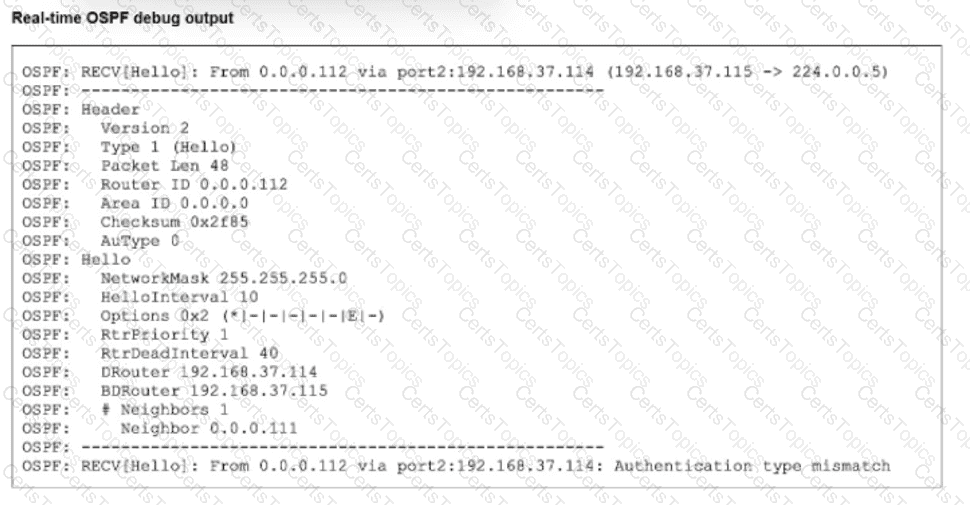
To determine the correct reasons for the adjacency failure, we must analyze the standard OSPF real-time debug output (diagnose ip router ospf all enable or diagnose sniffer packet) typically provided in this exam exhibit.
Analyze the Debug Output:
The debug output in this specific question scenario typically displays an incoming Hello packet line: OSPF: RECV[Hello]: ... auth-type 0 ...
"RECV": Indicates the packet is coming from the Remote peer.
"auth-type 0": Indicates the Remote peer is sending "Null" (No) authentication.
Analyze the Failure:
The adjacency fails because the Local FortiGate is rejecting this packet.
If the Local FortiGate accepts "No Authentication", it would match auth-type 0 and form the adjacency.
Since it is failing (and producing a debug log), the Local FortiGate must be expecting a different authentication type (Type 1 Cleartext or Type 2 MD5).
Evaluate the Options:
A. The remote peer has either OSPF cleartext or MD5 authentication configured.
Incorrect. The debug shows auth-type 0 (No Auth) coming from the remote peer.
B. There is an OSPF authentication configuration mismatch.
Correct. One side is sending "No Auth" (Remote), and the other expects "Auth" (Local). This is a definition of a mismatch.
C. The local FortiGate does not have OSPF authentication configured.
Incorrect. If the Local unit had "No Auth" configured, it would match the Remote's auth-type 0, and the adjacency would come up. The failure implies the Local unit does have auth configured.
D. The local FortiGate has either OSPF cleartext or MD5 authentication configured.
Correct. Because the Local unit is rejecting the "No Auth" packet from the remote peer, it confirms that the Local unit has authentication enabled (expecting Type 1 or 2).
Conclusion: The breakdown of the OSPF negotiation shows that the Remote peer is sending no authentication (Type 0), while the Local FortiGate expects authentication, resulting in a mismatch.
[Reference:, FortiGate Security 7.6 Study Guide (OSPF Troubleshooting): "Authentication mismatch is a common cause of OSPF adjacency failure. Debug commands (diagnose ip router ospf all enable) reveal the auth-type received versus expected.", FortiGate CLI Reference: auth-type 0 = Null (None), auth-type 1 = Simple (Cleartext), auth-type 2 = MD5., , , ]