A SysOps Administrator is managing a web application that runs on Amazon EC2 instances behind an ELB Application Load Balancer (ALB). The instances run in an EC2 Auto Scaling group. The administrator wants to set an alarm for when all target instances associated with the ALB are unhealthy.
Which condition should be used with the alarm?
An organization has decided to consolidate storage and move all of its backups and archives to Amazon S3. With all of the data gathered into a hierarchy under a single directory, the organization determines there is 70 TB data that needs to be uploaded. The organization currently has a 150-Mbps connection with 10 people working at the location.
Which service would be the MOST efficient way to transfer this data to Amazon S3?
A SysOps Administrator has created an Amazon EC2 instance using an AWS CloudFormation template in the us-east-1 Region. The Administrator finds that this template has failed to create an EC2 instance in the uswest-2 Region.
What is one cause for this failure?
A sysops administrator is reviewing AWS Trusted Advisor warnings and encounters a warning for an S3 bucket policy that has open access permissions. While discussing the issue with the bucket owner, the administrator realizes the S3 bucket is an origin for an Amazon CloudFront web distribution.
A company’s application stores documents within an Amazon S3 bucket. The application is running on Amazon EC2 in a VPC. A recent change in security requirements states that traffic between the company’s application and the S3 bucket must never leave the Amazon network.
What AWS feature can provide this functionality?
A company is planning to deploy multiple ecommerce websites across the eu-west-1, ap-east-1, and us-west-1 Regions. The websites consist of Amazon S3 buckets Amazon EC2 instances, Amazon RDS databases and Elastic Load Balancers.
Which method will accomplish the deployment with the LEAST amount of effort?
A company has mandated the use of multi-factor authentication (MFA) for all 1AM users, and requires users to make all API calls using the CLI. However, users are not prompted to enter MFA tokens, and are able to run CLI commands without MFA. In an attempt to enforce MFA. the company attached an 1AM policy to all users that denies API calls that have not been authenticated with MFA.
What additional step must be taken to ensure that API calls are authenticated using MFA?
A company’s website went down for several hours. The root cause was a full disk on one of the company’s Amazon EC2 instances.
Which steps should the SysOps Administrator take to prevent this from happening in this future?
An application is running on Amazon EC2 Instances behind an Application Load Balancer (ALB). An operations team wants to be notified in near-teal time when the ALB has issues connecting to backend EC2 instances.
Which solution will meet these requirements with the LEAST amount of effort?
A medical imaging company needs lo process large amounts of imaging data in real time using a specific instance type. The company wants to guarantee sufficient resource capacity for 1 year
Which action will meet these requirements in the MOST cost-effective manner?
A company runs an Amazon RDS MySQL DB instance. Corporate policy requires that a daily backup of the database must be copied to a separate security account.
What is the MOST cost-effective way to meet this requirement?
A company wants to icrease the availability and vulnerability of a critical business application. The appliation currently ueses a MySQL database running on an Amazon EC2 instance. The company wants to minimize application changes.
How should the company these requirements?
A company has adopted a security policy that requires all customer data to be encrypted at rest. Currently, customer data is stored on a central Amazon EFS file system and accessed by a number of different applications from Amazon EC2 instances.
How can the SysOps Administrator ensure that all customer data stored on the EFS file system meets the new requirement?
An organization has developed a new memory-intensive application that is deployed to a large Amazon EC2 Linux fleet. There is concern about potential memory exhaustion, so the Development team wants to monitor memory usage by using Amazon CloudWatch.
What is the MOST efficient way to accomplish this goal?
A company has received a notification in its AWS Personal Health Dashboard that one of its Amazon EBS-backed Amazon EC2 instances is on hardware that is scheduled maintenance The instance runs a critical production workload that must be available during normal business hours
Which steps will ensure that the instance maintenance does not produce an outage?
A SysOps Administrator is troubleshooting an AWS CloudFormation template whereby multiple Amazon EC2 instances are being created. The template is working in us-east-1, but it is failing in us-west-2 with the error code:
AMI [ami-12345678] does not exist.
How should the Administrator ensure that the AWS CloudFormation template is working in every region?
A SysOps Administrator is attempting to use AWS Systems Manager Session Manager to initiate a SSH session with an Amazon EC2 instance running on a custom Linux Amazon Machine Image (AMI) The Administrator cannot find the target instance in the Session Manager console
Which combination of actions with solve this issue? (Select TWO )
A SysOps Administrator created an AWS CloudFormation template for the first time. The stack failed with a status of ROLLBACK_COMPLETE. The Administrator identified and resolved the template issue causing the failure.
How should the Administrator continue with the stack deployment?
A financial service company is running distributed computing software to manage a fleet of 20 servers for their calculations. There are 2 control nodes and 18 worker nodes to run the calculations. Worker nodes can be automatically started by the control nodes when required. Currently, all nodes are running on demand, and the worker nodes are uses for approximately 4 hours each day.
Which combination of actions will be most cost-effective? (Select Two)
A company has an application running on a fleet of Microsoft Windows instances. Patches to the operating system need to be applied each month. AWS Systems Manager Patch Manager is used to apply the patches on a schedule.
When the fleet is being patched, customers complain about delayed service responses.
What can be done to ensure patches are deployed with MINIMAL customer impact?
A company has attached the following policy to an IAM user.
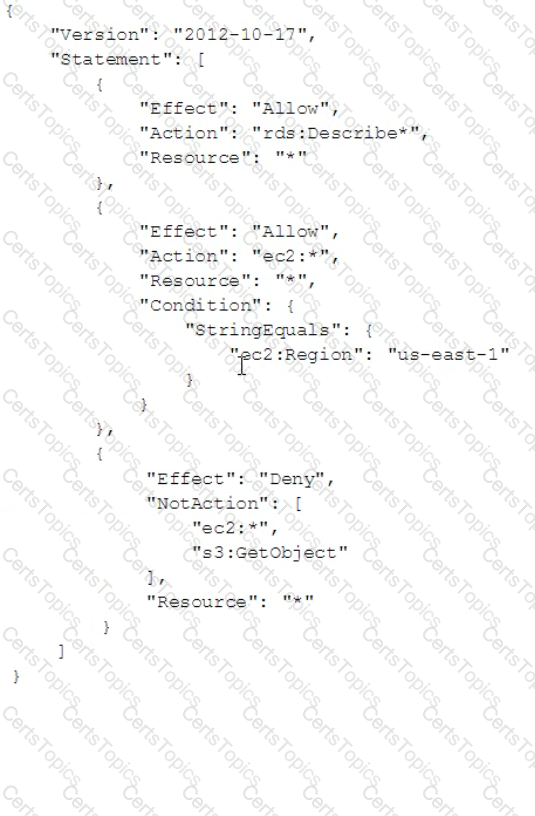
What of the following actions are allowed for the IAM user?
A company has deployed a NAT instance to allow web servers to obtain software updates from the internet. There latency on the NAT instance as the network grows. A SysOps Administrator needs to reduce latency on the instance in a manner that a efficient, cost effective, and allow for scaling with future demand.
Which action should be taken to accomplish this?
A SysOps Administrator needs to retrieve a file from the GLACIER storage class of Amazon S3. the Administrator wants to receive an amazon SNS notification when the file is available for access.
What action should be taken to accomplish this?
A Development team is designing an application that processes sensitive information within a hybrid deployment. The team needs to ensure the application data is protected both in transit and at rest.
Which combination of actions should be taken to accomplish this? (Choose two.)
A company needs to deploy a web application on two Amazon EC2 instances behind an Application Load Balancer (ALB). Two EC2 instances will also be deployed to host the database. The infrastructure needs to be designed across Availability Zones for high availability and must limit public access to the instances as much as possible.
How should this be achieved within a VPC?
An ecommerce site is using Amazon ElastiCache with Memcached to store session state for a web application and to cache frequently used data. For the last month, users have been complaining about performance. The metric data for the Amazon EC2 instances and the Amazon RDS instance appear normal, but the eviction count metrics are high.
What should be done to address this issue and improve performance?
A company has a multi-tier web application. In the web tier, all the servers are in private subnets inside a VPC. The development team wants to make changes to the application that requires access to Amazon S3.
What should be done to accomplish this?
A SysOps Administrator is maintaining an application that runs on Amazon EC2 instances behind an application Load Balancer (ALB). Users are reporting errors when attempting to launch the application. The administrator notices an increase in the httpcode_ELS_5xx_Count Amazon CloudWatch metric for the load balancer.
What is the possible cause for this increase?
A SysOps administrator notices a scale-out event for an Amazon EC2 Auto Scaling group Amazon CloudWatch shows a spike in the RequestCount metric tor the associated Application Load Balancer The administrator would like to know the IP addresses for the source of the requests
Where can the administrator find this information?
An application is being developed that will be served across a fleet of Amazon EC2 instances, which require a consistent view of persistent data. Items stored vary in size from 1 KB lo 300MB; the items are read frequently, created occasionally, and often require partial changes without conflict. The data store is not expected to grow beyond 2TB. and items will be expired according to age and content type.
Which AWS service solution meets these requirements?
An application running on Amazon EC2 allows users to launch batch jobs for data analysis. The jobs are run asynchronously, and the user is notified when they are complete. While multiple jobs can run concurrently, a user’s request need not be fulfilled for up to 24 hours. To run a job, the application launches an additional EC2 instance that performs all the analytics calculations. A job takes between 75 and 110 minutes to complete and cannot be interrupted.
What is the MOST cost-effective way to run this workload?
A SysOps Administrator noticed that the cache hit ratio for an Amazon CloudFront distribution is less than 10%. Which collection of configuration changes will increase the cache hit ratio for the distribution? (Select two.)
The Security team has decided that there will be no public internet access to HTTP (TCP port 80) because if it is moving to HTTPS for all incoming web traffic. The team has asked a SysOps Administrator to provide a report on any security groups that are not compliant.
What should the SysOps Administrator do to provide near real-time compliance reporting?
A SysOps Administrator has configured a CloudWatch agent to send custom metrics to Amazon CloudWatch and is now assembling a CloudWatch dashboard to display these metrics.
What steps should be the Administrator take to complete this task?
A company is managing a website with a global user base hosted on Amazon EC2 with an Application Load Balancer (ALB). To reduce the load on the web servers, a SysOps administrator configures an Amazon CloudFront distribution with the ALB as the origin After a week of monitoring the solution, the administrator notices that requests are still being served by the ALB and there is no change in the web server load.
What are possible causes tor this problem? (Select TWO.)
A company is using AWS Storage Gateway to create block storage volumes and mount them as Internet Small Computer Systems Interlace (iSCSI) devices from on-premise! servers As the Storage Gateway has taken on several new projects some of the Development teams report that the performance of the iSCSI drives has degraded. When checking the Amazon CloudWatch metrics a SysOps Administrator notices that the cachePercentUsed metric is below 60% and the cachePercentUsed metric is above 90%.
What steps should the Administrator take to increase Storage Gateway performance?
A company has a web application that runs both on-premises and on Amazon EC2 instances. Over time both the on-premises servers and EC2 instances begin crashing A sysops administrator suspects a memory leak in the application and wants a unified method to monitor memory utilization over time.
How can the Administrator track both the EC2 memory utilization and on-premises server memory utilization over time?
The Security team at AnyCompany discovers that some employees have been using individual AWS accounts that are not under the control of AnyCompany. The team has requested that those individual accounts be linked to the central organization using AWS Organizations.
Which action should a SysOps Administrator take to accomplish this?
A company's application infrastructure was deployed using AWS CloudFormation and is composed of Amazon EC2 instances behind an Application Load Balancer. The instances run an EC2 Auto Scaling group across multiple Availability Zones. When releasing a new version of the application, the update deployment must avoid DNS changes and allow rollback.
Which solution should a sysops administrator use to meet the deployment requirements for this new release?