Marketing has requested a significant change in the mix for a product family. The requested change falls between the demand and the planning time fences. The most appropriate action by the master scheduler is to:
Which of the following BEST describes an individual modifying something the individual is not supposed to?
The question below is based on the following standard and actual data of a production order
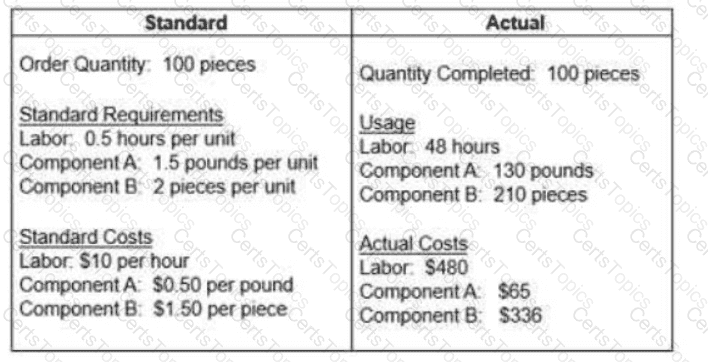
Which of the following statements about variances is true?
Which of the following BEST describes the responsibility of an information System Security Officer?