A security analyst reviews a packet capture and identifies the following output as anomalous:
13:49:57.553161 TP10.203.10.17.45701>10.203.10.22.12930:Flags[FPU],seq108331482,win1024,urg0,length0
13:49:57.553162 IP10.203.10.17.45701>10.203.10.22.48968:Flags[FPU],seq108331482,win1024,urg0,length0
...
Which of the following activities explains the output?
A web application has a function to retrieve content from an internal URL to identify CSRF attacks in the logs. The security analyst is building a regular expression that will filter out the correctly formatted requests. The target URL is and the receiving API only accepts GET requests and uses a single integer argument named "id." Which of the following regular expressions should the analyst use to achieve the objective?
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
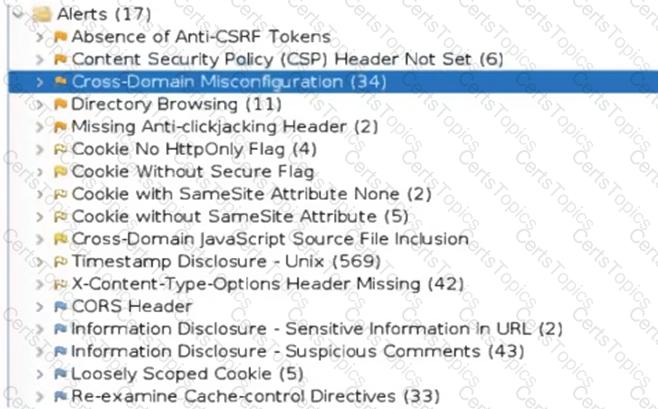
Which of the following tuning recommendations should the security analyst share?