An analyst is reviewing system logs while threat hunting:
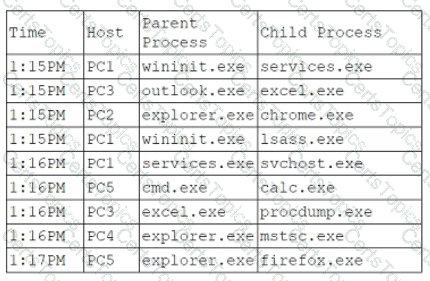
Which of the following hosts should be investigated first?
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system, application, or user base is affected by an uptime availability outage?
Which of the following would help an analyst to quickly find out whether the IP address in a SIEM alert is a known-malicious IP address?
An incident responder was able to recover a binary file through the network traffic. The binary file was also found in some machines with anomalous behavior. Which of the following processes most likely can be performed to understand the purpose of the binary file?