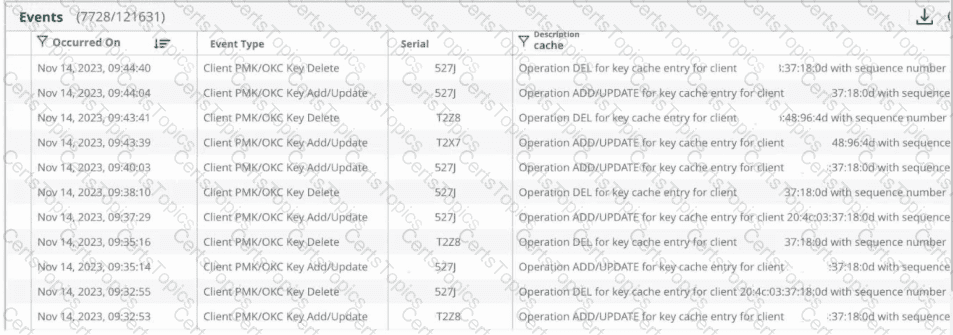
The provided event logs from Aruba Central show multiple entries of:
Client PMK/OKC Key Add/Update
Client PMK/OKC Key Delete
Operation ADD/UPDATE for key cache entry for client ...
Operation DEL for key cache entry for client ...
These log entries refer to Pairwise Master Key (PMK) and Opportunistic Key Caching (OKC) updates in the Aruba gateway or access point for wireless clients.
When a client roams between APs or the system refreshes key entries for active clients, Aruba’s infrastructure updates or deletes PMK cache entries dynamically. This process ensures secure key continuity across APs and controllers for tunneled SSIDs.
Exact Extracts from Aruba WLAN and AOS-10 Documentation:
“PMK/OKC cache updates and deletions are part of normal operation. When clients connect, disconnect, or roam, the system adds or removes their PMK cache entries. These log messages are informational and indicate expected WPA2-Enterprise behavior.”
“In a tunneled SSID, PMK and OKC entries are managed at the gateway level. When a client roams or rekeys, the gateway logs PMK/OKC Key Add/Update and Key Delete messages. These are not error conditions.”
“Frequent ADD/DEL entries for a client MAC address reflect normal WPA2 key lifecycle events—such as reauthentication, idle timeout, or client-driven disassociation.”
Thus, these messages indicate normal background key management (PMK caching and rekeying) and not any fault or attack scenario.
Why the Other Options Are Incorrect:
A. Denial-of-Service attack:False. These events correspond to key management, not excessive connection requests. Aruba security logs for DoS attacks show messages like “Association flood” or “Authentication flood,” not PMK/OKC operations.
B. Roaming issue:While OKC relates to roaming optimizations, these log messages do not indicate a failure or issue — they show successful key caching updates.
“OKC Key Add/Update events confirm successful key caching, not roaming failure.”
C. Client WLAN driver issue:No error messages (timeouts, EAP failures, or deauths) are logged. The presence of PMK updates and deletes alone does not imply a driver issue.
“Client driver problems typically manifest as association failures or 4-way handshake errors, not PMK cache logs.”
Conclusion:
The repeated “PMK/OKC Key Add/Update” and “Key Delete” events represent routine client key caching and refresh behavior in Aruba’s tunneled WLAN design.
No misconfiguration, client issue, or attack is implied.
Therefore, the correct answer is:
✅ D. This is normal, expected behavior. No further actions are needed.
References of HPE Aruba Networking Switching Documents or Study Guide:
Aruba WLAN Troubleshooting and Operations Guide – “Understanding PMK/OKC key lifecycle and expected log events.”
Aruba Campus WLAN Best Practices Guide – “Tunneled SSID key management (PMK, OKC, and 802.11r Fast Roaming).”
Aruba Central Monitoring and Event Logs Reference – “Client PMK/OKC Key Add/Delete informational messages.”