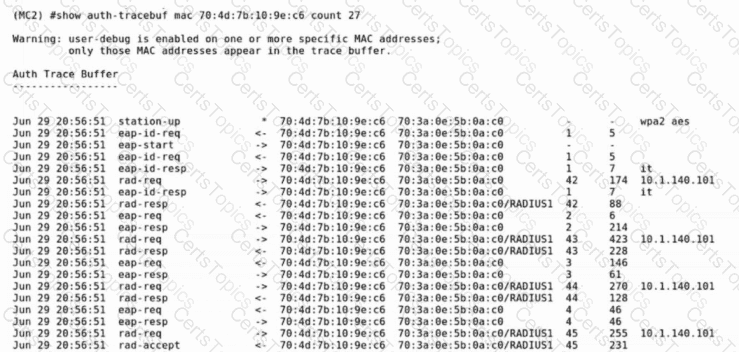
The provided output is from the command:
(MC2) #show auth-tracebuf mac
This command traces the authentication exchange between the access point (or mobility controller) and the RADIUS server for a specific client. The trace provides insight into the 802.1X authentication sequence and RADIUS responses.
From the exhibit:
eap-id-req
eap-id-resp
eap-req
eap-resp
eap-success
These messages clearly indicate that an 802.1X (EAP-based) authentication took place. MAC authentication (MAB) or WebAuth would not include multiple EAP identity and response messages.
RADIUS Messages:
rad-req, rad-resp, rad-accept from /RADIUS1
The presence of rad-accept indicates successful authentication.
Exact extract from ArubaOS (AOS-S/AOS 10 WLAN Authentication Guide):
“When the trace output shows EAP identity requests, EAP responses, and a RADIUS Access-Accept message, the authentication method in use is 802.1X (EAP-based user authentication). The presence of EAP-Success following the Access-Accept confirms successful 802.1X authentication.”
Follow-on WPA2 Key Exchange:
Lines show wpa2-key1, wpa2-key2, wpa2-key3, and wpa2-key4.
This sequence occurs after 802.1X authentication completes and is used to establish encryption keys for a WPA2 Enterprise session.
Exact extract from Aruba WLAN Troubleshooting Guide:
“After successful 802.1X authentication (EAP-Success), the controller exchanges four WPA2 keys with the station to derive the session keys used for data encryption. This confirms WPA2-Enterprise with 802.1X was used.”
No Indication of MAC or WebAuth:
MAC authentication would show mac-auth or macauth messages instead of eap-id-req/resp.
WebAuth involves HTTP-based redirection and is not visible in auth-tracebuf as EAP transactions.
Exact extract:
“MAC authentication shows ‘macauth start’ and ‘macauth accept’ entries, not EAPOL frames. WebAuth authentication uses a web redirect and does not appear as EAP frames in the trace buffer.”
Therefore, the trace confirms a WPA2-Enterprise 802.1X user authentication, where the user’s credentials were validated by the RADIUS server, followed by the WPA2 key handshake.
Why the Other Options Are Incorrect:
A. MAC authentication:Would show MAC-based request/response entries (macauth), not eap-id-req/resp.
C. WEBauth authentication:WebAuth occurs over HTTP/HTTPS and does not involve EAP messages; thus, no eap-id or eap-success would be seen.
D. 802.1X machine authentication:Machine authentication occurs before user logon and is typically identified in logs by a computer account (e.g., host/computername$). Here, the username and context indicate a user-level session.
References of HPE Aruba Networking Switching Documents or Study Guide:
ArubaOS 8/10 WLAN Authentication and Security Configuration Guide – “802.1X EAP Authentication and Trace Analysis.”
Aruba WLAN Troubleshooting Guide – “Using show auth-tracebuf to validate EAP authentication.”
Aruba Campus Wireless Design Fundamentals – “Understanding WPA2-Enterprise authentication flow (EAPOL, RADIUS, WPA2 4-Way Handshake).”
Aruba Access Security and AAA Implementation Guide – “Distinguishing between MAC, WebAuth, and 802.1X authentication in debug outputs.”