriately would start with which of the following suppliers?
Which of the following states of data becomes MOST important to protect as organizations continue to transition toward Application Programming Interface (API)-based solutions?
Which Open Systems Interconnection (OSI) layer is concerned with Denial-Of-Service (DoS) SYN flood attacks?
A multinational organization acquires a subsidiary. The acquisition results in the need to integrate a large population of new users into the organization's corporate cloud. What is the MAIN benefit of the organization's Federated Identity Management (FIM) system to address the need?
Endpoint security needs to be established after an organization procured 1,000 industrial Internet Of Things (IoT) sensors. Which of the following challenges are the security engineers MOST likely to face?
Internet Small Computer Systems Interface (iSCSI) protocol relies on Transmission Control Protocol/Internet Protocol (TCP/IP). Which can be used maliciously to interrupt the flow of data. Which Information Technology (IT) component would be impacted by such a disruption?
Typically, rough-cut capacity planning (RCCP) in a job shop environment would review which of the following work centers to determine the ability to execute the plan?
An effective approach to projecting requirements for materials with long lead times Includes which of the following options?
A forecasting method that responds slowly to changes in demand would be most appropriate when the historical demand pattern shows a:
Which of the following is a disadvantage of using federated identity?
During an investigation, a forensic analyst executed a task to allow for the authentication of all documents, data, and objects collected, if required. Which of the options below BEST describes this task?
Cloud computing introduces the concept of the shared responsibility model. This model can MOST accurately be described as defining shared responsibility between which of the following?
An organization is attempting to address the security risk introduced by employees writing down door entry passcodes. Which of the following security measures BEST mitigates this risk?
A security analyst has been asked to build a data retention policy for a hospital. What is the FIRST action that needs to be performed in building this policy?
An organization is restructuring its network architecture in which system administrators from the corporate office need to be able to connect to the branch office to perform various system maintenance activities. What network architecture would be MOST secure?
An organization has integrated its enterprise resource planning system into its centralized Identity and Access Management (IAM) system to automate provisioning of access. A security audit revealed that privileged access granted within the ERP system is not visible in the IAM system. Which of the following controls BEST mitigates this risk?
An organizational policy requires that any data from organization-issued devices be securely destroyed before disposal. Which method provides the BEST assurance of data destruction?
A security analyst modifies the organization’s baselines to align the controls more closely with specific security and privacy requirements. Which security concept is this an example of?
A cloud-based web application requires the use of cryptographic keys to encrypt user-uploaded files at rest. Where is the safest place to store these cryptographic keys?
An organization’s computer incident response team PRIMARILY responds to which type of control?
Check sheets can be used to:
Which of the following is the BEST activity to mitigate risk from ransomware on mobile devices and removable media in a corporate environment?
What are the FIRST two steps an organization should conduct to classify its assets?
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
Which of the following should be done FIRST when implementing an Identity and Access Management (IAM) solution?
The Chief Information Security Officer (CISO) for an international organization with offices operating globally has been tasked with developing a new data encryption policy that can be applied to all areas of the business. What is the MOST important factor that must be considered?
Zombieload, Meltdown, Spectre, and Fallout are all names of bugs that utilized which of the following types of attack?
During the initiation phase of a project to acquire a customer relation management system, what is the FIRST step a project team will take for early integration of security?
What is an important countermeasure to consider when hardening network devices and servers to reduce the effectiveness of unauthorized network scanning?
Which role is MOST accountable for allocating security function resources in order to initiate the information security governance and risk management policy?
A plant uses a level production strategy due to the high costs of hiring and letting go of skilled employees. The constrained resource is due to be upgraded in the fourth month of the planning horizon, and that will reduce capacity for that month by 17%.
Which of the following actions would be appropriate in this situation to maintain current levels of customer service and gross margin?
Which of the following measurements indicates there may be bias In the forecast model?
Which of the following benefits typically will be realized when switching from a functional to a cellular layout?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
What is the BEST item to consider when designing security for information systems?
Which Virtual Private Network (VPN) protocol provides a built-in encryption?
What is the PRIMARY secure protocol used by a Content Delivery Network (CDN)?
What priority control technique is most appropriate for a firm using a cellular production system?
An organization provides customer call center operations for major financial service organizations around the world. As part of a long-term strategy, the organization plans to add healthcare clients to the portfolio. In preparation for contract negotiations with new clients, to which cybersecurity framework(s) should the security team ensure the organization adhere?
A company’s Marketing and Sales departments have identified an opportunity to develop a new market for a product family and requested an increase in the production plan. Which of the following actions would be most appropriate to account for the new market opportunity?